MGCI CTF - Practice
Looking for some CTF’s to solve I found a CTF platform(https://ctfmgci.jonathanw.dev/) that hosts some practice challenges in order to warmup before the real contest.
In this blog post I will guide you through the General and Web challenges and show you my methodology in order to solve them.
General Category
Back to School ‘21 - Keys and Flags
Proof of Flag
ctf{h0W_t0_Su8m1T}
Summary
In this challenge you just need to read the description and submit the flag.
Proof of Solve
While Aaron was thinking of a potential lore for a problem he wanted to set, he came across a key that had the characters ctf{h0W_t0_Su8m1T} on it. If only he knew what it opened…Back to School ‘21 - Curses
Proof of Flag
ctf{wh4T_th3_F0cK}
Summary
In this challenge you are given a .zip file. Once extracted you will find a strange file called curses.txt that contains a strange string:
└─$ cat curses.txt
(( !!^ !)@ !@# !!( !)$ %@ *$ (% !!^ !)$ %! (% &) $* (( &% !@%Proof of Solve
Using dcode.fr cipher identifier I was able to find that this strange string is called keyboard-change-cipher.
Now in order to decipher this we will use: https://www.dcode.fr/keyboard-change-cipher
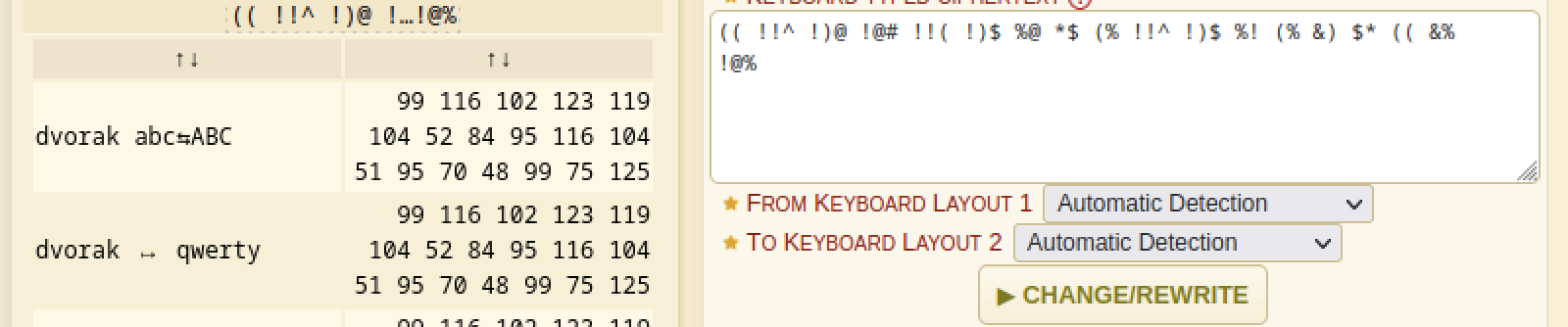
We see that this decodes into a list of decimal numbers which presumably this would be the flag. Now in order to decode this we could use CyberChef(https://gchq.github.io/CyberChef/#recipe=From_Decimal('Space',false)&input=OTkgMTE2IDEwMiAxMjMgMTE5IDEwNCA1MiA4NCA5NSAxMTYgMTA0IDUxIDk1IDcwIDQ4IDk5IDc1IDEyNQ) or write a quick script in python:
#!/usr/bin/env python3
enc_flag = [99, 116, 102, 123, 119, 104, 52, 84, 95, 116, 104, 51, 95, 70, 48, 99, 75, 125]
for enc_char in enc_flag:
print(chr(enc_char), end="")File Extensions 1
Proof of Flag
ctf{fileextensionsarejustacrutch}
Summary
In this challenge you are given a .zip file that contains a strange .txt file.
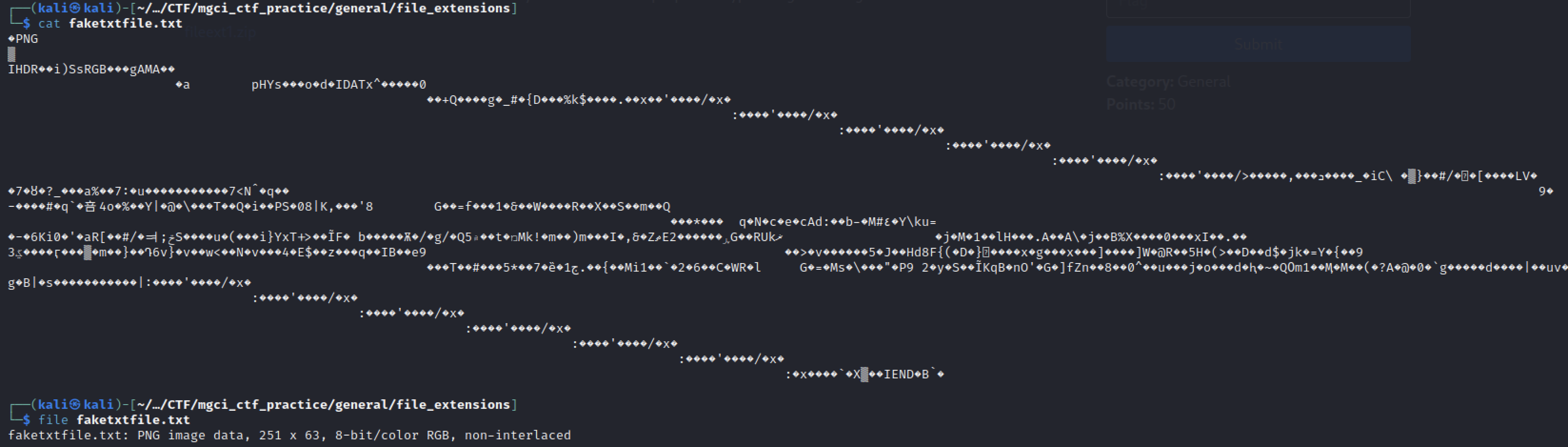
By just running a simple command as file on this file we can see that this is actually a PNG file.
Proof of Solve
So in order to view the image and get the flag we will just need to mv faketxtfile.txt fake.png and view the image.
In order o extract the flag faster we could write a python OCR script that will automatically write the flag:
from PIL import Image
from pytesseract import pytesseract
path_to_tesseract = r'C:\Program Files\Tesseract-OCR\tesseract.exe'
path_to_image = './fake.png'
pytesseract.tesseract_cmd = path_to_tesseract
img = Image.open(path_to_image)
text = pytesseract.image_to_string(img)
print(text)Or you could use an online OCR: https://www.newocr.com/
File Extensions 2
Proof of Flag
Summary
As the previous challenge we get a strange file. So starting to analyze it we can see that it’s actually a Windows Binary Executable.
└─$ file Weirdfile
Weirdfile: PE32+ executable (console) x86-64, for MS Windows, 17 sections
-------------------------------------------------------------------------
┌──(kali㉿kali)-[~/…/CTF/mgci_ctf_practice/general/file_extensions_two]
└─$ xxd Weirdfile| head
00000000: 4d5a 9000 0300 0000 0400 0000 ffff 0000 MZ..............
00000010: b800 0000 0000 0000 4000 0000 0000 0000 ........@.......
00000020: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000030: 0000 0000 0000 0000 0000 0000 8000 0000 ................
00000040: 0e1f ba0e 00b4 09cd 21b8 014c cd21 5468 ........!..L.!Th
00000050: 6973 2070 726f 6772 616d 2063 616e 6e6f is program canno
00000060: 7420 6265 2072 756e 2069 6e20 444f 5320 t be run in DOS
00000070: 6d6f 6465 2e0d 0d0a 2400 0000 0000 0000 mode....$.......
00000080: 5045 0000 6486 1100 1f1b 7b61 00de 0300 PE..d.....{a....
00000090: c505 0000 f000 2700 0b02 0221 001e 0000 ......'....!....Proof of Solve
We will change the file to mv Weirdfile weird.exe and try to execute it using wine because we can’t execute by default .exe files on linux.
└─$ wine weird.exe
ctf{notanimageshhhhh}MGCTF ‘20 October - General
Proof of Flag
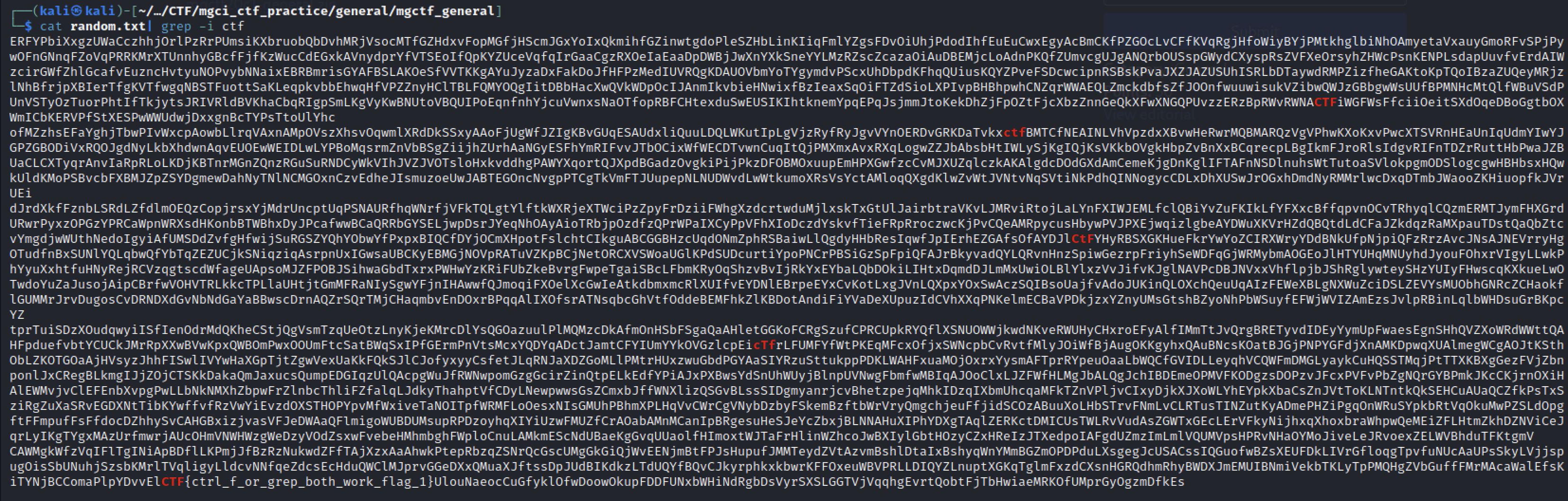
CTF{ctrl_f_or_grep_both_work_flag_1}
Summary
In this challenge we are given a .zip file that contains a .txt file that haves lot’s of strings similar to base64 encoded strings.
Proof of Flag
In order to solve this challenge you just need to cat the file and search for the flag.
MGCTF ‘20 October - General (Hard)
Proof of Flag
CTF{congrats_linux_user_flag_two}
Summary
You are given a .zip file that contains a linux executable:
└─$ file LinuxExecutable
LinuxExecutable: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=a92d2af7a3148ae89aaf8afb8495c272e6a511aa, not stripped
---------------------------------------------------------------------------
┌──(kali㉿kali)-[~/…/CTF/mgci_ctf_practice/general/mgctf_general_hard]
└─$ xxd LinuxExecutable| head
00000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............
00000010: 0300 3e00 0100 0000 a005 0000 0000 0000 ..>.............
00000020: 4000 0000 0000 0000 7019 0000 0000 0000 @.......p.......
00000030: 0000 0000 4000 3800 0900 4000 1d00 1c00 ....@.8...@.....
00000040: 0600 0000 0400 0000 4000 0000 0000 0000 ........@.......
00000050: 4000 0000 0000 0000 4000 0000 0000 0000 @.......@.......
00000060: f801 0000 0000 0000 f801 0000 0000 0000 ................
00000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................
00000080: 3802 0000 0000 0000 3802 0000 0000 0000 8.......8.......
00000090: 3802 0000 0000 0000 1c00 0000 0000 0000 8...............Proof of Solve
In order to solve this challenge you just need to chmod +x LinuxExecutable, run the binary and get the flag:
└─$ ./LinuxExecutable
CTF{congrats_linux_user_flag_two}MGCTF ‘20 October - Git
Proof of Flag
CTF{you_found_me_git_flag_1}
Summary
You are given a .zip file that contains a .git directory.
Proof of Solve
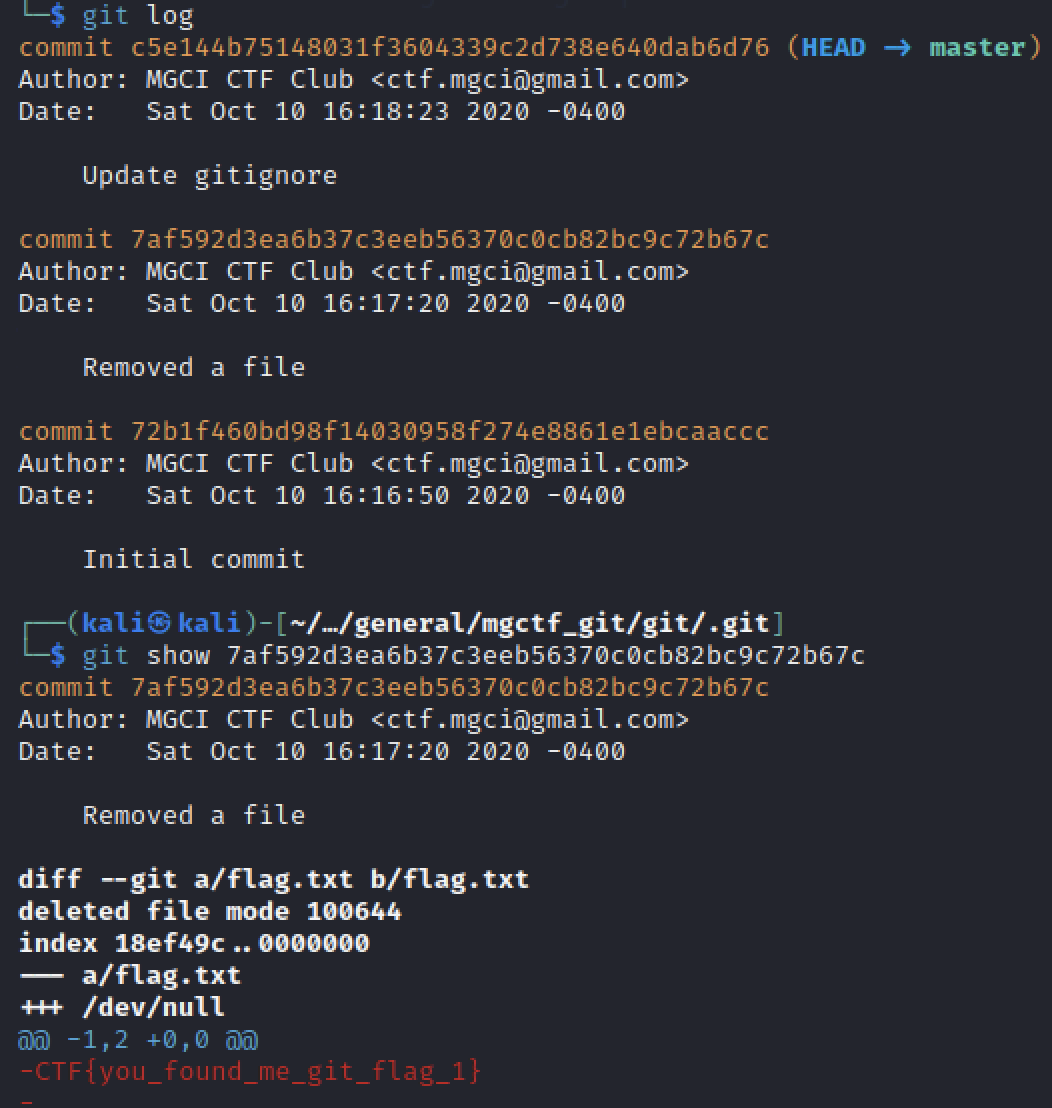
Looking at tthe .git folder we can see a .gitignore file that contains the following text:
└─$ cat ../.gitignore
# We cannot let any more flag files slip through
flag.txtThis indicates us that somewhere there should be a flag.
So I started to look at the git logs and found an interesting commit saying that a file was removed:
MGCTF ‘20 October - Git (Hard)
Proof of Flag
CTF{maybe_the_repo_was_a_red_herring_flag_2}
Summary
As the previous challenge we get a .git directory where we need to find the flag.
Proof of Solve
When trying to unzip the folder the unzip command showed us something interesting:
└─$ unzip mgctf20c1-githard.zip
Archive: mgctf20c1-githard.zip
inflating: README.md
creating: .git/
creating: .git/tree/
inflating: .git/tree/0e.txt
inflating: .git/description
creating: .git/info/
inflating: .git/info/exclude
inflating: .git/config
inflating: .git/HEAD
inflating: .git/COMMIT_EDITMSG
creating: .git/refs/
creating: .git/refs/tags/
[...]We can see a file called 0e.txt that normally shouldn’t be there. So when we try to read the file we got the flag:
└─$ cat tree/0e.txt
CTF{maybe_the_repo_was_a_red_herring_flag_2}MGCTF ‘20 Winter - Problem 0 - Sanity Check
Proof of Flag
CTF{everything_works}
Summary
Because this is just a sanity check the flag is present in the description of the challenge.
Proof of Solve
Let's make sure that everything is working on your end and our end.
Your flag is: CTF{everything_works}MGCTF ‘20 Winter - Problem 1 - Coal for Christmas
Proof of Flag
CTF{7a88bc2d4fb96f00fb13a44f27b8e8bf}
Summary
This is a UNIX command and file’s exercise where you just need to create a list of files and then md5sum the listing of the directory.
Proof of Solve
└─$ touch coal lotsofcoal morecoal somecoal somemorecoal && ls | md5sum
7a88bc2d4fb96f00fb13a44f27b8e8bf -Web Category
Back to School ‘21 - Comments
Proof of Flag
ctf{htmlcommentsnotdisplayed}
Summary
In this challenge you get an website with some text on it. Based on the challenge name we need to look on the source code of the application in order to find the flag.
Proof of Solve
└─$ curl -XGET https://dev.jonathanw.dev/index.html | grep ctf
<!-- ctf{htmlcommentsnotdisplayed} -->Back to School ‘21 - Files
Proof of Flag
ctf{urlencodingveryuseful}
Summary
We get a .zip file containing the web application source code:
from flask import *
import html
app = Flask(__name__)
app.config["SECRET_KEY"] = "thesecret" # only required for flashing anyways
@app.route('/')
def home():
url = request.full_path
if '?' not in url or 'file' not in request.args:
return render_template('index.html')
# Parse the request arguments
try:
params = [(e.split('=')[0], html.unescape(e.split('=')[1])) for e in url[url.index('?')+1:].split('&')]
except Exception:
flash('Hey, stop trying to break the server! That is not nice!')
return render_template('index.html')
# Block file=flag.txt but other files are fine
for item in params:
if 'file' in item[0]:
if 'flag.txt' in item[1]:
flash('Blocked!')
return render_template('index.html')
else:
break
if request.args['file'] == 'flag.txt':
return send_from_directory('.', 'flag.txt')
else:
flash('Sorry, but that file does not exist.')
return render_template('index.html')Proof of Solve
We can see that there is a filter on the flag.txt but there isn’t any check if the file is url encoded.
So we will encode flag.txt: flag%2Etxt
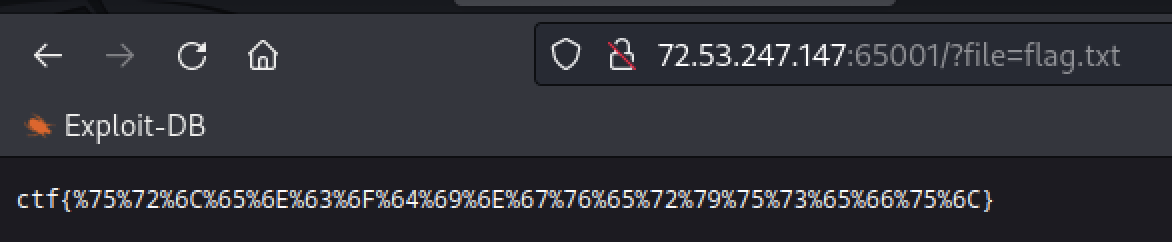
Now in order to get the real flag we just need to URL Decode it and get the flag.
Hello, World! (part 2)
Proof of Flag
CTF{welcome_to_inspect_element}
Summary
Trying to solve the challenge we can see that don’t have any webserver endpoint:
So I started to look on the source code of the application and found an interesting endpoint: https://ctfmgci.jonathanw.dev/api/problem?id=helloworld2
Proof of Solve
Trying to access this endpoint give us the flag:
CTF{welcome_to_inspect_element}MGCI-WLMAC Joint CTF Contest ‘21 - Hidden In Plain Sight
Proof of Flag
CTF{UnD3rY0UrN053}
Summary
You can solve this challenge the same as the previous one.
Proof of Solve
Access the endpoint and retrieve the flag by viewing the source code of the application.